The Good | DoJ Charges $100M Fraud Ring & Seizes $1M in Crypto from BlackSuit Ransomware
The DoJ has charged four Ghanaian nationals, Isaac Oduro Boateng (aka “Kofi Boat”), Inusah Ahmed (aka “Pascal”), Derrick Van Yeboah (aka “Van”), and Patrick Kwame Asare (aka “Borgar”), for their roles in a $100 million fraud scheme involving romance scams and business email compromise (BEC) attacks. All four defendants allegedly belonged to a major crime ring operating globally from 2016 to 2023 and focused on targeting U.S. companies and vulnerable individuals, particularly vulnerable senior citizens who live alone.
Combining fake romance scams, spoofed emails, and forged wire transfer authorization letters, they tricked victims into wiring funds to U.S.-based contacts, who then laundered the proceeds for West African ‘chairmen’ – members of the fraud ring stationed in West Africa. Boateng and Ahmed were identified as ringleaders, while Yeboah focused on romance scams. The charges carry potential sentences of up to 20 years for each major offense.
The DoJ has also seized $1,091,453 in cryptocurrency from the BlackSuit ransomware group, tracing the funds as criminals moved them across multiple exchanges to hide their origins. The seized amount was part of a 49.3 Bitcoin ransom (worth $1.45M at the time) paid on April 4, 2023, for a decryptor. The action followed the June 2024 collection of key evidence and came soon after “Operation Checkmate”, which took down BlackSuit’s dark web extortion portals.
This week, the DOJ announced coordinated actions against the BlackSuit (Royal) ransomware group, including the takedown of servers and domains and the seizure of virtual currency. The disruption was coordinated by the FBI, @DHSgov, @SecretService, @IRS_CI and international law… pic.twitter.com/DHtSeGzlRo
— FBI (@FBI) August 14, 2025
BlackSuit, linked to Royal, Quantum, and Chaos ransomware, has been tied to over 450 attacks across U.S. critical sectors and has amassed $370M in ransom payments combined. Authorities emphasize that seizing illicit funds remains a critical component to disrupting ransomware operations, in particular hindering how actors can use their funds to maintain or rebuild infrastructure and recruit new affiliates and members.
The Bad | Cyberespionage Group Targets Georgia and Moldova with Stealthy MucorAgent Backdoor
Seemingly aligned with Russian geopolitical interests, ‘Curly COMrades’ are targeting government and judicial bodies in Georgia as well as energy firms in Moldova. The new cyberespionage group first emerged mid-last year and is known to use a custom three-stage .NET backdoor dubbed ‘MucorAgent’, which is capable of executing AES-encrypted PowerShell scripts and uploading results to a command and control (C2) server. The name derives from heavy use of curl.exe for exfiltration and COM object hijacking.
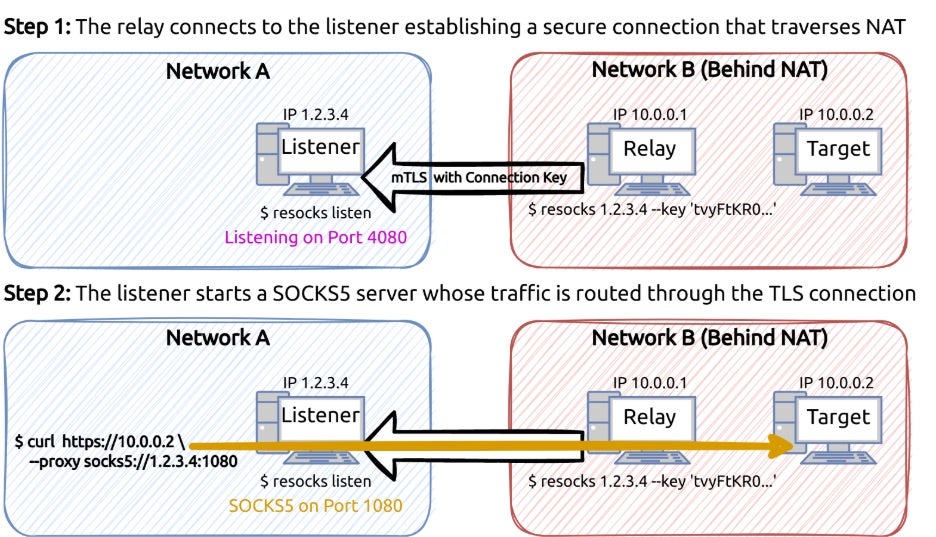
Curly COMrades achieve persistence through an uncommon method. First, it hijacks class identifiers (CLSIDs) that zero in on a Windows’ Native Image Generator (NGEN) component via a seemingly inactive scheduled task. The task runs unpredictably during idle times or system changes. Additional tools include the Go-based Resocks proxy, custom SOCKS5 servers, SSH with Stunnel, and CurlCat for obfuscated traffic relayed through compromised sites.
