The Good | U.S. & Spanish Officials Crack Down on Hacktivist & Identity Theft Activities
U.S. officials have charged Ukrainian national Victoria Dubranova for allegedly supporting Russian state-backed hacktivist groups in global critical infrastructure attacks. Extradited earlier this year, Dubranova faces trials in February and April 2026 tied to her suspected involvement in NoName057(16) and CyberArmyofRussia_Reborn (CARR), respectively.
GOT HER: A pro-Russian UKR hacker, Victoria Dubranova, has been arrested in a MASSIVE 99-count indictment for GRU-backed attacks on US water systems and food plants. She’s been extradited — and now there’s a $10M bounty on her GRU bosses! https://t.co/i31z4aXPMF pic.twitter.com/AAKeGQWx0K
— Chuck Pfarrer | Indications & Warnings | (@ChuckPfarrer) December 12, 2025
The indictment states that NoName057(16) operated as a state-sanctioned effort involving multiple threat actors and a government-created IT center. Their tooling includes a custom DDoS called ‘DDoSia’ used to launch attacks against government and financial agencies as well as critical transportation.
Prosecutors say Russia’s military intelligence service funded and directed CARR, a hacktivist group with over 75,000 Telegram followers and a long record of attacks. Damage to U.S. water systems, an ammonia leak at a Los Angeles facility, and targeting of nuclear and election infrastructure are all attributed to CARR. Dubranova faces up to 27 years on CARR-related charges and 5 years on NoName charges. Multi-million dollar rewards are in place for information on either threat group.
In Spain, authorities have arrested a 19-year-old hacker for the alleged theft and sale of 64 million records stolen from nine organizations. The suspect faces charges including cybercrime, unauthorized access, and privacy violations.
The investigation first started in June after breaches at the unnamed firms were reported. Police later confirmed that the suspect possessed millions of stolen records containing full names, addresses, emails, phone numbers, DNI numbers, and IBAN codes. He reportedly tried to sell the data on multiple forums using six accounts and five pseudonyms.
While officers have seized cryptocurrency wallets containing proceeds from the alleged sales, the total number of individuals affected remains unclear. Given the scale of the crime, Spanish authorities emphasize the seriousness of attempting to monetize stolen personal information.
The Bad | Malicious VS Code Extensions Deploy Stealthy Infostealer Malware
Two malicious Visual Studio Code extensions, Bitcoin Black and Codo AI, were recently discovered on Microsoft’s VS Code Marketplace, infecting developers with information-stealing malware. Each disguised as a harmless color theme and an AI coding assistant, the extensions were published under the alias ‘BigBlack’. While download counts are still low at the time of this writing, both packages point to a clear intent to compromise developer environments.
Researchers note that earlier versions of Bitcoin Black used a PowerShell script to fetch a password-protected payload, briefly flashing a visible window that could alert users. The latest version now has a hidden batch script that quietly downloads a DLL and executable via curl, significantly reducing detection risk. Meanwhile, Codo AI delivers legitimate code-completion via ChatGPT or DeepSeek but embeds a malicious payload alongside these features.
Both extensions deploy the Lightshot screenshot tool paired with a malicious DLL that uses DLL hijacking to load an infostealer called runtime.exe. Once executed, the malware creates a directory under %APPDATA%\Local\ and begins exfiltrating sensitive data from system details and clipboard content to WiFi passwords, screenshots, installed software lists, and running processes. Finally, it launches Chrome and Edge in headless mode to extract cookies and hijack active sessions, targeting several crypto wallets including Phantom, MetaMask, and Exodus.
