The Good | Pentagon Accelerates AI Adoption to Strengthen Cyber & Operational Readiness
In a significant step forward to modernizing government operations, the DoD has awarded a contract up to $200 million to OpenAI to develop frontier AI-based capabilities for the Pentagon. The contact will be managed by the Chief Digital and Artificial Intelligence Office (CDAO), which currently leads AI adoption efforts across the U.S. military. Created in 2022, CDAO serves as the Pentagon’s central hub for AI expertise and innovation.
The contract is part of a broader government initiative to responsibly and effectively harness AI with the purpose of streamlining operations, reducing administrative burdens, and shoring up national defense. A core part of the project includes the development of prototype agentic workflows – semi-autonomous AI agents that are designed to perform repetitive, time-consuming tasks that currently demand a large amount of human effort. These AI tools would free up both military and civilian personnel, with focus and time redirected to high-value work to enhance mission readiness.
The effort builds on the Pentagon’s previous AI work, including Task Force Lima, which spent over a year evaluating generative AI’s reliability for defense use. As the DoD continues to embrace its potential, with safeguards in place, AI is actively being used by the Army to sift through massive volumes of unstructured data, such as regulations, field manuals, and procurement documents. It’s also worth noting that generative AI is already assisting with drafting acquisition paperwork and translating orders into actionable tasks for military aid efforts.
This contract signals the DoD’s growing confidence in AI’s utility and points to a larger trend: federal agencies are moving forward with secure, carefully-governed AI integration to enhance cybersecurity, data management, and operational effectiveness across government agencies.
The Bad | New Threat Actor ‘Water Curse’ Exposes Risks of Weaponized GitHub Platforms
Water Curse, a newly identified threat cluster, is weaponizing GitHub repositories to distribute multi-stage malware, masquerading as penetration testing tools. While the cluster has yet to be attributed to any known actor, the activity is described as stealthy with financially-motivated goals.
Cyber researchers have been tracking the cluster since March 2023, noting the use of at least 76 GitHub accounts using Visual Studio files to conceal payloads like SMTP email bombers and a remote access trojan called Sakura-RAT. These payloads allow attackers to exfiltrate data such as credentials, browser information, and session tokens, while also establishing long-term access to compromised systems.
The infection chain begins with heavily obfuscated Visual Basic Script and PowerShell loaders, which download encrypted archives containing malicious Electron-based applications. These then conduct system reconnaissance and establish persistence using anti-debugging, privilege escalation, and defense evasion techniques. Additional scripts are used to weaken system defenses and prevent recovery.
