The Good | U.S. Authorities Charge ATM Hackers, Dismantle Darkmarket, and Seize ‘RAMP’ Forum
A U.S. federal grand jury has charged 31 defendants for their roles in an ATM jackpotting operation linked to Venezuela’s Tren de Aragua gang.
The indictment details 32 counts tied to the use of Ploutus malware to drain ATMs nationwide. After physically accessing the machines, suspects installed preloaded drives or USBs to deploy the malware, erase forensic evidence, and force cash dispensing until empty.
Prosecutors say the operation laundered millions to fund the gang, now officially designated a Foreign Terrorist Organization by U.S. authorities. This action follows two previous indictments from October and December 2025, bringing the total prosecutions to 87.
A Slovakian man has pleaded guilty to running Kingdom Market, a darkmarket that sold drugs, cybercrime tools, fake IDs, and stolen data. Alan Bill (aka Vend0r or KingdomOfficial) admitted conspiring to distribute controlled substances while operating the platform from 2021 to 2023.
During the probe, undercover agents bought fentanyl, methamphetamine, and a fraudulent U.S. passport before authorities seized the site in 2023. The investigation cited tens of thousands of users, crypto-based payments, and Bill’s role as the administrator. Sentencing is scheduled for this May as Bill faces 40 years of imprisonment and a possible $5 million fine.
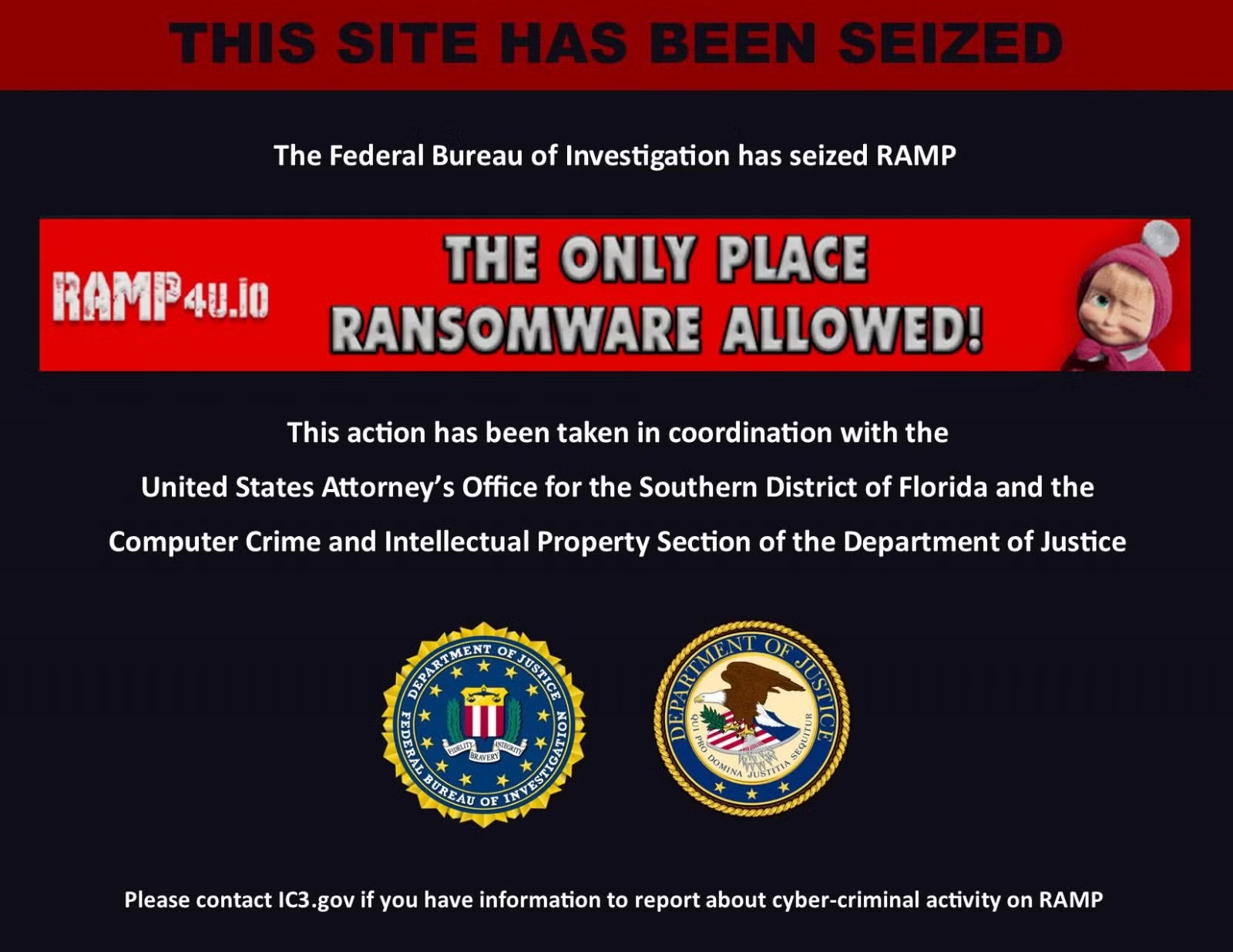
The FBI has seized the infamous RAMP cybercrime forum, a platform that openly hosted ransomware advertising, malware, and hacking services. Both its Tor and clearnet domain now display an FBI seizure banner, suggesting investigators have access to user data that could expose the forum’s users and all linked threat actors.
The takedown of the 5-year old forum removes one of the last centralized hubs where ransomware operators could openly advertise or trade access to networks, recruit affiliates, and coordinate at scale.
