For the last decade, digital transformation has been fueled primarily by the adoption of cloud services which provide unmatched agility and reduced time to market when compared with legacy on-premises infrastructure. Most organizations have invested in public and hybrid cloud architectures to stay competitive, with nearly 94% of organizations using at least one cloud service. The COVID-19 pandemic has only accelerated plans to move to the cloud as security, high-priority and IT teams scaled to meet the demand for IT resources for a remote workforce.
Agile development practices that emphasize iteration and speed can overwhelm security teams who are not prepared to secure workloads as fast as they are created. This friction between DevOps and SecOps creates bottlenecks and an incentive for development teams to circumvent security and governance processes. As a result, there are often blind spots for security teams tasked with keeping cloud environments secure.

Cloud Misconfigurations on the Rise
Governance of workloads is often performed once when the workload is deployed, or sometimes not at all. And the specific configuration of workloads is inconsistent, with many instances deployed without critical controls. According to the State of Cloud Security 2021 report, misconfigurations remain the number one cause of cloud breaches.
Under the AWS Shared Responsibility Model, the customer is responsible for configuring resources so that they are secure. While cloud adoption is rising, legacy security tooling designed for on-premises environments has failed to keep up and is not suited for cloud environments. One such technology is traditional vulnerability scanning and assessment tools, which rely heavily on on-premises appliance deployments and bandwidth-heavy scanning. This approach is insufficient for security teams looking to embrace the cloud with the confidence of knowing that their critical applications and services are configured in a secure manner.
Even organizations that have a vulnerability scanning tool deployed to their cloud environments often struggle in three areas:
- Observability: Ingesting infrastructure vulnerability data and correlating with EDR telemetry from within the application workload
- Operationalize: Visualize the most critical vulnerabilities to prioritize remediation
- Actionability: Performing remediation across the cloud environment at scale
Cloud-Native Approach to Vulnerability Assessment
Vulnerability assessment for AWS workloads hasn’t been straightforward until now, with the launch of Amazon Inspector.
Amazon Inspector is a vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure. With a few clicks in the AWS management console, you can enable Inspector across all accounts in your organization. Once enabled, Inspector automatically discovers all running Amazon EC2 instances and container images residing in Amazon Elastic Container Registry (ECR) at any scale and immediately starts assessing them for known vulnerabilities.
An Inspector risk score is created for each finding by correlating Common Vulnerabilities and Exposures (CVE) information with factors such as network access and exploitability. This score is used to prioritize the most critical vulnerabilities to help increase remediation response efficiency.
All findings are aggregated in a newly designed Inspector console and pushed to AWS Security Hub and Amazon EventBridge to automate workflows. Vulnerabilities found in container images are sent to Amazon ECR for resource owners to view and remediate. With Inspector, even small security teams and developers can ensure infrastructure workload security and compliance across your AWS workloads.
Inspector creates a list of prioritized findings for security teams to prioritize remediation based on the impact and severity of vulnerabilities. These reports can provide valuable insights into opportunities for security and cloud teams to reduce their overall cloud attack surface.
SentinelOne Integration for Amazon Inspector
Today, we are delighted to introduce the SentinelOne Integration for Amazon Inspector, which provides support for Amazon Inspector findings with the SentinelOne Data Platform. The SentinelOne Data Platform is a massively scalable, cloud-native logging and analytics platform built on AWS that is designed to ingest, normalize, correlate, and action limitless datasets.
SentinelOne integrates with Amazon Inspector to provide unified visibility of vulnerabilities within AWS infrastructure. SentinelOne ingests Amazon Inspector findings from Amazon EventBridge and correlates against logs from additional security and DevOps data sources. The SentinelOne Data Platform provides powerful querying and threat hunting features to make searching and pivoting within the datasets simple for security and cloud teams.
