BlackNevas Ransomware: In-Depth Analysis, Detection, and Mitigation
What Is BlackNevas Ransomware?
BlackNevas (aka “Trial Recovery”) is a ransomware family that was first observed in November 2024. BlackNevas is a derivative or variation upon the Trigona ransomware family. BlackNevas operators focus on extortion and profit, with less emphasis on naming and shaming of victims. As of this writing, the group does not host their own data leak site (DLS) but they claim to ‘partner’ with other ransomware operations to facilitate data leaks and hosting of stolen data. This partner list includes Kill Security, Hunters International, DragonForce, Blackout, Embargo Team, and Mad Liberator.
What Does BlackNevas Ransomware Target?
BlackNevas attackers do not discriminate when it comes to victimology outside of targeting large enterprises. Currently, financial institutions as well as those in the telecommunications, manufacturing, medical, and legal industries are all known targets of BlackNevas campaigns.
How Does BlackNevas Ransomware Work?
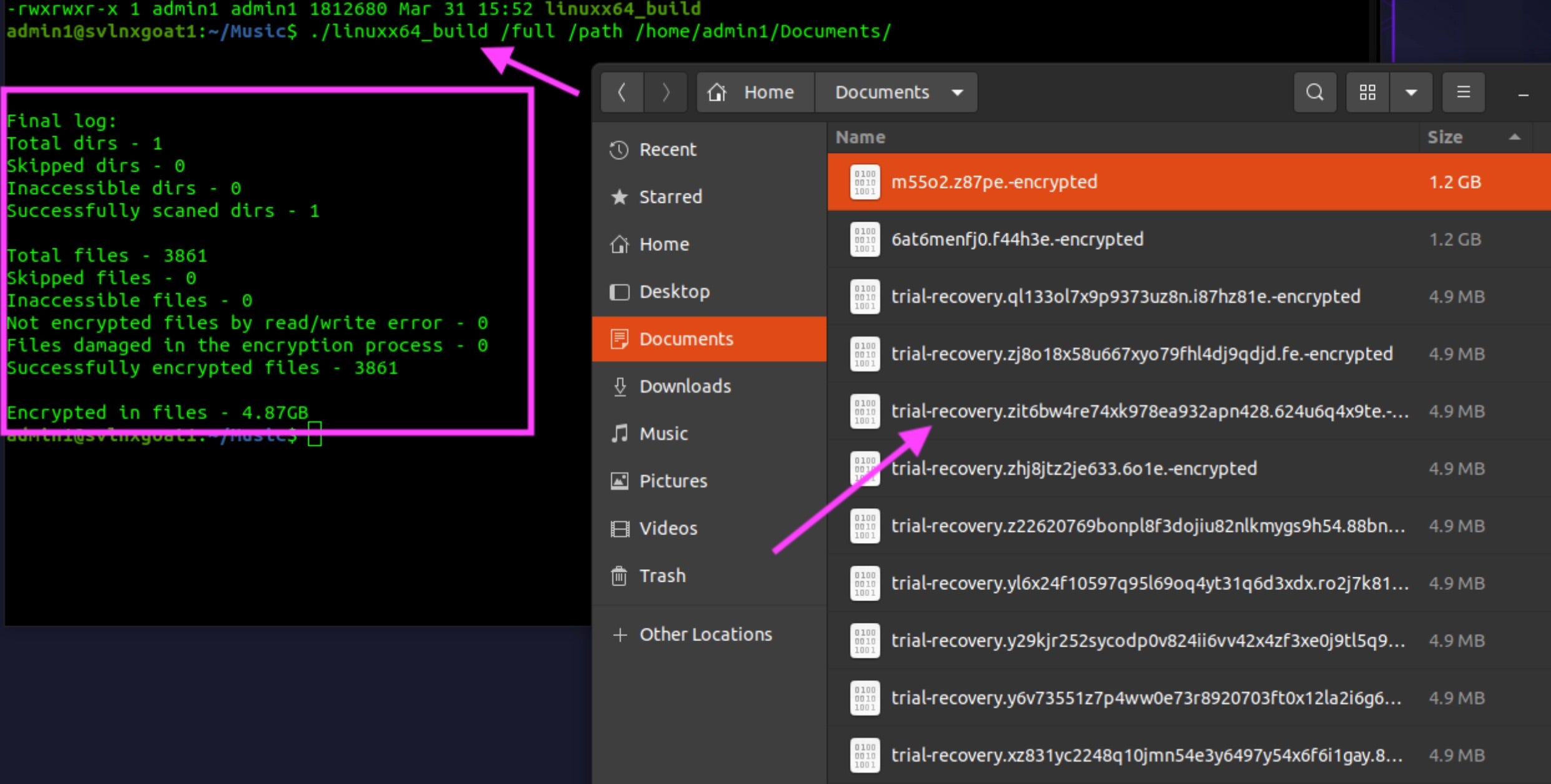
BlackNevas payloads are built to support multiple platforms and environments. Basic Widows and Linux payload support exists, alongside versions tailored for NAS encryption and ESXi. Additionally, multiple architectures are supported within each OS family. For example, there are 64 and 32-bit Windows and Linux encryptors along with ARM payloads.
Initial delivery methods of BlackNevas payloads vary across campaigns. Deployment via spear phishing as well as exploitation of known vulnerabilities has been observed. Analyzed samples of BlackNevas ransomware exhibit the same basic underpinnings and encryption methods found in Trigona ransomware. Generally, file encryption is handled via a combination of AES-256 (symmetric key) and RSA-4112 (public key) in OFB (output feedback) mode.
BlackNevas ransomware configuration data is embedded within each payload. The configuration data is encrypted using multiple layers of AES in CBC mode. Encrypted files are modified, adding the .-encrypted extension (sometimes capitalized to .ENCRYPTED) to affected files. The .-erased extension is applied in the event that the ‘/erase’ option is used with the ransomware payloads.