The Bad | 175,000 AI Systems Exposed Without Security Controls
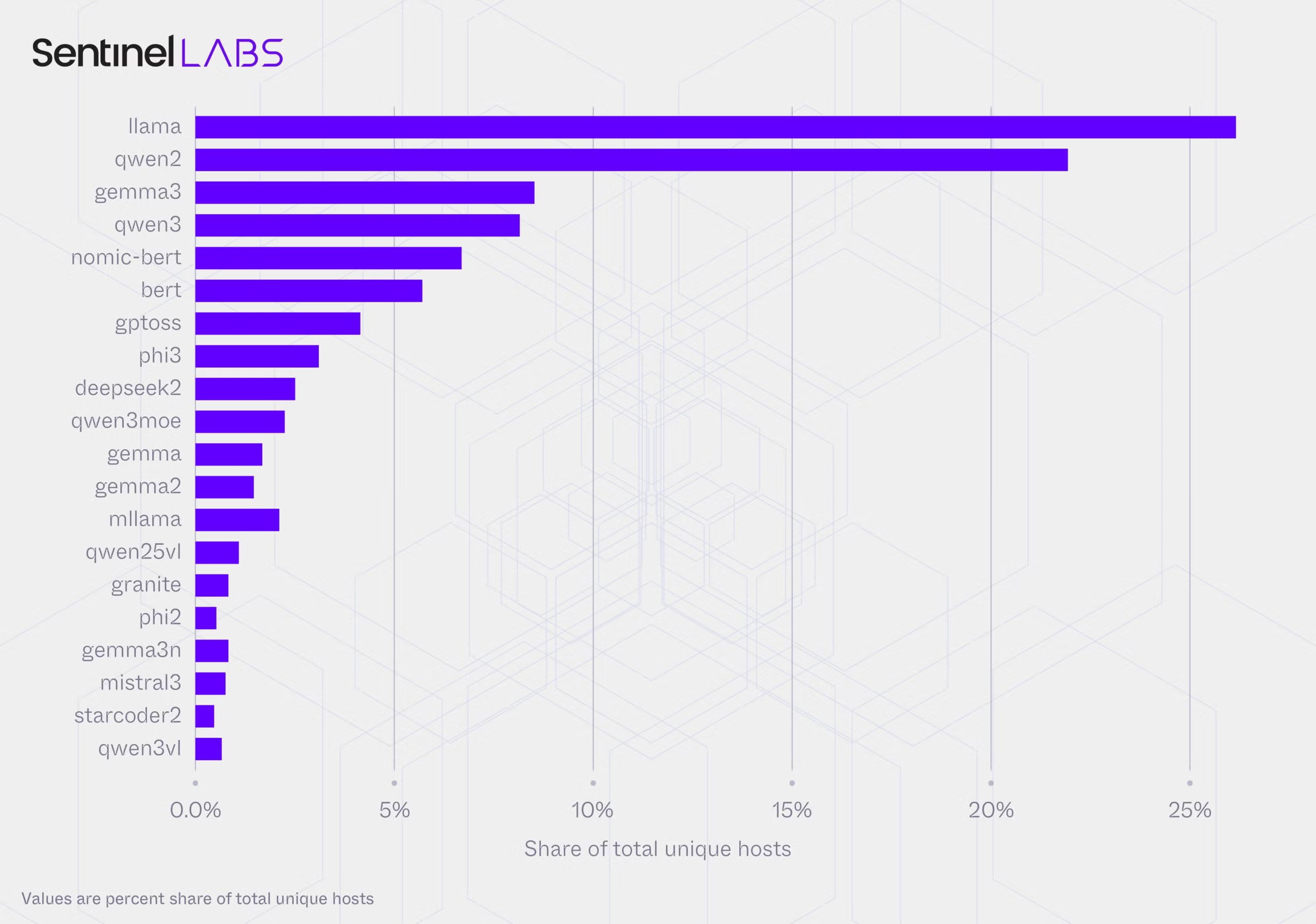
SentinelLABS and Censys revealed this week a sprawling network of 175,000 open-source AI systems hosted across 130 countries, warning that these exposed systems lack basic security protections like authentication and monitoring that major AI platforms implement by default.
Over 293 days of scanning, researchers identified a persistent core of 23,000 systems generating most activity, with many configured to execute code, access external systems, and process images. The systems are concentrated in cloud services and residential networks, where their IP addresses appear as legitimate household or business traffic, making it difficult to trace malicious activity back to attackers.
The research highlights how attackers could commandeer these unauthenticated systems to generate spam, phishing emails, and disinformation campaigns while appearing to operate from trusted networks. Researchers found at least 201 systems explicitly configured with safety guardrails removed. Because these systems lack authentication, attackers can access them at no cost while victims pay the infrastructure bills.
The researchers say the vast, unmanaged layer of LLMs represent a “governance inversion”: The systems are scattered across thousands of networks, but they all run the same handful of AI models. If one of those models has a vulnerability, it affects thousands of systems at once, but there’s no single entity responsible for securing all those deployments.
The researchers conclude that those running self-hosted AI systems should secure them with the same authentication, monitoring, and network controls used for other externally accessible infrastructure. However, the research notes that residential deployments require different approaches, as home users aren’t held to the same security requirements as businesses running AI systems on cloud infrastructure.