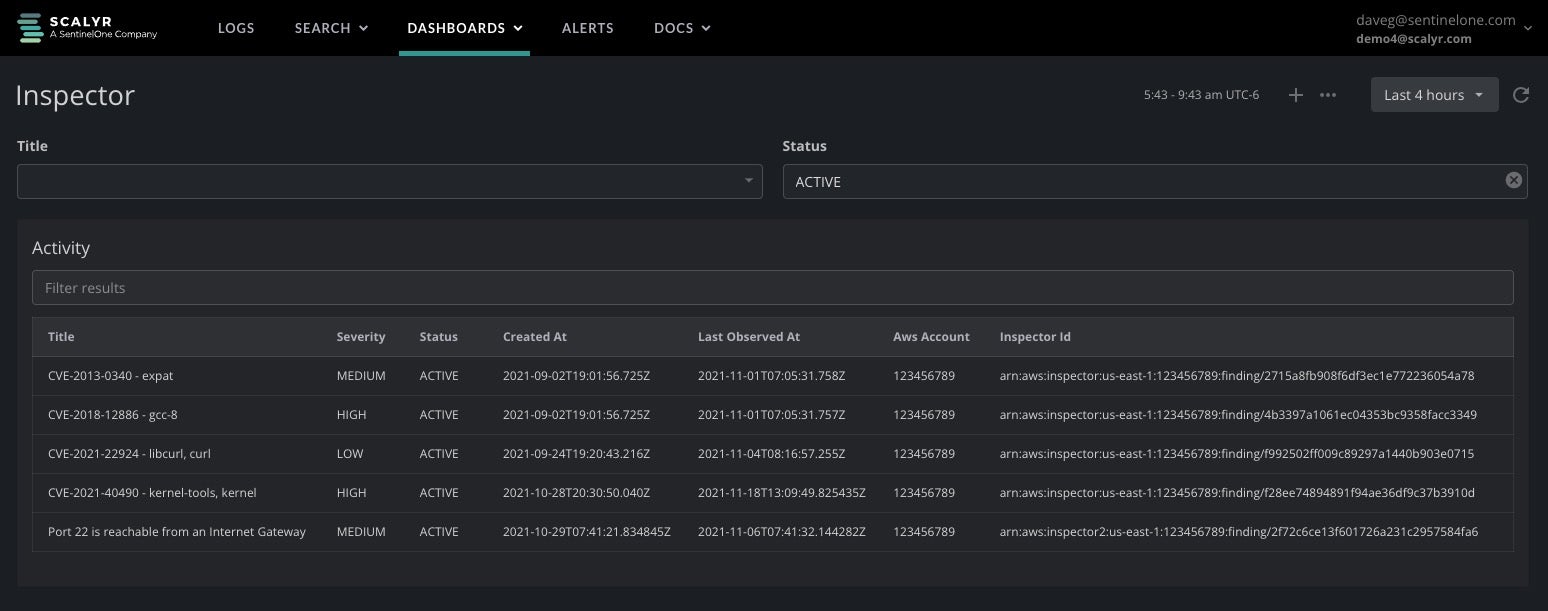
Within SentinelOne, analysts can use prebuilt dashboards to view high priority vulnerabilities from Amazon Inspector. Data from Inspector is enriched with links to view additional information about CVEs from the MITRE National Vulnerability Database. With this data, analysts can view the most common vulnerabilities within their environment, the most severe, and additional context about a given CVE from a single pane of glass.
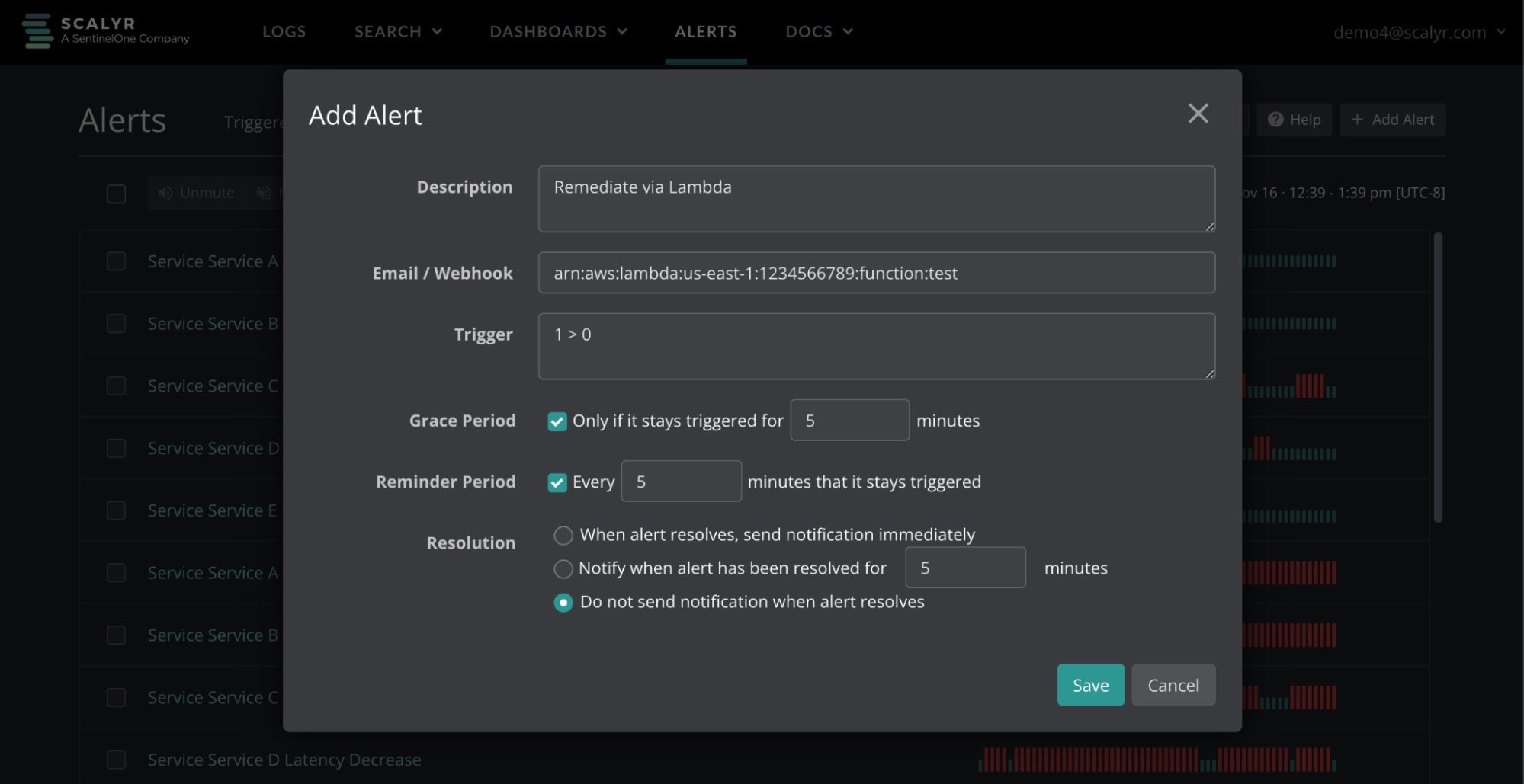
When a vulnerability needs to be remediated, the SentinelOne Data Platform’s alerting is ready with native support for AWS Lambda, EventBridge, SQS, and SNS — allowing you to not only identify issues quickly but accelerate vulnerability remediation.
By interacting natively with AWS, you can leverage existing remediation patterns and curate them, if needed, to fit your business rules.
Bridging Workload Protection and Vulnerability Assessment
Vulnerability management is a crucial activity for maintaining good security hygiene. While prioritizing and remediating vulnerabilities will go a long way towards reducing the total attack surface, legacy custom applications lifted and shifted to the cloud may not be able to be updated fast enough to address open vulnerabilities. Regardless of the application, workloads within cloud environments should have measures to protect, detect and respond to active threats from vulnerabilities that may have been exploited.
Cloud VMs, cloud instances, and containers are just as vulnerable to known vulnerabilities, zero-day attacks, and malware as user endpoints. Runtime protection, detection, and response are critical to effective cloud workload security. Singularity Cloud Workload Security includes enterprise-grade protection, EDR, and Application Control to secure your cloud apps wherever they run. Our Linux Sentinel and Windows Server Sentinel deliver runtime security for VMs, and our Kubernetes Sentinel provides runtime security for managed and self-managed Kubernetes clusters.