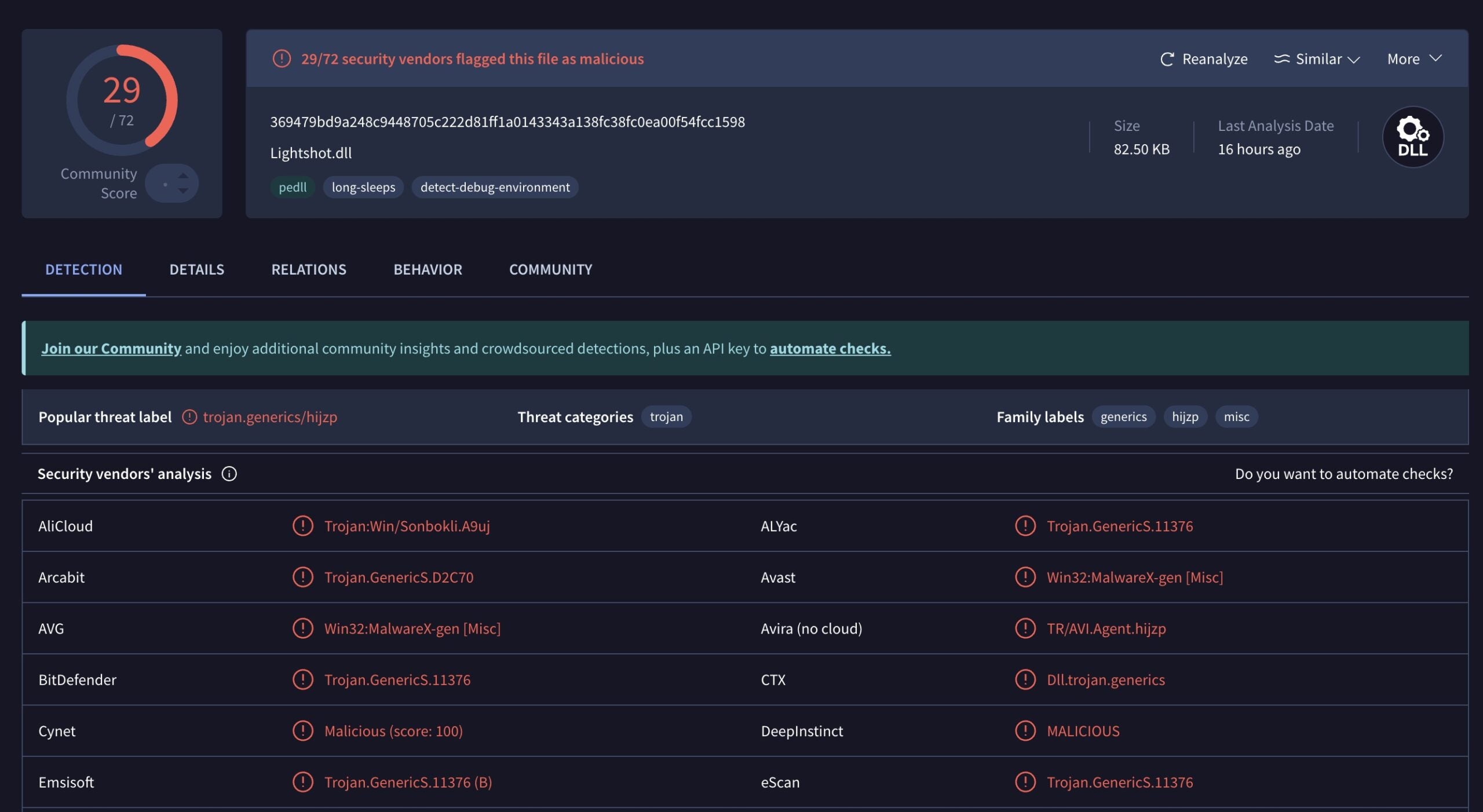
Microsoft has since removed both extensions from the Marketplace and the malicious DLL is already flagged by 29 of 72 antivirus engines on VirusTotal. Developers are advised to install extensions only from trusted publishers and stay alert to atypical extension behavior.
The Ugly | CyberVolk Resurfaces With New Telegram-Powered RaaS ‘VolkLocker’
CyberVolk, a pro-Russia hacktivist persona first identified in late 2024, resurfaced this August with a revamped ransomware-as-a-service (RaaS) offering known as VolkLocker (CyberVolk 2.x). SentinelLABS reported this week that the group has pivoted to using Telegram for both automation and customer interaction; however, operations are being undercut by payloads that retain artifacts, allowing victims to recover their files.
VolkLocker is written in Golang and supports both Windows and Linux. Payloads are distributed largely unprotected, with RaaS operators instructed to use UPX for packing. Builders must supply key configuration values including a Bitcoin address, Telegram bot token ID, encryption deadline, file extension, and more.
On execution, the ransomware attempts privilege escalation via the “ms-settings” UAC bypass, performs system and VM checks, and enumerates drives for encryption. A dynamic HTML ransom note then displays a 48-hour countdown, while a separate enforcement timer corrupts the system if deadlines or decryption attempts fail.
Telegram serves as the backbone of the RaaS, offering operators an administrative panel, victim enumeration, broadcast messaging, and optional extensions such as RAT and keylogger control. Recent ads show CyberVolk expanding into standalone tooling with tiered pricing models.