The malware attempts to achieve persistence via Registry Run keys. Like Trigona, BlackNevas ransomware has SMB enumeration/spreading capabilities. This capability can be toggled on and off (/!lan and /!local) in current generations of Trigona and BlackNevas ransomware. Additional command-line arguments are supported as well.
The following commands are available in the current Windows generation of BlackNevas ransomware payloads. Most of these are implemented across both Windows and Linux platforms. These same parameters/arguments are also present in later versions of Trigona.
/!lan – Do not attempt to encrypt files over network shares
/!local – Do not encrypt local files
/log – Standard verbose log output (txt file)
/short_log – Reduced output (not every function called)
/erase – Overwrite data. The first 512KB is by default, but this option can be used with the /full argument
/full – Full file encryption (as opposed to the first 512KB)
/is_testing – Sets testing/debugging flag
/path – specified path for encryption (recursive)
/shdwn – Initiate system shutdown post-encryption (shutdown.exe -f -s -t 00)
/test_cid – Force use of specified computer ID (testing)
/test_vid – Force use of specified victim ID (testing)
/debug – verbose output, execute in debug mode
/allow_system – enable encryption of files in System directory
/wipe – overwrite (wipe/erase) files
/depth – Sets recursion depth when /path is used.
/!prerename – disable renaming of files prior to encryption process
/delete – same as /wipe
/notkill – disable termination of processes or vms (depending on build)
/priority – sets encryption (process) priority
/stealth – Executed with /path, does not rename files. ‘Stealth encryption’
/clear_exclude
/notcmd
/ips
NAS and ESXi-focused builds have specialized parameters as well, including:
/nohup – Execute and exit (while encrypting as a background process)
/do_not_poweroff – Disable Power-down/shutdown (vm) post-encryption
/chattr-i – Make files non-modifable (immutable)
/detach – Detach session from screen / terminal
Most of the Linux/ESXi/NAS focused builds of BlackNevas also require the /p or /path commands for proper execution.
