Datasheet
Wayfinder Threat Hunting

Expert Threat Hunters curate detections, validate suspicious activity, and drive behavioral queries to expose threats automated tools miss.
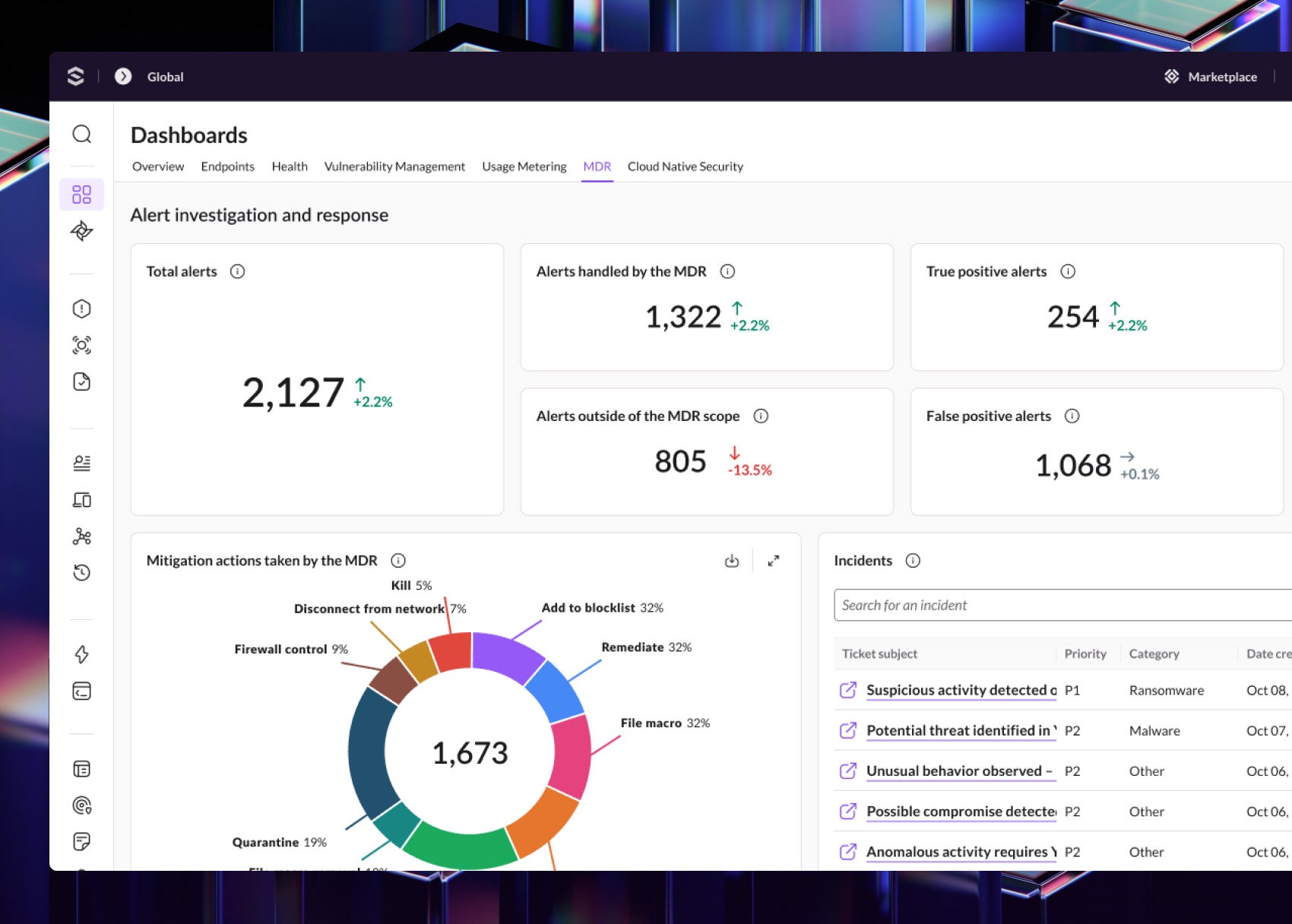
Findings are validated against real telemetry, ensuring you only receive high-confidence alerts that require attention.
