Cybercrime went from a nuisance to a threat when its practitioners realized their crimes could produce benefits such as financial gain, political pressure, and to promote causes supported by the attackers. This spurred innovations in offensive methodologies and required defenders to evolve further. Today, we have fully funded threat operations, state-backed and organized as a standard business. This operationalization of cybercrime has unlocked an era of threats with focused agendas and more tangible impact to business. Defensive technology has kept pace with threats to a degree, but this rapid expansion has left organizations struggling to keep up in an enigmatic market of security solutions.
The persistence of older security products now complicates the endpoint protection landscape. Available solutions include varying terminology like antivirus (AV), next-generation anti-virus (NGAV), endpoint protection platform (EPP), endpoint detection and response (EDR), and the most recent arrival to the space, modern endpoint detection and response (Modern EDR). While all of these solutions are focused on endpoint security, they vary in terms of the technology implemented and directional focus of the solution, and their ability to stop threats and threat actors.
This blog post reviews the fundamentals of endpoint security solutions so organizations can confidently navigate the landscape and choose defenses that truly match their environments.
The Evolution of Threats
Adversarial tactics have evolved significantly from the early days of the internet. The browser plugins and pop-up adware, while still present today, were the kings of the cyber underground in the early aughts of the century. While those malware are easy to detect and AV solutions quickly came to the rescue, the threat actors did not stop evolving there, have not stopped since, and are not expected to stop anytime soon. This is where the implementation of AI-based technology shows its advantage.
Modern EDR toolsets, while still maintaining the old-school antivirus protections, integrate the advantages of NGAV by monitoring system behavior to identify potential attacks that may not have been detected by signature-based scanning. Coupled with a deep integration with AI, Modern EDR expedites response operations significantly. This is particularly prudent when it comes to novel threats, where behavioral detection and AI assistance enable response with the same speed as a known threat. Modern EDR solutions then use this telemetry to refine their detection logic automatically, scaling detection capabilities.
Separating Modern EDR toolsets from the rest of the field further is their implementation of generative AI models and agentic workflows to assist in threat hunting and incident response operations. Natural language queries, or enabling analysts to perform investigations without being a query language expert, allows security teams to be more efficient and effective, while upleveling analysts to perform above their station.
The Modern EDR field is limited, currently, with one solution standing out above the rest: SentinelOne’s Singularity Endpoint.
Understanding the Fundamentals: AV, NGAV & EPP
Antivirus (AV)
At the foundational level, your endpoints need some type of antivirus. This typically correlates to “signature-based detection,” meaning the security solution is scanning your files against a library of known malicious file signatures. Suppose a file on your computer matches the signature of a malicious file. In that case, a detection occurs, and generally, some form of quarantine or cleaning action is taken to mitigate the threat posed by the malicious file.
This type of detection was ideal for the early days of the internet when malware and cybercrime were in their nascency, and is still applicable today for the more basic or well-known attacks, but does not constitute a full endpoint protection solution in the current threat landscape.
Next-Generation Antivirus (NGAV)
As threat actors iterated on their tactics and the tools they used, relying on known malicious signatures fell out of sufficiency. While still required for a holistic security posture, signature-based scanning was not able to identify the most novel threats, creating avenues for malicious payloads to bypass current protections. Behavioral analysis and the integration of machine learning into endpoint protection were the solution. By analyzing the behavior of the system, on top of signature scanning, NGAV was able to identify anomalous behavior from threats that may not have a known signature yet. This elevated protections to meet the newest threats of the time, ransomware.
Endpoint Protection Platform (EPP)
Endpoint protection platforms were the next to make their way to market, carving out a segment of endpoint security not adequately addressed by antivirus, proactive prevention. EPP is often confused with AV, but its focus is different and worth understanding. EPP focuses on preventing attacks through attack surface reduction and device control, making your endpoints a harder target for adversaries. This puts the focus on preventing malware from reaching the laptop through firewall controls, USB port blocking, and other endpoint settings configurations that limit avenues for malicious files to make it to your computer’s operating system. EPP is a critical security feature that you should have deployed in your environment, protecting your assets in tandem with an AV solution.
