The Good | DOJ Seizes $15B in Crypto, Targets Global Scam Ring & PowerSchool Hacker
The U.S. Department of Justice has seized $15 billion in bitcoin from the Prince Group, a vast criminal syndicate behind cryptocurrency scams known as romance baiting. Led by fugitive Chen Zhi (aka Vincent), the group defrauded billions from victims through fake investment schemes disguised as romantic or business opportunities. Operating across 30+ countries, Prince Group forced trafficked workers into Cambodian compounds to run these scams under threat of violence.
The organization laundered illicit gains through complex crypto transfers before converting them into cash for luxury assets, including yachts, jets, and even a Picasso painting. In coordination with the U.K., the U.S. Treasury has sanctioned Zhi and 146 of his associates. Authorities, on the whole, estimate that Americans lost $16.6 billion to such scams last year, with Southeast Asian-based operations driving most of this increase. As global authorities intensify crackdowns on large-scale fraud and cybercrime operations, U.S. law enforcement continues to pursue domestic offenders exploiting digital platforms for profit.
Matthew D. Lane, a 19-year-old from Massachusetts, was sentenced to four years in prison and ordered to pay $14 million in restitution for orchestrating a severe cyberattack on PowerSchool, a leading K–12 software provider serving over 60 million students worldwide. Lane and his accomplices used stolen subcontractor credentials to breach PowerSchool’s systems, stealing data on 9.5 million teachers and 62.4 million students, including social security numbers and medical records. They demanded $2.85 million in Bitcoin under the alias “Shiny Hunters”.

Despite PowerSchool paying an undisclosed ransom to prevent a data leak, the group continued additional extortion attempts on several affected school districts. Lane pleaded guilty to multiple federal cybercrime charges in May.
The Bad | North Korean Hackers Deploy EtherHiding to Steal Cryptocurrency