The Ugly | Newly Patched Microsoft Office Zero-Day Allows Security Feature Bypass
Microsoft has released emergency out-of-band security updates to address a high-severity zero-day vulnerability in Office, tracked as CVE-2026-21509 (CVSS score: 7.8). The flaw is currently being exploited in the wild and affects Office 2016, 2019, LTSC 2021, LTSC 2024, and Microsoft 365 Apps for Enterprise.
CVE-2026-21509 is a security feature bypass flaw that allows attackers to exploit COM/OLE controls in Office. Attackers send malicious files to targets and use social engineering techniques to convince victims to open the documents. The exploit is possible because Office relies on untrusted inputs when processing COM/OLE controls, enabling low-complexity attacks that require no authentication.
Microsoft’s advisory states that Office 2021 and later are automatically protected via a service-side update, but users must restart their apps.
For Office 2016 and 2019, users must install specific updates. Microsoft has also outlined a Registry-based mitigation, requiring creation of a {EAB22AC3-30C1-11CF-A7EB-0000C05BAE0B} subkey under COM Compatibility and adding a Compatibility Flags DWORD with a value of 400.
The vulnerability has been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, and the agency mandates that federal entities must patch affected systems by February 16, 2026.
As attackers continue to target Microsoft’s suite of products to access sensitive business data, users are advised to prioritize updating Office, applying Registry mitigations if needed, and exercising caution with untrusted Office documents to prevent compromise.
This update follows January 2026 Patch Tuesday, which addressed 114 flaws, including one other actively exploited zero-day in Desktop Window Manager enabling attackers to read memory addresses linked to remote ALPC ports.