The group has also been observed installing legitimate remote access tools like Remote Utilities (RuRat) and commercial RMM software for interactive control. MucorAgent bypasses Windows’ Antimalware Scan Interface (AMSI), retrieves encrypted payloads disguised as PNG files, and harvests credentials by attempting NTDS database extractions and LSASS dumps. Curly COMrades implements dynamic command scheduling within MucorAgent, using in-memory decryption for secondary payloads and leveraging obfuscated .NET reflection to execute injected code, minimizing footprint and evading static analysis detection. Network reconnaissance relied on living-off-the-land binaries (netstat, wmic, ipconfig) and PowerShell AD enumeration.
While Curly COMrades employs stealthy techniques, open-source tools, and legitimate utilities to blend with normal activity, their operations generate detectable signals picked up by XDR platforms. Currently, cyber researchers suggest the attacks are part of a larger espionage campaign focused on persistence, credential theft, and data exfiltration.
The Ugly | New “MadeYouReset” Attack Technique Exploits HTTP/2 Flaw to Bypass DoS Protections
Cyber researchers have disclosed ‘MadeYouReset’, a new HTTP/2 attack technique (CVE-2025-8671) capable of bypassing the standard 100 concurrent request limit per TCP connection. This enables attackers to send thousands of requests and trigger powerful denial-of-service (DoS) conditions for legitimate users and vendors. In some implementations, the flaw can escalate to out-of-memory crashes. Affected products include Apache Tomcat (CVE-2025-48989), F5 BIG-IP (CVE-2025-54500), and Netty (CVE-2025-55163).
MadeYouReset is the latest flaw to affect HTTP/2 and builds on earlier Rapid Reset attacks (CVE-2023-44487) and its mitigations. It works by abusing the HTTP/2 RST_STREAM mechanism (used for both client cancellations and error signaling) without sending an RST_STREAM frame directly. Attackers send valid requests, then trigger carefully timed protocol violations that force the server to reset the stream while still processing the backend response. This approach bypasses Rapid Reset protections while achieving similar disruption.