The Rise of EDR: Legacy vs Modern
Legacy Endpoint Detection & Response
AV, NGAV, and EPP gave rise to what had become the mainstay option for organizations looking to secure their endpoints until recently: endpoint detection and response. EDR is the combination of signature-based detection, endpoint control, and moderate implementation of machine learning for endpoint security. EDR tools enhance signature-based AV with behavioral monitoring, monitoring system processes and actions for patterns that align with more advanced attacks such as ransomware, and provide more advanced, and sometimes automated, response actions. Additionally, EDR suites enable more effective investigation and response to security incidents through a centralized portal and investigative tools.
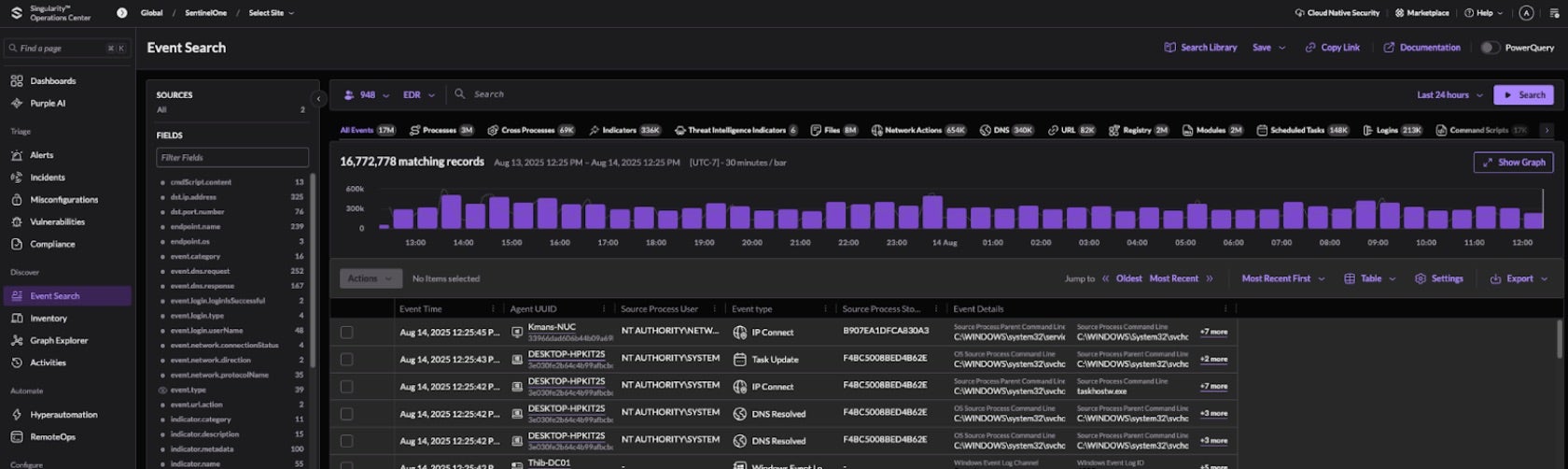
EDR solutions accomplish this through log and telemetry data pulled from the endpoint into their centralized platform for analysis. This provides deeper visibility into endpoints than AV/EPP, and more advanced response capabilities through automation.
This combined package of AV, NGAV, EPP, and a centralized investigation and response platform was the right solution for the needs of the time, and has been a strong iterative improvement of endpoint protection capabilities, but is not the end of the evolutionary line for endpoint security. EDR toolsets, while powerful, require skilled hands to operate and often come with a steep learning curve. In the current labor market, organizations struggle to fill higher-level security engineering positions, and those are the exact roles that are responsible for administering EDR solutions, leaving many organizations under-protected with misconfigured security toolsets. The analysts that are on the team are often overwhelmed with the number of alerts generated by the EDR solution, each requiring a level of manual investigation, and often lacking some critical context that would help expedite investigative operations.
Modern Endpoint Detection & Response: The Next Chapter
These gaps, and the advancement of artificial intelligence technologies, have led to the rise of the latest iteration on endpoint security, Modern EDR. Building on the heritage of AV, NGAV, EPP, and EDR, and leveraging AI and automation, Modern EDR increases the likelihood of stopping attacks, and the speed at which organizations can investigate and respond to security threats. This operational boost is a product of Modern EDR solutions placing heavy emphasis on AI implementations in detections, investigations, automation, and proactive defenses, making them more effective against zero-day vulnerabilities, limiting organizational attack surfaces, and reducing overall risk.
