The Good | Authorities Crackdown on BlackCat and Coinbase Malicious Insiders & Malware Operators
Two former employees from Sygnia and DigitalMint have pleaded guilty for participating in ransomware attacks linking them to the BlackCat (ALPHV, AlphaVM) operation. Ryan Goldberg and Kevin Martin admitted to conspiring to extort U.S. organizations, abusing the same security expertise they once used to defend cyber victims. Working with a third accomplice, they breached multiple companies nationwide and shared roughly 20% of ransom proceeds for access to BlackCat’s infrastructure. Prosecutors say they demanded between $300,000 and $10 million per victim.
Alternative to insider risk at the highest technical levels, similar threats are emerging from much lower in the access chain, too. Indian authorities arrested a former customer support agent for aiding threat actors in the May data breach at Coinbase, a popular cryptoexchange with more arrests are expected. The incident exposed data from roughly 69,500 users after bribed staff at outsourcing partner, TaskUs, enabled access. This news follows charges against Ronald Spektor, accused of stealing $16 million by impersonating Coinbase, highlighting ongoing insider and social engineering risks.
We have zero tolerance for bad behavior and will continue to work with law enforcement to bring bad actors to justice.
Thanks to the Hyderabad Police in India, an ex-Coinbase customer service agent was just arrested. Another one down and more still to come.
— Brian Armstrong (@brian_armstrong) December 26, 2025
Beyond insider abuse, attackers are also exploiting everyday user behavior to siphon funds at massive scale. A Lithuanian national was arrested for allegedly infecting 2.8 million systems with clipboard-stealing malware disguised as KMSAuto, an illegal Windows and Office software activator. The suspect used clipper malware to swap cryptocurrency addresses and divert funds to attacker-controlled ones. Korean National Police Agency says the campaign ran from 2020 to 2023, with a total of KRW 1.7 billion ($1.2M) stolen across thousands of transactions. Authorities warn that pirated software is often a key component in how attackers spread malware.
The Bad | Chinese-Based Attackers Deploy Stealthy Kernel‑Mode ‘ToneShell’ Backdoor
Security researchers have uncovered a significantly more stealthy variant of the ToneShell backdoor, a tool long associated with Chinese state-sponsored cyberespionage activity, now delivered via a kernel‑mode loader for the first time. New analysis links the campaign to G0129 (aka Bronze President, TEMP.Hex, Hive0154), a threat actor known for targeting government agencies, NGOs, and think tanks.
The activity, observed since at least February, primarily targets government organizations across Asia, particularly in Myanmar and Thailand. Investigators have found evidence that some victims had previously been compromised by earlier ToneShell variants, PlugX malware, or the ToneDisk USB worm, indicating long‑term persistence across multiple intrusion waves.
What sets this campaign apart is its use of a malicious kernel‑mode mini‑filter driver, ProjectConfiguration.sys, signed with a stolen or leaked digital certificate originally issued to Guangzhou Kingteller Technology Co., Ltd and valid between 2012 to 2015. Operating deep within the Windows kernel, the driver acts as a rootkit: evading static analysis by resolving kernel APIs at runtime, blocking file deletion and registry access, protecting injected processes, and deliberately interfering with Microsoft Defender by manipulating the WdFilter driver’s load order.
The driver ultimately injects two user‑mode payloads, including the updated ToneShell backdoor, which now features enhanced stealth capabilities. Changes also include a simplified host‑ID scheme, network traffic obfuscation using fake TLS headers, and remote administration capabilities such as file transfer and interactive shell access. Communication occurs over TCP port 443 to an attacker‑controlled infrastructure.