North Korean state-sponsored hackers have begun using a novel malware-hosting method called “EtherHiding” to steal cryptocurrency, marking the first time a nation-state actor has employed this blockchain-based technique. Researchers attribute the activity to the DPRK-linked cluster UNC5342, which has been deploying EtherHiding since February 2025 as part of its ongoing “Contagious Interview” campaign. The group uses fake job offers to lure software developers, posing as recruiters from fake companies. During technical assessments, victims are tricked into running malicious code, initiating the multi-stage infection chains.
EtherHiding embeds malicious payloads within smart contracts on public blockchains, including Ethereum and Binance Smart Chain, allowing attackers to fetch the malware via read-only calls that leave no trace of the transaction. This method provides anonymity, is resilient to takedowns, and provides the flexibility to update payloads at minimal cost, an average of $1.37 USD per update. The payloads include JADESNOW, a JavaScript downloader, and InvisibleFerret, a backdoor for credential theft, remote control, and exfiltration of cryptocurrency wallet data and browser-stored passwords.
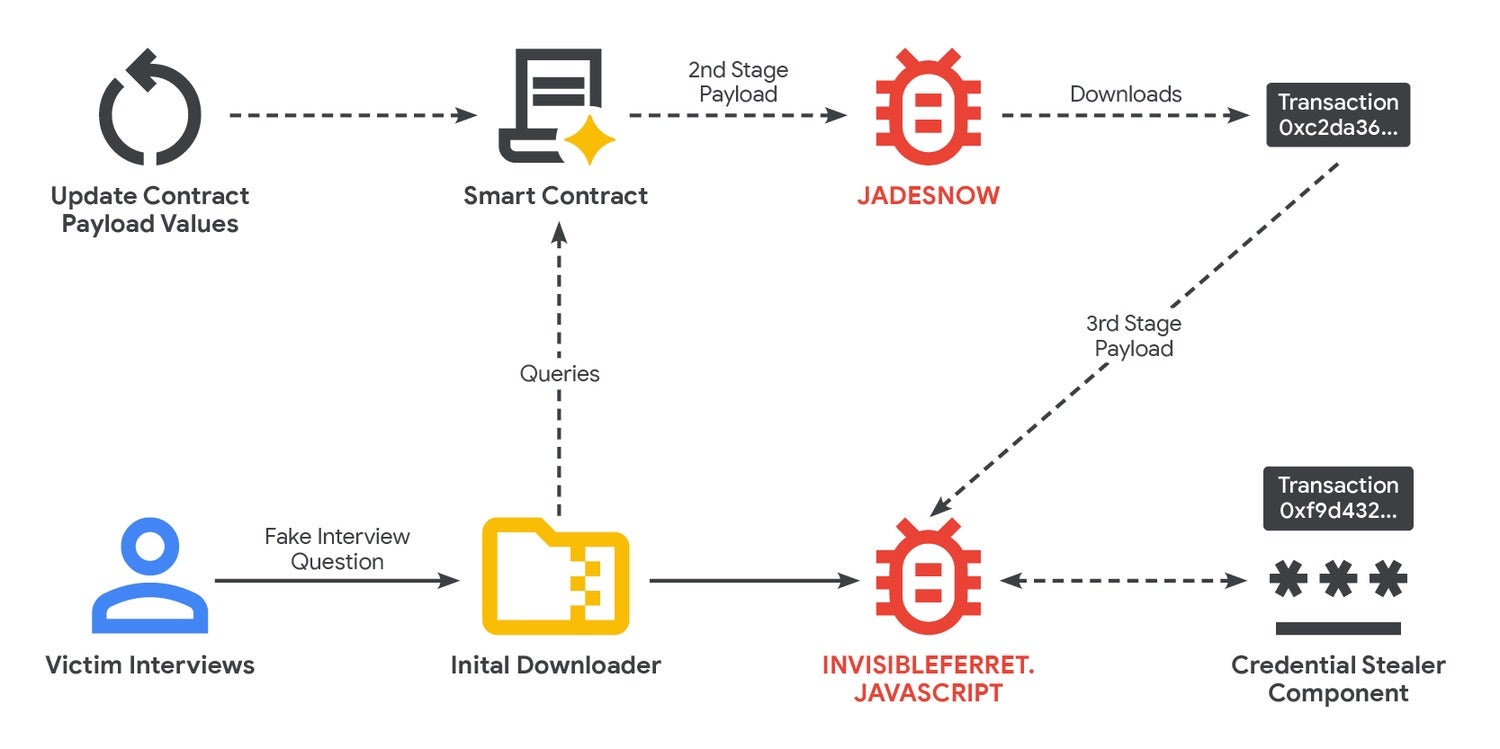
Researchers note that the threat actor’s use of multiple blockchains suggests operational compartmentalization and makes forensic analysis more difficult. The approach demonstrates a shift toward bulletproof hosting, using blockchain technology to create takedown-resistant, flexible malware distribution.
Users should exercise caution with job-related downloads and adopt best practices such as testing files in isolated environments, restricting executable file types, and enforcing strict browser policies to block script auto-execution.
The Ugly | Flaws in Microsoft Defender Could Lead to Theft of Data
Researchers have reported unpatched vulnerabilities in Microsoft Defender for Endpoint (DFE) that could enable attackers to bypass authentication, spoof data, exfiltrate sensitive information, and inject malicious files into forensic evidence collections used by security analysts.
Reported to Microsoft’s Security Response Center in July 2025, the issues were categorized as low severity, with no confirmed fixes as of this writing. Researchers tracking the flaws focused on how the agent communicated with cloud backends, using tools like Burp Suite and WinDbg memory patches to bypass certificate pinning in MsSense.exe and SenseIR.exe, allowing plaintext interception of HTTPS traffic, including Azure Blob uploads.
