The Good | UK Convicts “Bitcoin Queen” in World’s Largest Cryptocurrency Seizure
This week, a court in the UK convicted Bitcoin fraudster Qian Zhimin (aka Zhang Yadi) of acquiring and possessing criminal property after a 7 year pursuit and the recovery of stolen crypto assets now worth $7.3 billion.
Qian, a 47 year old Chinese national, had profited from a multibillion dollar fraud scheme between 2014 and 2017, in which she convinced around 130,000 unwitting victims to invest in “digital gold” by promising returns of 100-300%.
Dubbed “the Bitcoin Queen”, Qian fled from China to the UK using a false passport after authorities began investigating her in 2017. She then attempted to launder her funds through an accomplice, Wen Jian, a 42 year old female who facilitated the purchase of property, jewellery and other high value assets on Qian’s behalf.

In 2018, authorities seized a number of digital devices from Qian and Wen’s London home, but it was not until 2021 that they realized the devices contained digital wallets holding 61,000 Bitcoin, worth at that time around a billion dollars. Wen was subsequently arrested in 2022 and convicted in 2024. Qian remained at large until her arrest in April 2024. Qian’s sentencing has been set for next month.
What happens to the seized funds remains the subject of some controversy since the value of the Bitcoin now far exceeds that of the funds invested by victims. Both the UK government and representatives of the Chinese victims are seeking restitution.
The Bad | Hackers Exploit Milesight Routers to Send Phishing SMS to Users
New research suggests that multiple threat actors may be leveraging an unpatched bug in Milesight cellular routers, targeting users in a number of different countries with SMS phishing messages (aka Smishing) since at least 2022. A patch for the flaw, CVE-2023-43261, was released in 2023, but analysis suggests many unpatched devices remain accessible from the public internet.
The researchers say that attackers have been exploiting the vulnerable routers to send large volumes of SMS messages mimicking government services, banks and delivery companies. Victims receive legitimate looking texts urging them to click malicious links, which redirect to mobile-optimized phishing pages.
The attack is made possible as the flaw allows anyone to access log messages on the exposed routers via API calls. The logs contain encrypted administrator credentials which attackers can decrypt using hardcoded AES keys found in the client-side JavaScript and then use these credentials to authenticate further API calls.
The researchers also believe other bugs may be in play as they noted evidence that many exposed devices were running outdated firmware with other known vulnerabilities.