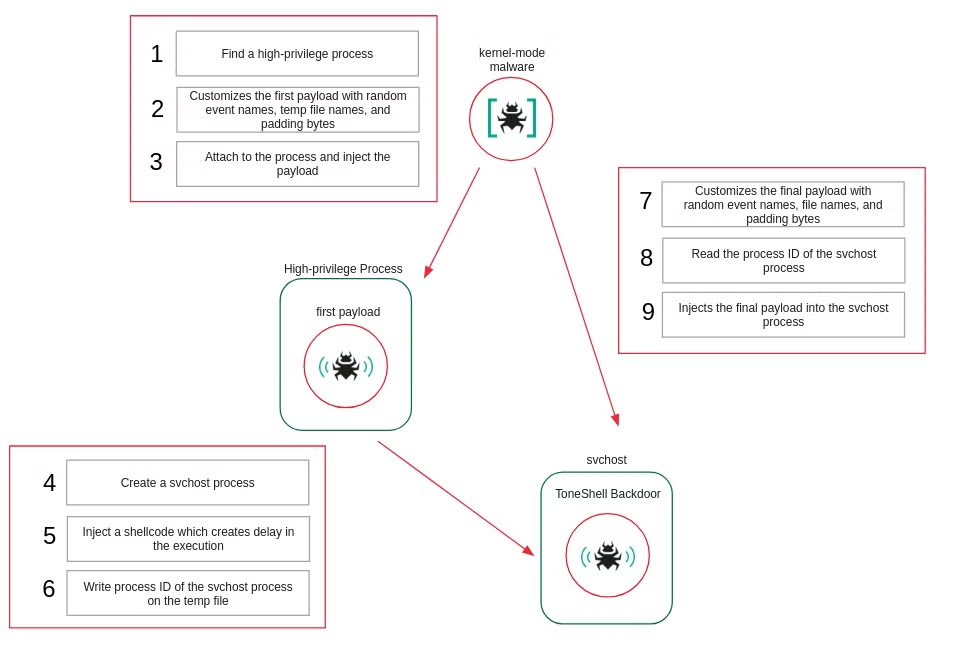
Researchers note this marks a clear evolution in G0129’s tactics, prioritizing kernel‑level persistence and evasion. As the payload operates almost entirely in memory, memory forensics becomes a critical detection method, alongside monitoring for indicators of compromise tied to the malicious driver and injected shellcode.
The Ugly | Hackers Steal $7M via Compromised Trust Wallet Chrome Extension
After a compromised update to the Trust Wallet Chrome extension went live over the holidays, approximately $7 million has been stolen from nearly 3,000 cryptocurrency wallets. The malicious version 2.68.0 contained a hidden JavaScript file called 4482.js that silently exfiltrated sensitive wallet data, including seed phrases, to an external server, api.metrics-trustwallet[.]com. Users immediately reported funds disappearing after simple wallet authorizations, prompting Trust Wallet to investigate and release a patched version 2.69. CEO Eowyn Chen confirmed the hack and assured users that the company would reimburse affected wallets.
Investigations indicate that attackers likely exploited a leaked Chrome Web Store API key to publish the malicious extension, bypassing Trust Wallet’s standard release procedures. In parallel, threat actors launched a phishing campaign using a Trust Wallet-branded site, fix-trustwallet[.]com, claiming to provide a “vulnerability fix”. Users who entered their seed phrases on the site immediately lost access to their wallets. WHOIS records suggest the phishing domain may be linked to the same actors behind the malicious extension.
