The Good | DoJ Charges “IntelBroker” Cyberattacker Responsible for $25M in Data Theft
A British national linked to a series of globally-reaching, high-impact data breaches has been formally charged by U.S. authorities. Kai West, 25, is accused of operating under the alias “IntelBroker” and orchestrating cyberattacks that led to an estimated $25 million in damages across government agencies, corporations, and critical infrastructure.

According to the indictment unsealed by the U.S. Attorney’s Office for the Southern District of New York, West engaged in a multi-year campaign to exfiltrate and sell sensitive data, including health records and proprietary corporate information. This data was then routed and trafficked on BreachForums, a well-known underground marketplace where West also served as an administrator.
The FBI identified West through a combination of undercover purchases, cryptocurrency tracing, and forensic analysis of associated online accounts. Investigators linked the transactions and email activity to a Ramp banking account registered in West’s name, ultimately confirming his identity as IntelBroker.
West has been charged with conspiracy to commit computer intrusions, conspiracy to commit wire fraud, wire fraud, and unauthorized access to protected systems. Several of these offenses carry maximum penalties of up to 25 years in prison. He was arrested in France in February 2025, and the United States is seeking his extradition.
These actions come alongside the arrest of four additional individuals in France allegedly responsible for operating BreachForums. West’s arrest highlights the growing effectiveness of law enforcement in identifying and dismantling cybercrime networks, no matter how globally dispersed they are.
The Bad | APT28 Abuses Signal in New Malware Campaign Targeting Ukraine
Ukraine’s Computer and Emergency Response (CERT-UA) has attributed a new malware campaign to Russian-based state-sponsored group APT28 (also tracked as UAC-0001). The campaign abuses messaging platform Signal as a trusted vector to distribute malicious documents to Ukrainian government entities. This tactic marked another evolution in APT28’s cyberespionage operations.
The latest attacks work by delivering a macro-enabled Word document via Signal (Акт.doc), which deployed a multi-stage infection chain. This chain includes the use of Covenant, a memory-resident loader, that fetches a malicious DLL and a WAV file containing shellcode. These ultimately load BeardShell, a previously undocumented C++ malware capable of decrypting and executing PowerShell payloads, before exfiltrating results via the Icedrive API.
BeardShell achieves persistence through COM-hijacking in the Windows registry, highlighting the campaign’s evasion strategy. In earlier variants of the attack from last year, APT28 also deployed SlimAgent, a malware tool designed to grab encrypted screenshots via Windows API calls such as BitBlt, CreateCompatibleDC, CreateCompatibleBitmap, EnumDisplayMonitors, and GdipSaveImageToStream.
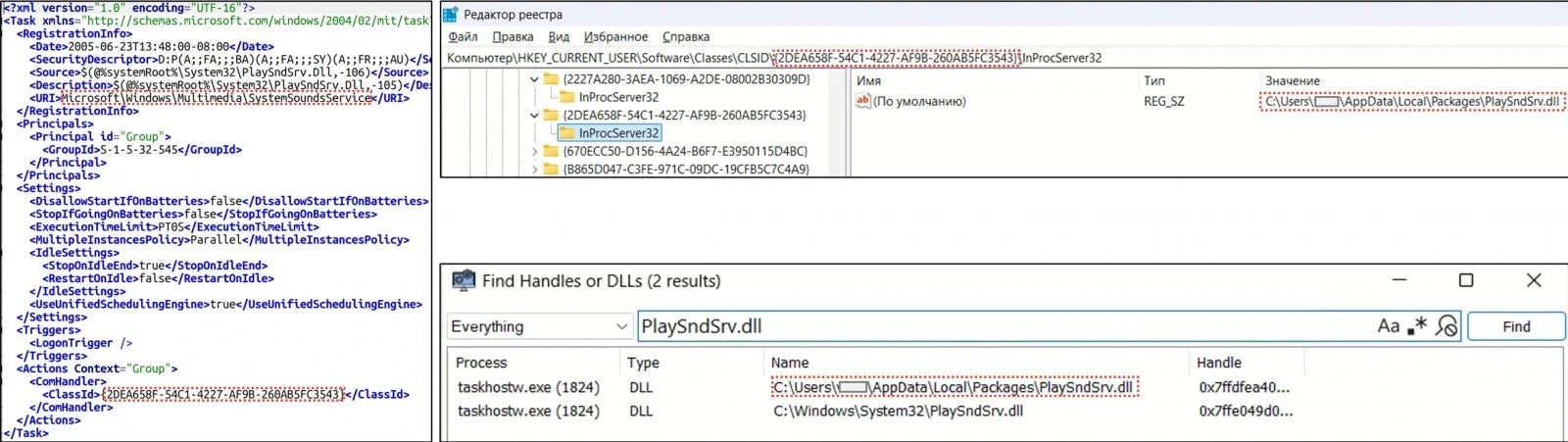
According to CERT-UA, they also observed network activity tied to domains like api.icedrive[.]net and app.koofr[.]net and recommend monitoring them closely. The attackers’ use of Signal as a delivery mechanism, combined with advanced malware capabilities, demonstrates the group’s ongoing innovation when it comes to targeting Ukraine’s digital infrastructure. Although Ukrainian officials voiced concerns over Signal’s lack of cooperation, the platform maintains it does not share communication data with any government.