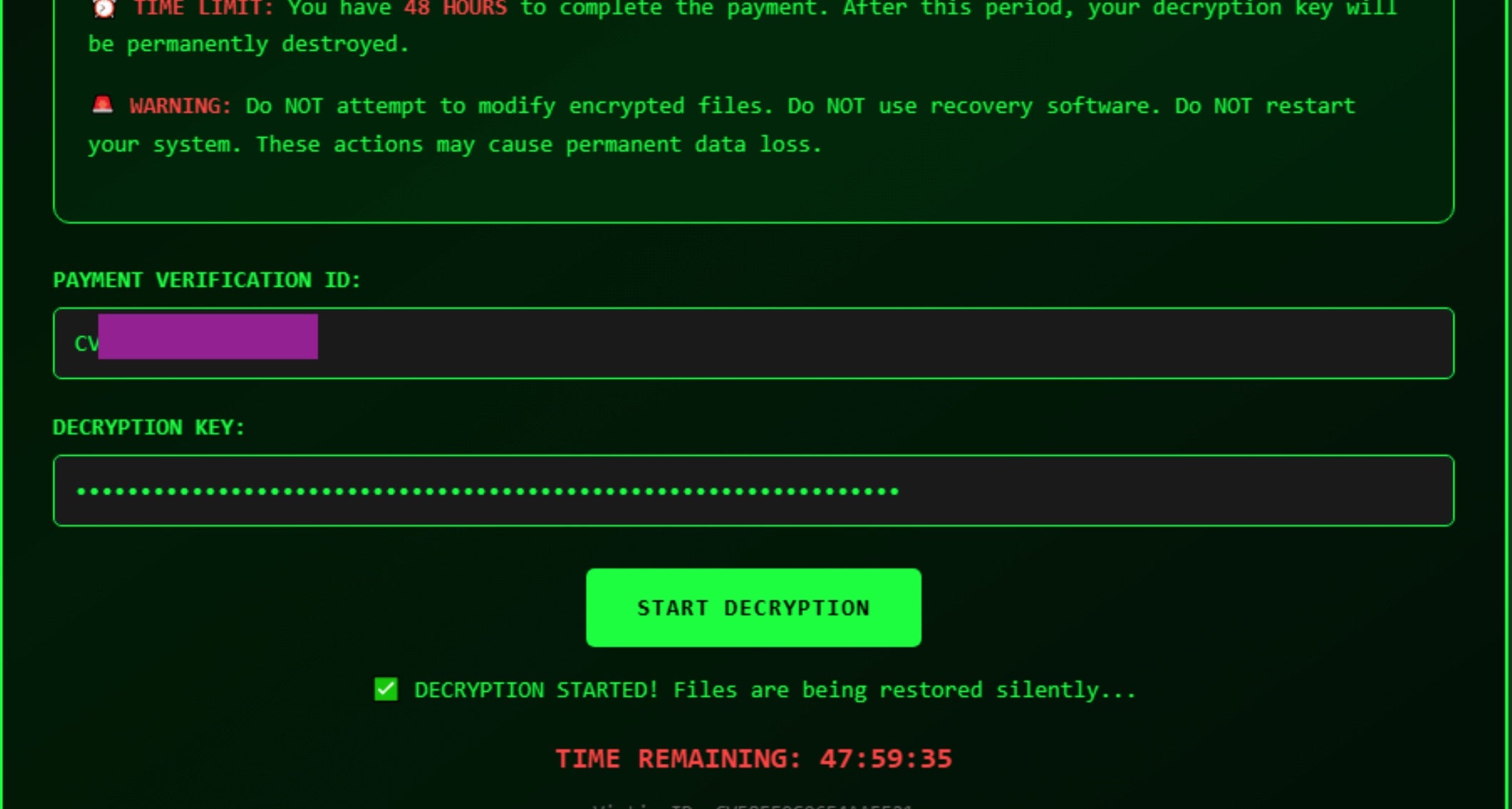
The encryption routine uses AES-256 in GCM mode with a hardcoded master key. Crucially, the key is written in plaintext to a file in %TEMP%, alongside the victim’s unique identifier and the attacker’s Bitcoin address – an apparent leftover test artifact that allows victims to decrypt their own files.
Despite repeated account bans on Telegram, CyberVolk continues to evolve its services. The plaintext key flaw, however, reveals quality-control issues that limit the real-world impact of VolkLocker as-is. SentinelOne’s Singularity Platform detects and blocks behaviors and payloads linked to CyberVolk.