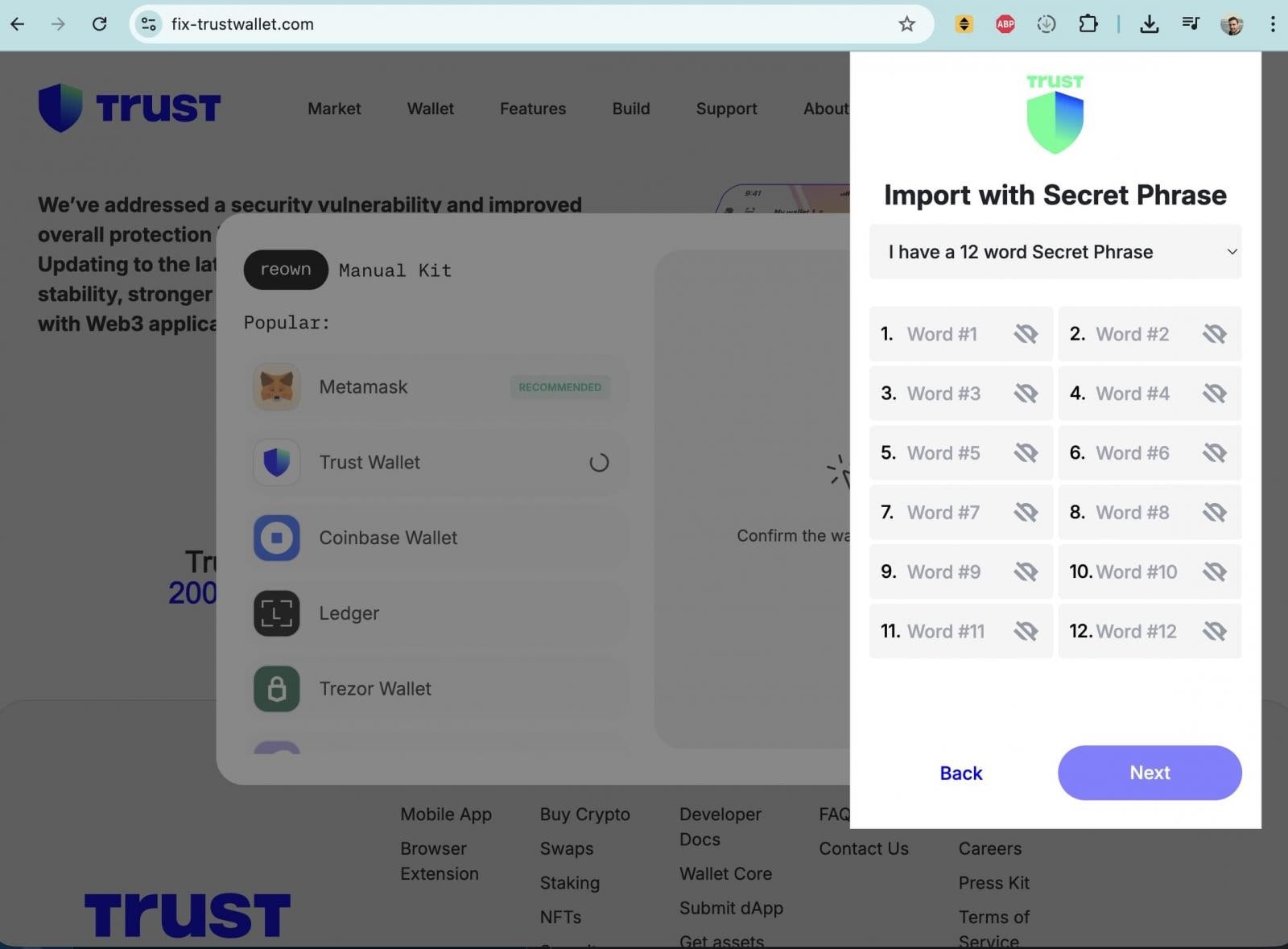
Trust Wallet, a non-custodial cryptocurrency wallet acquired by Binance in 2018, emphasized that mobile-only users and other browser extension versions were not affected. The company has begun reimbursing victims after verifying wallet ownership, transaction hashes, and affected addresses, while warning users not to share private keys or seed phrases.
Security researchers noted the incident highlights significant risks in browser-based wallets and supply chain attacks, as malicious updates can gain privileged access to funds. Trust Wallet has suspended compromised API keys, reported the malicious domains to registrars, and continues monitoring for scams. Users are strongly advised to immediately update to version 2.69, only use official channels, and verify all communications to protect their crypto assets.


