Singularity™ Identity
The Evolving Risks for Identity Security
Stolen credentials, escalated privileges, and directory attacks have become increasingly common as top entry points in breaches. Yet, traditional defenses leave organizations exposed with weak, disconnected, and outdated identity protections.
Limited Visibility
Many identity attacks involve the endpoint, but siloed tools and directories leave critical visibility gaps for attackers to exploit.
Complex Hygiene
Hybrid identity environments can be costly, with time-consuming audits and misconfigurations that attackers exploit faster than teams can remediate.
Delayed Detection
Credential theft and directory attacks unfold in seconds, and they’re often not detected until after privilege escalation or lateral movement.
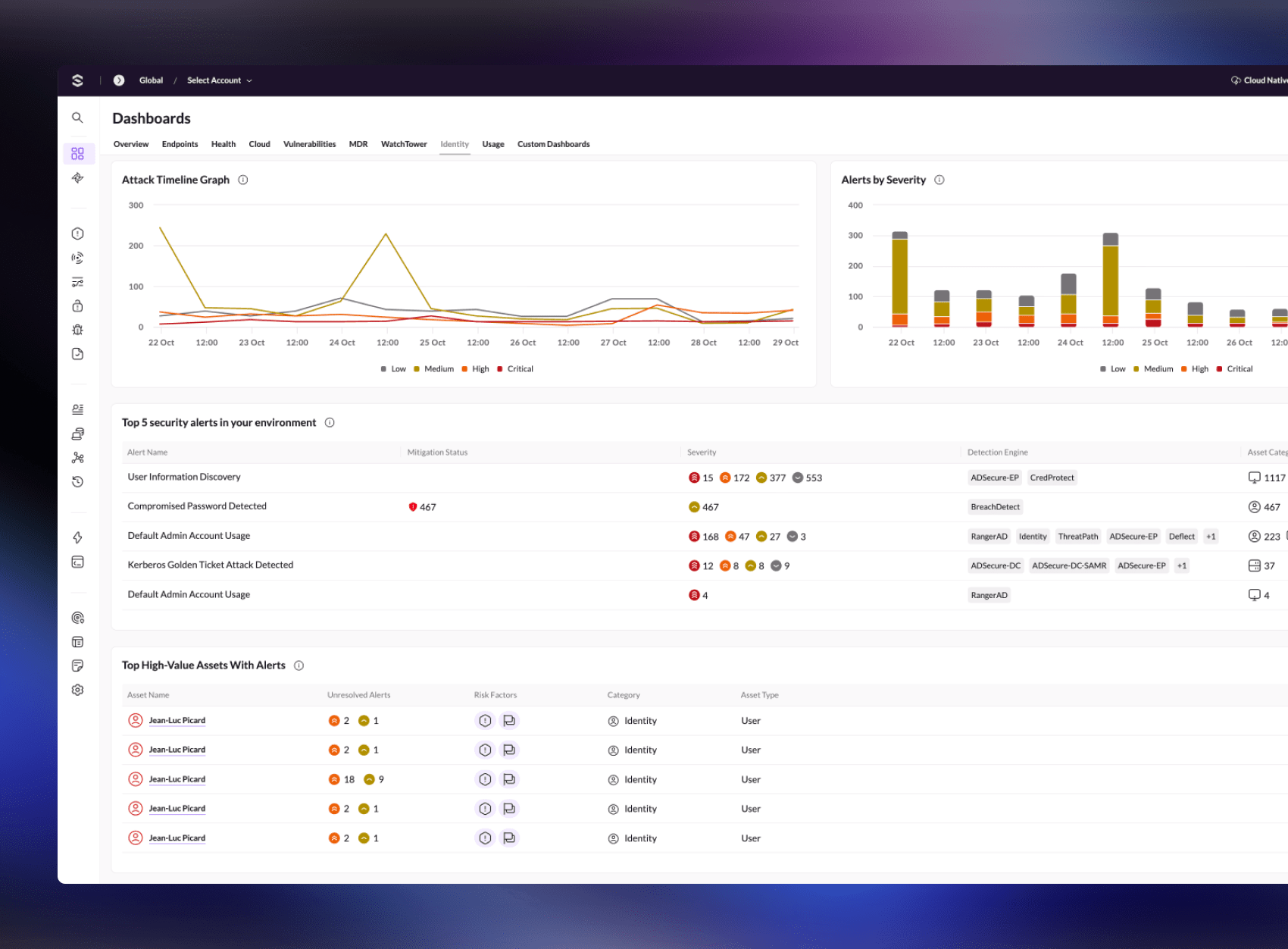
Gain Complete Visibility
- Get end-to-end visibility across endpoints and identities from a single lightweight agent.
- Correlate endpoint and identity activity for context-driven detection and faster triage.
- Eliminate blind spots across siloed environments.
- Accelerate investigations with unified, high-fidelity alerts and correlated evidence.