Analysis of the targeted phone numbers indicates that Europe is the primary region affected by the smishing campaigns, with Belgium heavily targeted; however, vulnerable devices were also observed in Australia, Turkey, Singapore and even North America. In one of a number of campaigns, SMS lures using the domain disney[.]plus-billing[.]sbs and referencing a payment issue urged recipients to click a malicious link.
Phishing messages in several languages, including French, Italian and English, were observed. The researchers believe multiple campaigns have been in operation by different threat actor groups targeting the same vulnerable infrastructure.
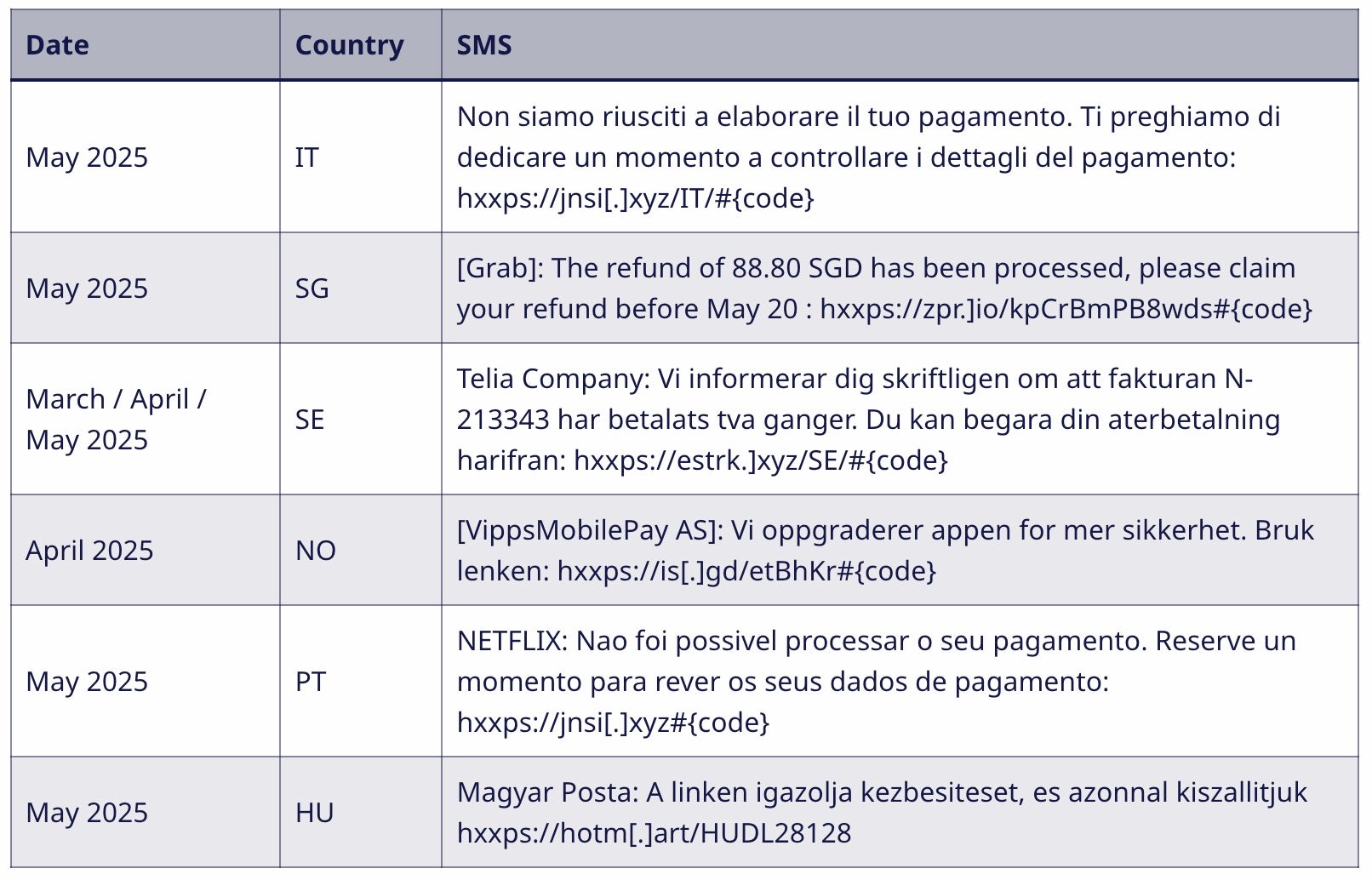
Vulnerable cellular routers offer an attractive target to threat actors, affording them the ability to send messages at scale without being flagged as malicious. Individuals and businesses are reminded that, as with other forms of phishing, heightened awareness and scepticism towards unsolicited SMS messages, even when they appear to come from trusted sources, is a vital first line of defense.
The Ugly | Trio of Flaws in Google Gemini Turn AI Into Attack Vehicle
AI is in the spotlight again this week with news that several products within Google’s family of AI models were vulnerable to search injection attacks, prompt injection attacks and exfiltration of user data, leading researchers to dub the flaws the ‘Gemini Trifecta’.
The flaws were found in Google Cloud Platform’s Gemini Cloud Assist, Gemini Search Personalization, and Gemini Browsing Tool, and serve as a reminder of the risks that AI brings to enteprises as threat actors look to manipulate such tools in their attacks. The researchers say they discovered three distinct components in the Gemini suite that had issues:
- Gemini Cloud Assist — This prompt-injection vulnerability in Google Cloud’s Gemini Cloud Assist tool could have enabled attackers to exploit cloud-based services, potentially compromising cloud resources, and also could have allowed phishing attempts. This vulnerability represents a new attack class in the cloud and in general, where log injections can poison AI inputs with arbitrary prompt injections
- Gemini Search Personalization Model — This search-injection vulnerability gave attackers the ability to inject prompts, control Gemini’s behavior and potentially leak the user’s saved information and location data by manipulating their Chrome search history
- Gemini Browsing Tool — This flaw allowed attackers to exfiltrate a user’s saved information and location data by abusing the browsing tool, potentially putting user privacy at risk.
The vulnerabilities were reported to Google and have now been patched. However, it is important that enterprises view AI assistants not just as passive productivity tools but as active attack surfaces and treat them accordingly.