The /erase feature can be utilized to approximate wiper functionality by attackers. The /erase option is combined with /path or /full as the attacker sees fit. This option renders targeted files unrecoverable.
BlackNevas ransom notes are written to disk, in each location containing encrypted files. TXT-formatted ransom notes are named “how_to_decrypt.txt”. Some encrypted files will have their name overwritten with “trial-recovery” followed by a string of characters. This is the source of the ‘Trial Recovery’ name that some apply to this malware family.
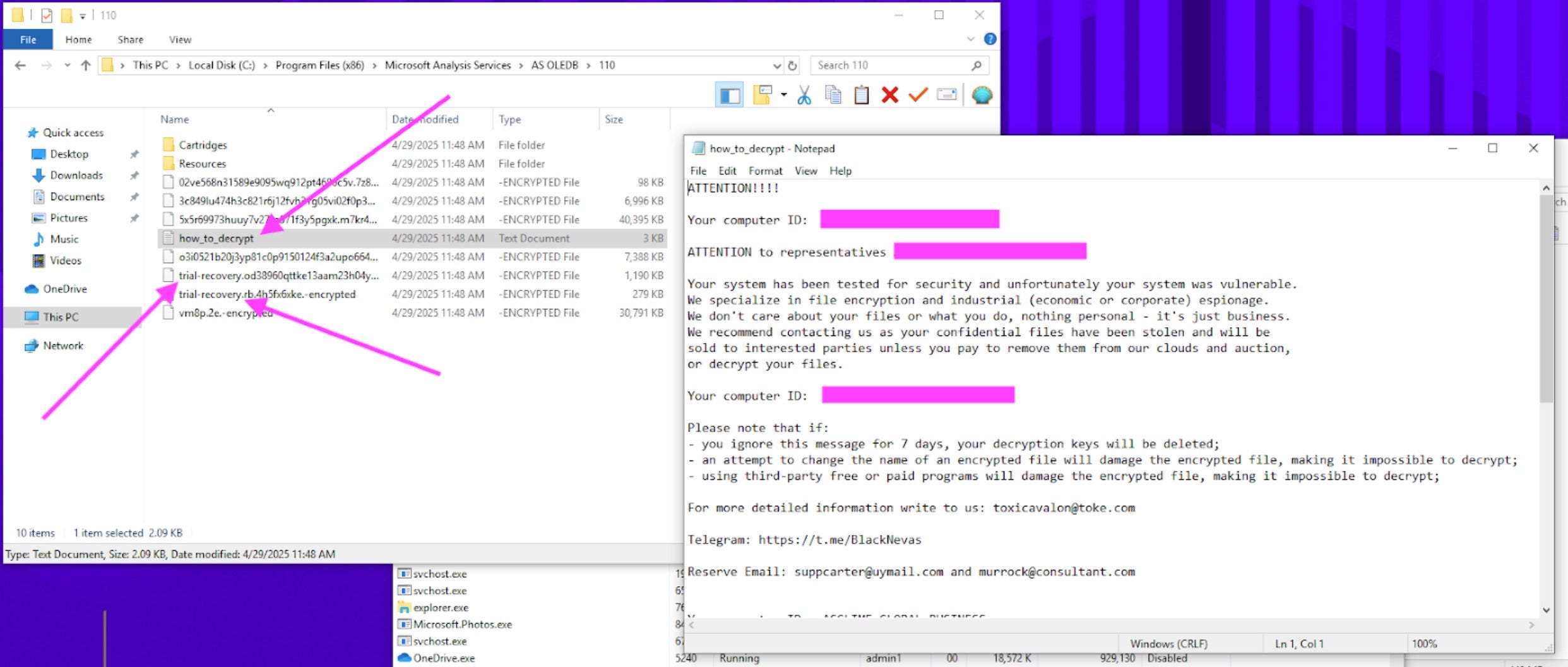
BlackNevas ransom notes instruct victims to email the threat actor via victim-specific email addresses that are included in the Ransom notes. BlackNevas ransom notes typically contain the victim names as well.