Modern EDR integrates the comprehensive log collection, threat prevention, detection, and response capabilities of traditional EDR with cutting-edge AI and automation for enhanced detection and response. Leveraging advanced reasoning and language models for sophisticated threat hunting and analysis, proactive prioritization, and advanced automation for efficient threat mitigation and response, this potent amalgamation of technologies enables teams to do more with less, empowers analysts to investigate incidents more effectively without the steep experience requirement, and expedites response actions through automation.
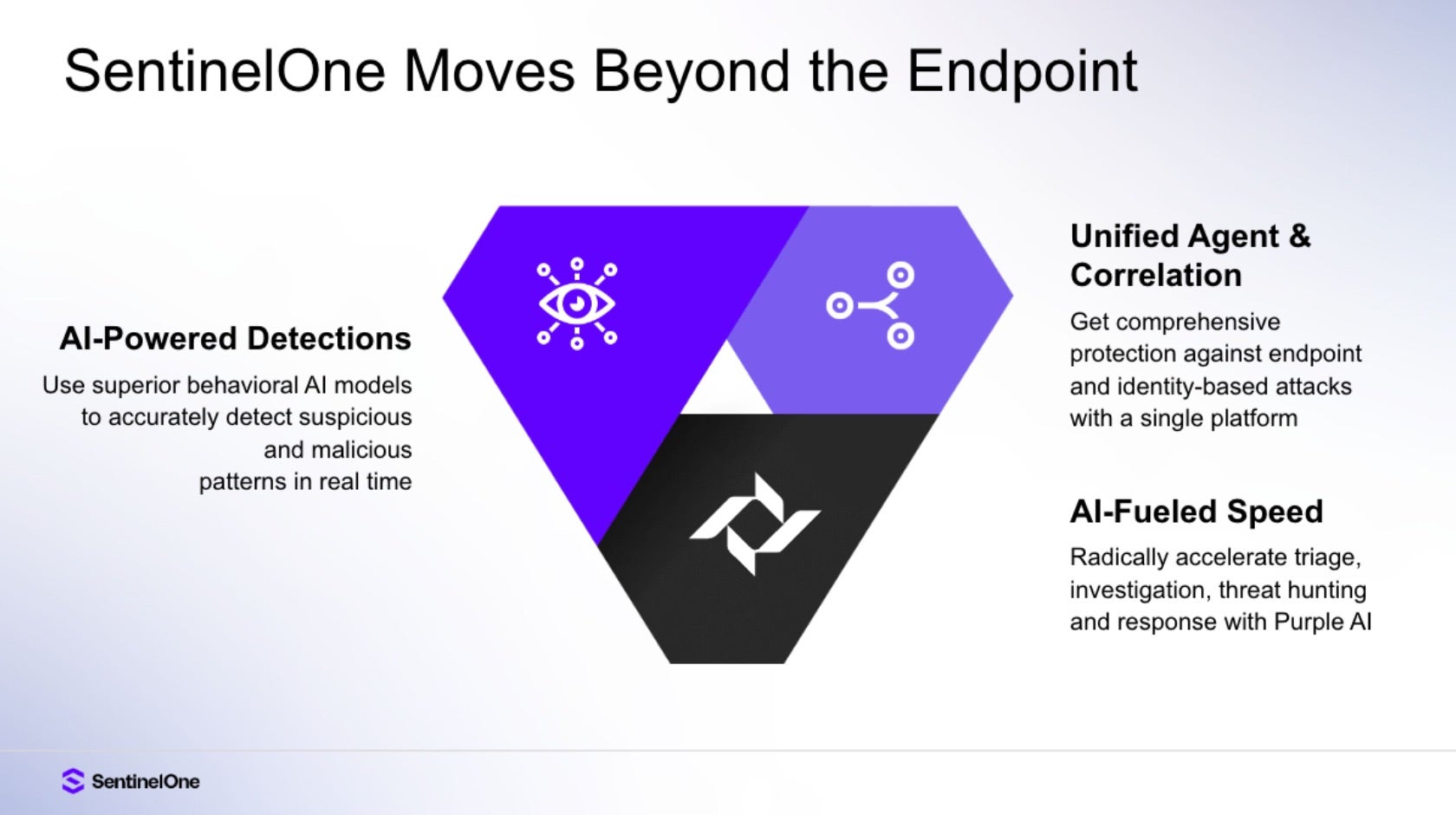
Modern EDR solutions also expand their monitoring capabilities to other aspects of the environment, such as Software-as-a-Service (SaaS) solutions and identity platforms, through integrations with a centralized console, giving rise to the extended detection and response (XDR) moniker. XDR primarily relates to this expansion of integrations across attack surfaces beyond endpoints, enabling even wider visibility across organizational assets and solutions.