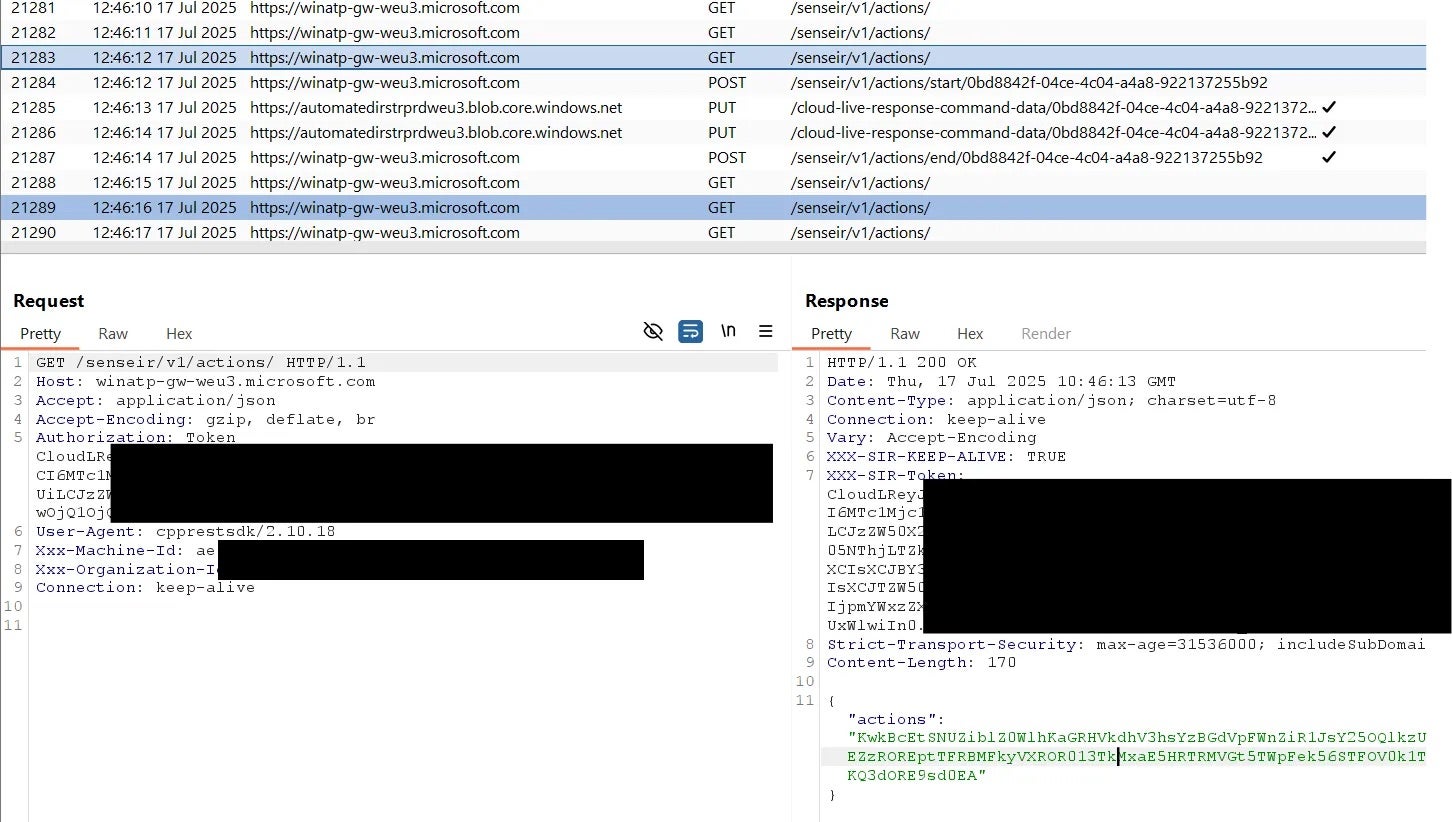
The core problem lies in DFE requests to endpoints such as /edr/commands/cnc and /senseir/v1/actions/, where Authorization tokens and headers are ignored. Low-privileged users can obtain machine and tenant IDs from the registry to impersonate the agent, intercept commands, or spoof responses such as faking an “already isolated” status while leaving devices exposed. Similarly, CloudLR tokens for Live Response and Automated Investigations are ignored, allowing payload manipulation and uploads to Azure Blob URIs.
In addition, attackers can access 8MB configuration dumps without credentials, revealing detection logic like RegistryMonitoringConfiguration and ASR rules, while investigation packages on disk can be tampered with, embedding malicious files disguised as legitimate artifacts.
Despite responsible disclosure by the researchers concerned, it remains unknown whether Microsoft will patch the flaws any time soon.