The campaign poses a broader risk to government and enterprise networks that rely on encrypted messaging platforms like Signal for sensitive communications. The deployment of stealthy, modular malware raises concerns about long-term espionage, data theft, and operational disruption across sectors critical to national security.
The Ugly | Salt Typhoon Expands Cyber Espionage Operations to Canadian Telecos
China-linked state-sponsored threat group Salt Typhoon has expanded its targeting to include Canadian telecommunications providers. Confirmed by the Canadian Centre for Cyber Security and the FBI, the group successfully breached a major Canadian telecom firm in February 2025 by exploiting CVE-2023-20198 – a critical Cisco IOS XE vulnerability disclosed in late 2023.
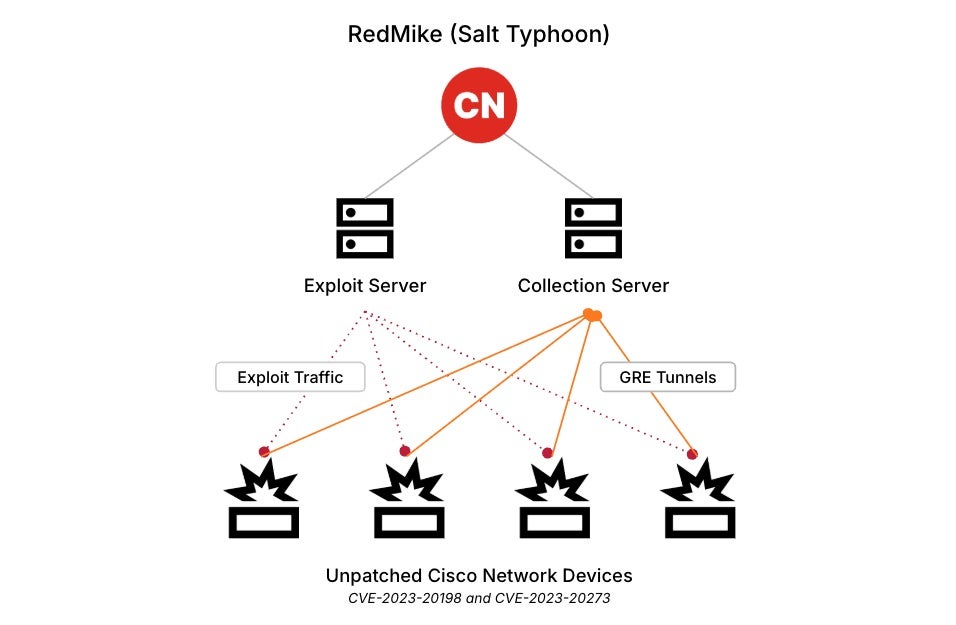
This flaw, which allows unauthenticated remote attackers to gain administrator-level access, had previously been used to compromise over 10,000 devices worldwide. Despite having ample time to apply available patches, at least one Canadian telecom provider remained vulnerable, enabling the attackers to compromise three network devices. The threat actors retrieved configuration files and established a Generic Routing Encapsulation (GRE) tunnel, allowing them to intercept sensitive network traffic.
The breach follows earlier Salt Typhoon activity from October 2024, when indicators of cyber reconnaissance were observed across dozens of Canadian organizations. Although no confirmed intrusions were reported at that time, authorities warned that failure to act would leave critical infrastructure exposed. That warning has now materialized.
Beyond telecommunications, Salt Typhoon has been linked to reconnaissance and potential intrusion attempts in other sectors, raising concerns about future lateral movement and supply chain attacks. Their tactics typically focus on compromising perimeter devices – routers, firewalls, and VPN appliances – with managed service providers and cloud vendors also targeted for indirect access to downstream victims.
The Cyber Centre warns that Salt Typhoon’s activity against large organizations is highly likely to continue through 2026. Telecommunication providers, in particular, remain high-value targets due to their access to metadata, subscriber information, and sensitive communications.