A single, resource-efficient, Sentinel agent delivers autonomous runtime protection, detection, and response across the hybrid cloud estate. SentinelOne brings runtime security to Amazon EKS, Amazon EKS Anywhere, Amazon ECS, and Amazon ECS Anywhere, with automated kill and quarantine, application control, and complete remote shell forensics.
SentinelOne Singularity uses Behavioral AI to evaluate threats in real-time, delivering high-quality detections without human intervention. Our solution automatically correlates individual events into context-rich Storylines™ to reconstruct the attack and easily integrates threat intelligence to increase detection efficacy. Analysts can remediate all affected endpoints and cloud workloads with a single click, without the need to write any new scripts, simplifying and reducing mean time to respond.
Preserving the immutable state of production cloud workloads is a key control to protecting them against malware like crypto-jacking coin miners and zero-day attacks. All expected processes are defined within the workload image. When a change is to be made, instead of updating an image already in production, DevOps decommissions the old and releases a new image.
The SentinelOne Application Control Engine prevents your workload from being hijacked by rogue processes by automatically detecting and killing any executable not found in the image, reducing the possibility of a successful vulnerability exploit.
With SentinelOne Integration, customers can unify cloud workload protection with vulnerability insights from Amazon Inspector. Context-rich EDR telemetry can be queried alongside vulnerability information from Amazon Inspector, giving security analysts a single dataset for identifying open vulnerabilities and detecting successful vulnerability exploits.
Conclusion
Using SentinelOne Integration to connect Amazon Inspector findings with cloud-native protection for AWS workloads, organizations can use best-in-breed solutions to identify vulnerabilities proactively and detect and respond to active exploits of vulnerable applications. Together, security and DevOps teams can innovate rapidly, securely and embrace cloud adoption with confidence.
To learn more about SentinelOne for AWS, visit s1.ai/AWS.