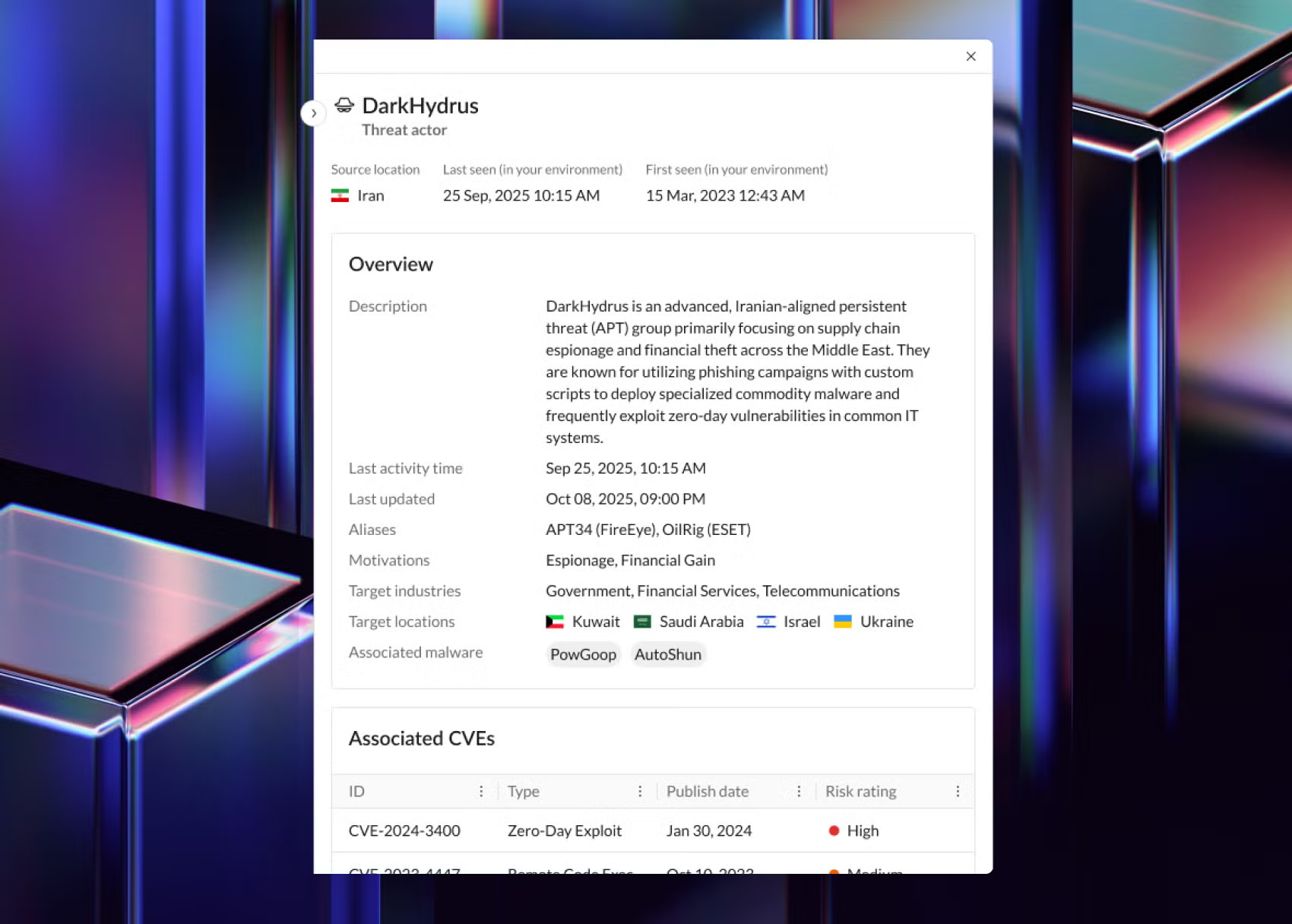
Fuel investigations with continuously enriched IOCs, actor attribution, and campaign context.
Detect novel campaigns and TTPs with expert-driven queries that rapidly convert breaking intel into active hunts.
Hunt with zero overhead. Access findings and detection status directly in your console for a unified experience.
Stay informed with hunter-produced Flash Reports summarizing emerging threats, actors, and new TTPs.