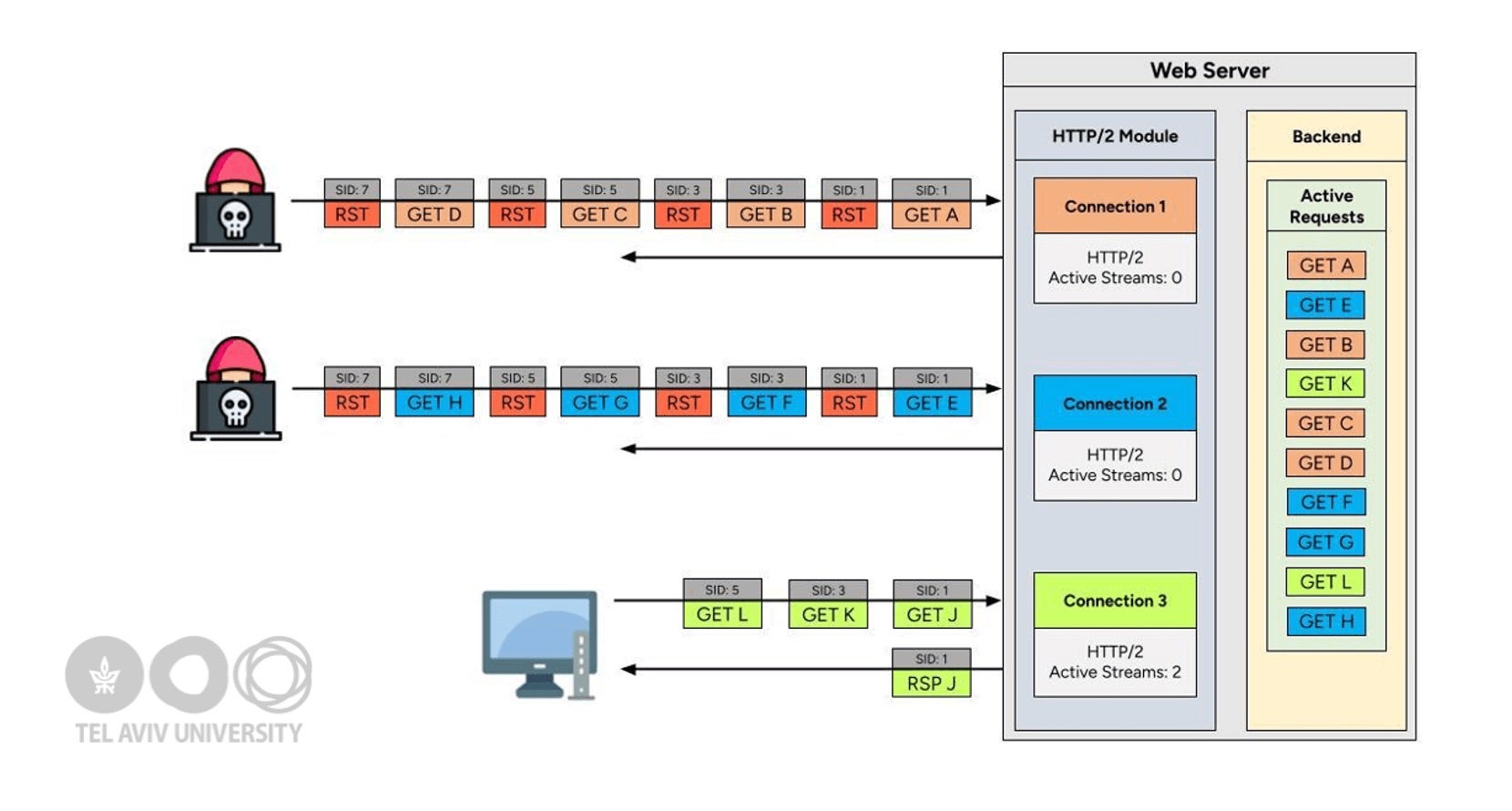
Six crafted primitives can induce server resets, such as invalid WINDOW_UPDATE or PRIORITY frames, frames with illegal lengths or self-dependencies, and HEADERS or DATA frames sent after the stream is closed. The technique exploits mismatches between HTTP/2 specifications and actual server architectures, leading to resource exhaustion.
According to CERT Coordination Center (CERT/CC), this vulnerability stems from server-triggered Rapid Reset behaviors, allowing attackers to overwhelm server resources and deny service to legitimate users. Researchers also warn that MadeYouReset highlights the growing complexity of protocol abuse and the need for defenses against subtle, specification-compliant exploits.
Given HTTP/2’s critical role in web infrastructure, researchers stress that patching affected products and refining protocol-level defenses is essential to prevent large-scale exploitation of this emerging threat.