Why Modern EDR with AI-Assisted Tooling is Optimal
Organizations looking for an endpoint security solution in 2025 have a plethora of options available to them, each with its own terminology and marketing that can make the decision a quagmire for business leaders. In the current threat landscape, adopting a more forward-looking solution, such as a Modern EDR tool that heavily utilizes AI technologies and automation, is required to stay at pace with the evolving threats and attack techniques.
The advantages seen from Modern EDR solutions are easily illustrated across three domains: AI implementation, automation, and proactive defense.
AI Implementation
Modern EDR toolsets take full advantage of the technology available today, with an eye on innovating as that technology evolves. This is seen through the implementation of artificial intelligence across the product for detection, administration, automation, and operations.
A hallmark feature of Modern EDR is the use of generative AI for natural language query development. This enables analysts to perform investigations and craft detection queries without being an expert in the specific query language of the toolset, effectively boosting level one analysts to perform at a level two or three standard.
Noise reduction is another key area where Modern EDR toolsets stand out. AI detection engines are utilized to detect threats as well as determine the fidelity of any given detection. By eliminating low confidence detections and alerts, Modern EDR solutions reduce the overall alert volume analysts are burdened with, reducing the associated alert fatigue that can have detrimental impact to security operations.
Automation
Many AV and EDR options contain automation to a certain degree, enabling automated quarantine or cleaning options, but that is not enough in the current threat landscape. Automations should extend beyond immediate containment to assist the analyst responsible for investigations, and expand beyond the EDR solution to enable more efficient workflows with connected utilities. This is a further implementation of AI that helps lower mean time to respond (MTTR) metrics and reduce exposure windows through immediate data and context availability for the analyst. Assisted by automated workflows that remove smaller tasks that would consume additional analyst time, such as establishing a Zoom bridge or Slack channel for response operations, further expedites security operations and allows analysts to stay focused on the investigation at hand. 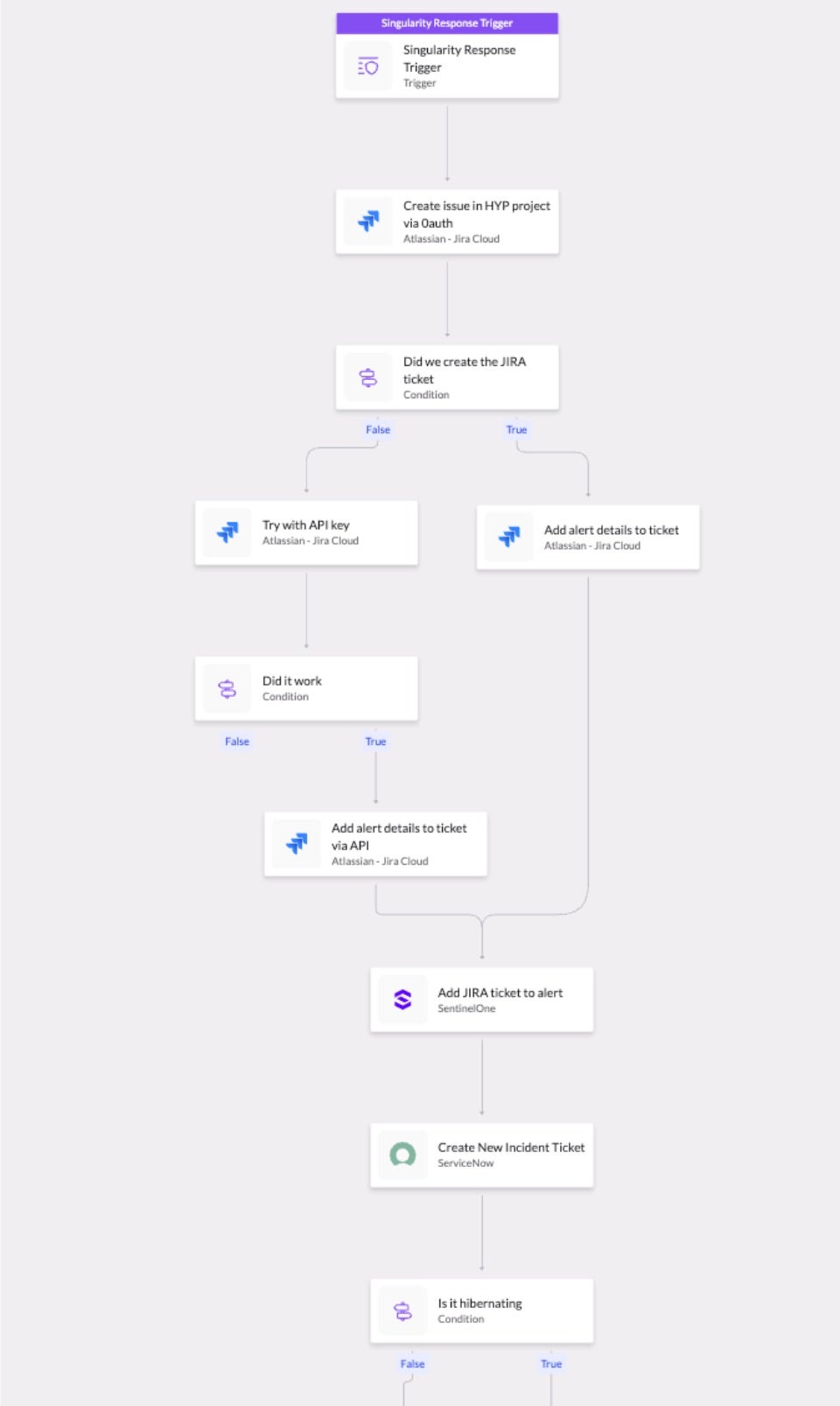
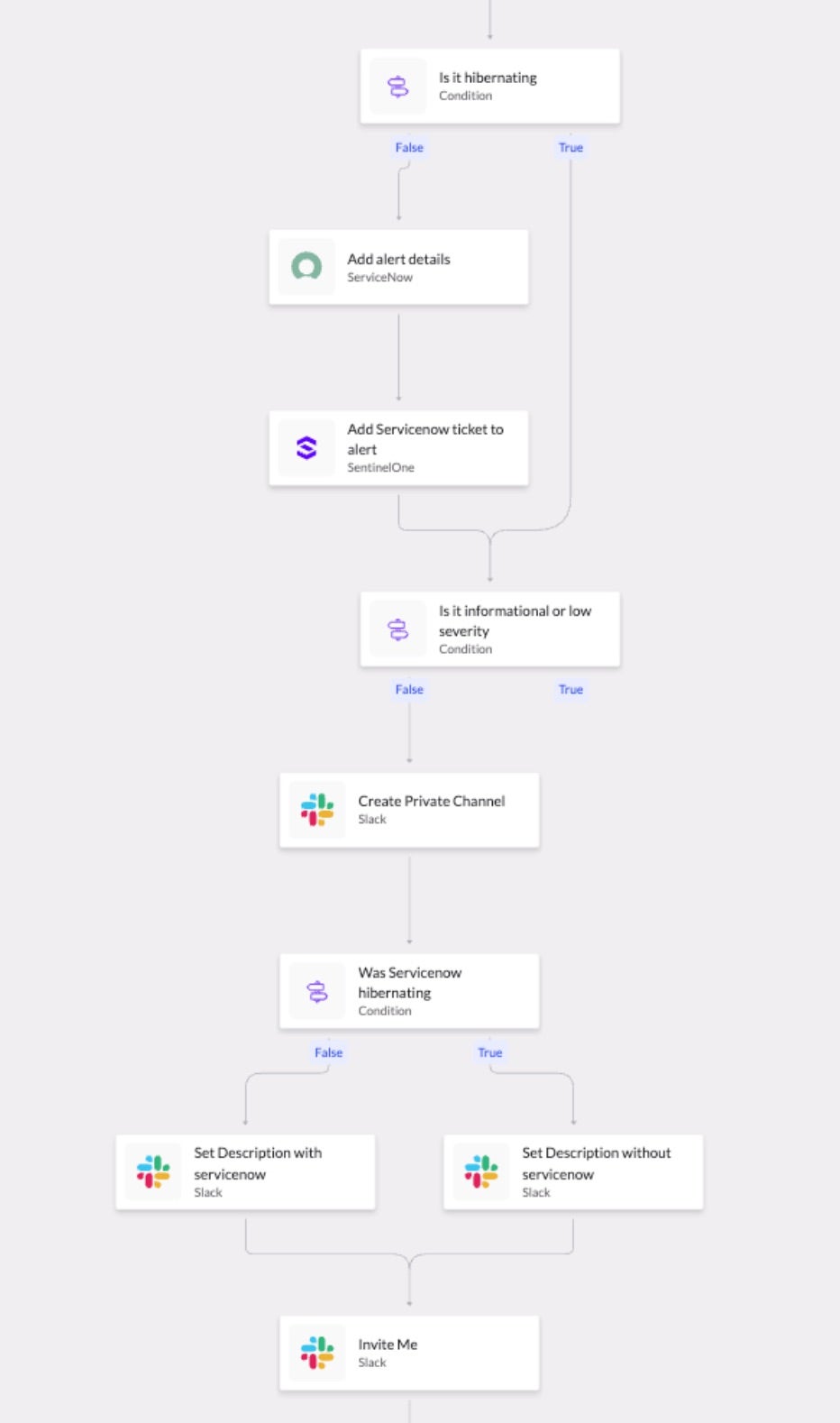
AI implementations can also aid in the investigation process through advanced correlation of events across log sources, building an attack story that can aid analysts in determining the root cause of the incident, potential access vectors, and the total scope of affected systems. While this data is available within legacy EDR solutions, it often requires manual investigation by the analyst, requiring a more elevated skillset to be performed effectively, and taking significantly more time, while a threat actor may be within the environment.
Proactive Defense
The benefits of AI-assisted tooling in incident response are easily visualized, but focus also needs to be applied to the proactive or prevention side of endpoint security. Several EDR solutions include EPP-like functions for reducing attack surfaces, which is the minimum that should be expected from a current Modern EDR solution. With the implementation of AI, Modern EDR customers can benefit from collective intelligence through connected models sharing indicator information across multiple organizations. This means a novel threat cannot stay novel for long, with other environments utilizing the same AI solutions being inoculated against the threat after its first detection.
Modern EDR solutions may also provide a level of AI-powered offensive security tooling for identifying potential security gaps or misconfigurations within the infrastructure, attempting minor exploits against the environment, and providing further assistance in reducing attack surfaces. While not a replacement for an annual penetration test, these engines can help identify weaknesses between exercises, helping maintain security over the course of the year.
Conclusion
AV, NGAV, EPP, EDR, and Modern EDR coexisting in the market can present a challenge for business leaders trying to make the right decision for their organization’s endpoint security, and knowing the differences between the options can be a significant advantage. Legacy AV and EPP products are not sufficient for today’s threat landscape, and businesses should instead be looking for advanced solutions that include them. EDR options, while utilizing machine learning, do not go far enough to enable security operations or take full advantage of currently available technologies. Modern EDR solutions are the next iteration of endpoint security and come with advantages unmatched by legacy solutions, enabling organizations to run more efficient security operations, uplevel analysts, and build stronger proactive defenses. In an age of rapidly evolving threats, utilize a security solution that can keep up.
Stuck with a legacy endpoint protection solution that struggles to keep up with current threats? Check out SentinelOne’s Modern EDR solution: Singularity Endpoint. Book a demo today to see how Singularity Endpoint can protect your organization with an AI-powered first line of defense.