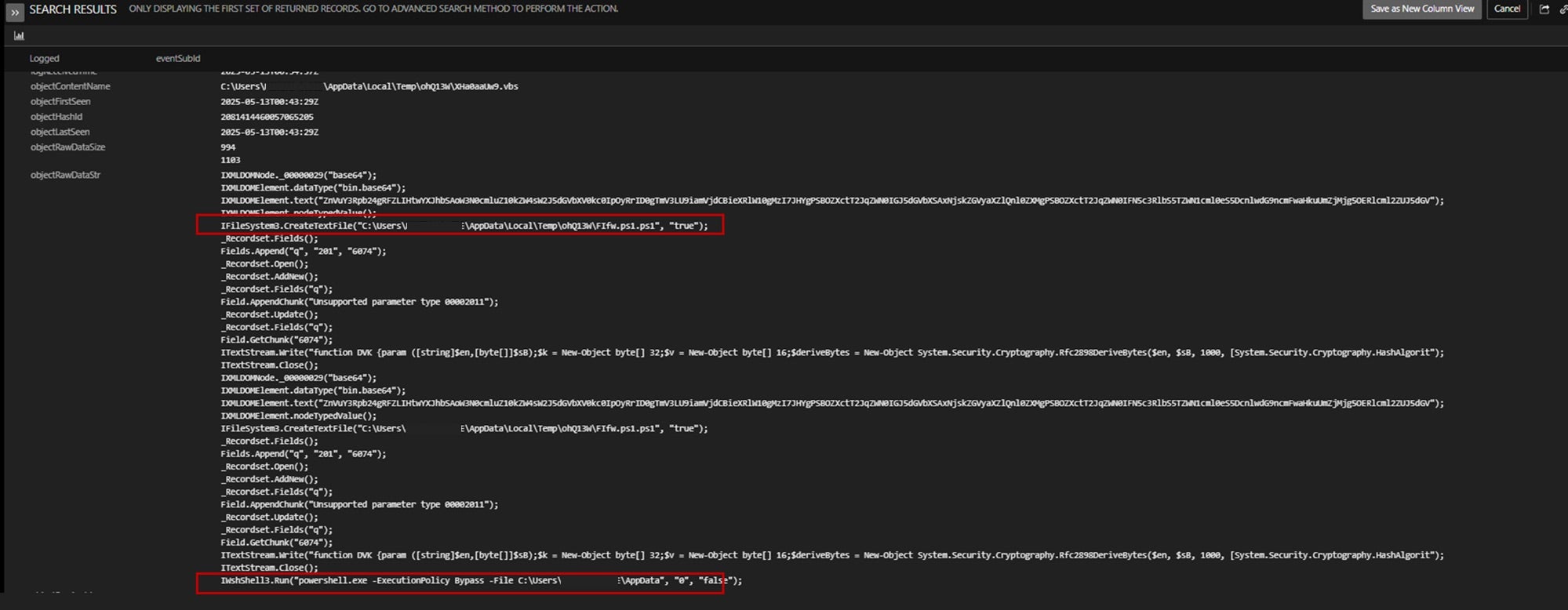
So far, infrastructure and tooling associated with Water Curse show a focus on scalability, stealth, and cross-functional development. The unknown threat actor blurs the line between red team utilities and actual malware, deploying a wide variety of components ranging from OSINT scrapers and game cheats to crypto-wallet tools and credential stealers, all suggesting a multi-vertical monetization strategy. While similarities exist between Water Curse and known distribution-as-a-service (DaaS) campaigns, researchers have yet to confirm a direct connection.
Threat actors continue to quietly exploit trusted platforms to hide malware in plain sight, embedding malicious tools in seemingly legitimate projects. Tactics like the ones used by Water Curse not only complicate detection but also highlight the need to effectively secure developer ecosystems and open-source platforms.
The Ugly | Zero-Day Used in “Trinper” Malware Campaign Highlights Software Supply Chain Risks
A recently-patched Google Chrome flaw was exploited in March by a threat actor known as TaxOff, who used it to slip a stealthy backdoor called “Trinper” onto targeted systems. The attack began with a phishing email, then exploited a sandbox escape flaw (CVE-2025-2783) to bypass Chrome’s defenses, giving TaxOff access with no clicks or downloads required beyond the initial link.
Google Chrome Zero-Day CVE-2025-2783 Exploited by TaxOff to Deploy Trinper Backdoor #cybersecurity #hacking #news #infosec #security #technology #privacy thehackernews.com/20…
— Ninja Owl (@ninjaowl.ai) 19 June 2025 at 05:18
The malware is written in C++ and uses multithreading to stay hidden while capturing keystrokes, collecting files, and exfiltrating data. It communicates with a remote command and control (C2) server to execute commands, launch a reverse shell, and extend its capabilities. Initial infection vectors traced back to phishing emails all contained links to malicious websites hosting the exploit or ZIP files with shortcuts that launched PowerShell commands, often using loaders like Donut or Cobalt Strike.
TaxOff was first reported in late 2024, and has consistently used finance-themed and geopolitical lures to target domestic organizations. In this most recent operation codenamed “ForumTroll”, the phishing emails impersonated invitations to high-profile Russian forums, leading users to a fake website hosting the exploit. Security researchers have since reportedly uncovered further links between this operation and earlier attacks dating back to October 2024, some of which share tactics with another group called Team46, raising the possibility of overlap between the two.
The attackers’ repeated use of zero-days and complex backdoors points to a long-term strategy focused on persistence and stealth. These incidents underscore the continued exploitation of software supply chains and widely used platforms to deliver advanced malware through trusted but vulnerable entry points.