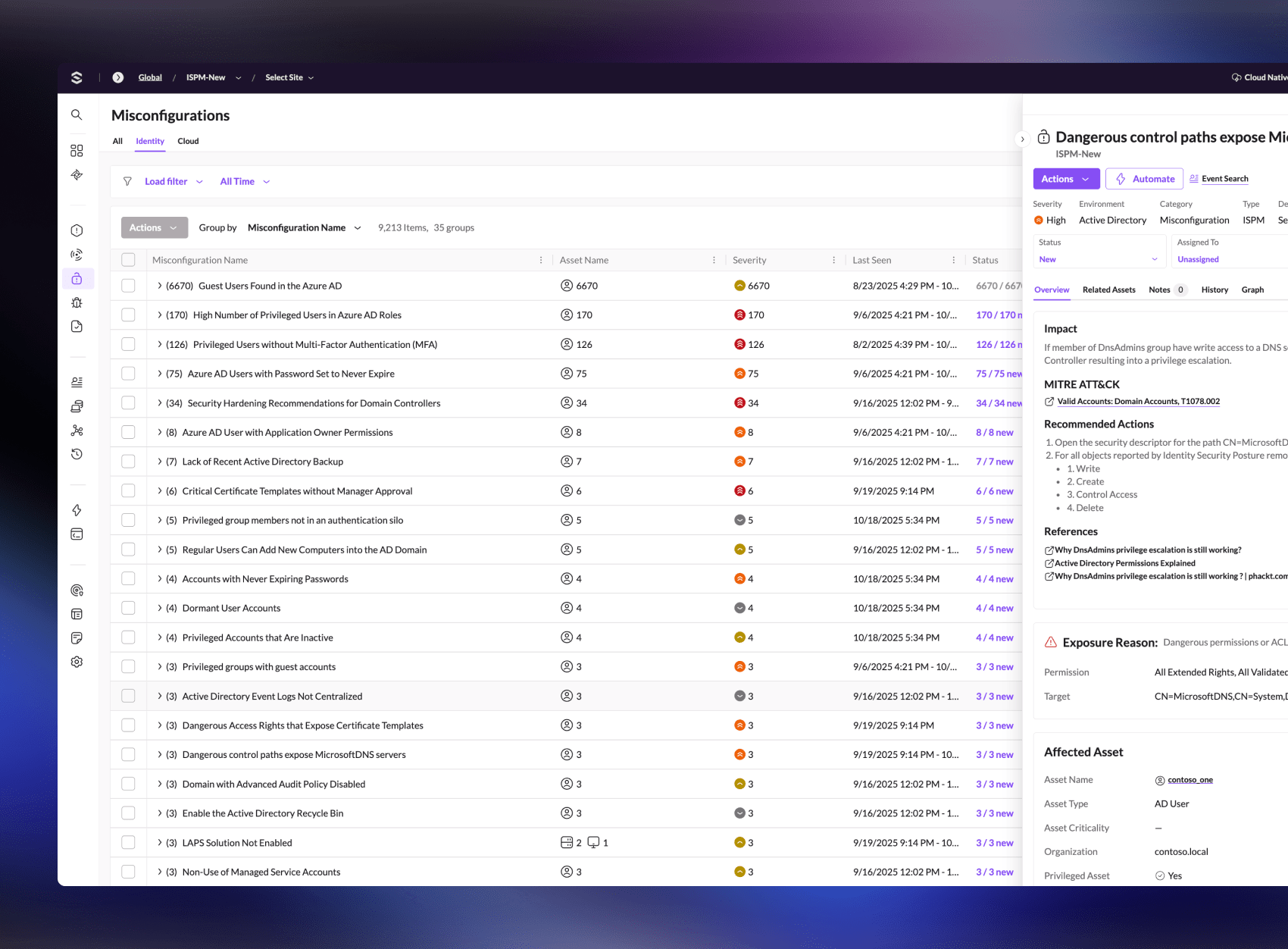
Reduce the Identity Attack Surface
- Identify misconfigurations and exposures before attackers exploit them.
- Harden Active Directory and cloud identity providers, including Entra ID, Okta, Ping, SecureAuth, and Duo.
- Strengthen identity hygiene through comprehensive posture assessments.

Proactively Disrupt Attackers
- Deploy deception techniques to lure and trap intruders early.
- Detect reconnaissance and credential harvesting attempts in their earliest stages.
- Surface stolen or compromised credentials exposed on the dark web.

Stop Attacks in Real Time
- Instantly detect and remediate credential theft and privilege escalation attempts.
- Block lateral movement across endpoints and domains — before escalation.
- Automate remediation workflows to disable compromised identities and enforce password changes.
- Protect users, accounts, and infrastructure in real time.
Experience Singularity Identity Security
See how SentinelOne Identity Security delivers end-to-end visibility and real-time defense. Connect with a product expert to see how Singularity Identity can help you:
- Eliminate blind spots with a single unified endpoint and identity agent.
- Reduce risk by addressing misconfigurations and exposures across hybrid environments.
- Stop credential-based attacks instantly with proactive defense.
The World’s Leading and Largest
Enterprises Trust SentinelOne
Including four of the Fortune 10 and hundreds of the Global 2000.
The Standard in Security Excellence
Tried and trusted by the industry's leading authorities, analysts, and associations.
A Leader.
Five Years Running.