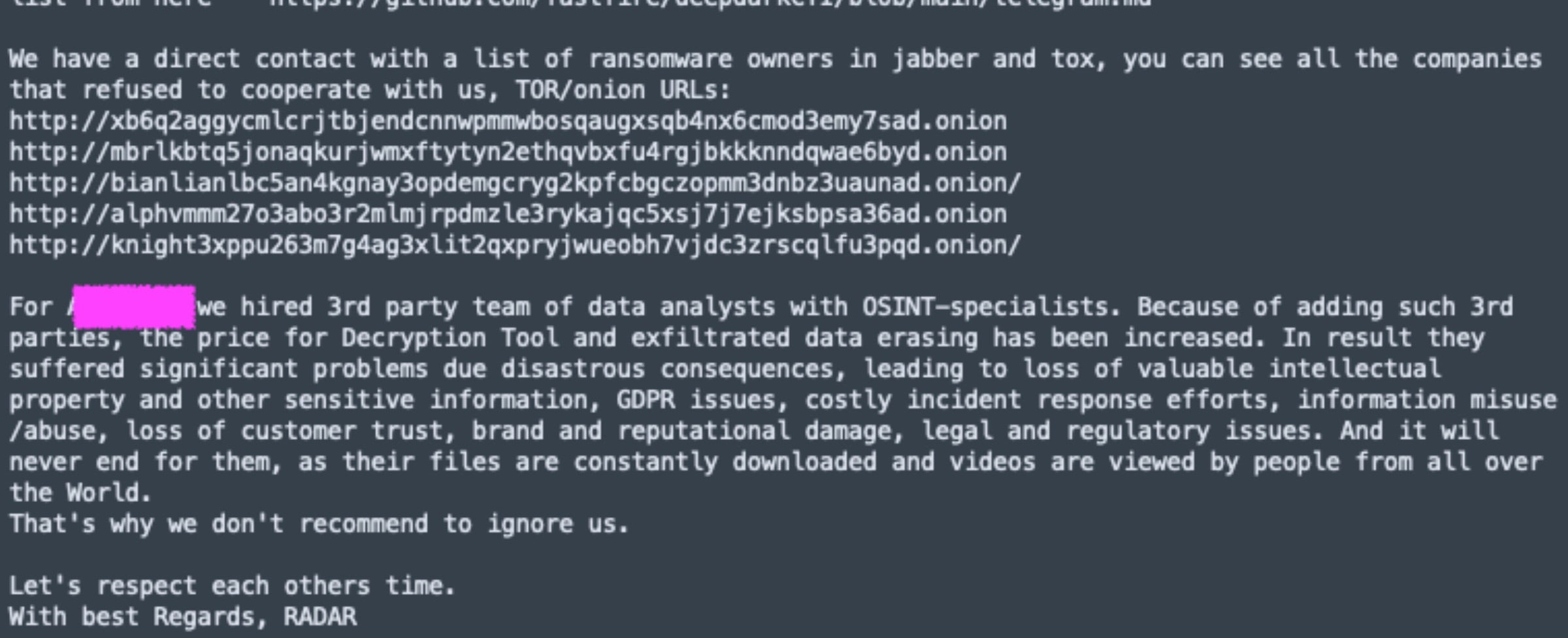
The ransom notes also contain links (.onion) to their ‘partner’ sites. Should victims fail to comply, the ransomware operator threatens to post to one of their partners’ DLSs. This approach is similar to the Dispossesser/RADAR model. While we do not currently believe there is any relationship between RADAR and BlackNevas, it is of value to note the similar approach in ransom notes.
This type of operational model involving extortion and partnership with others for leaks is expanding and gaining momentum. RADAR/Dispossessor, for examples, claims partnerships with groups including BianLian, ALPHV (BlackCat), and Knight.
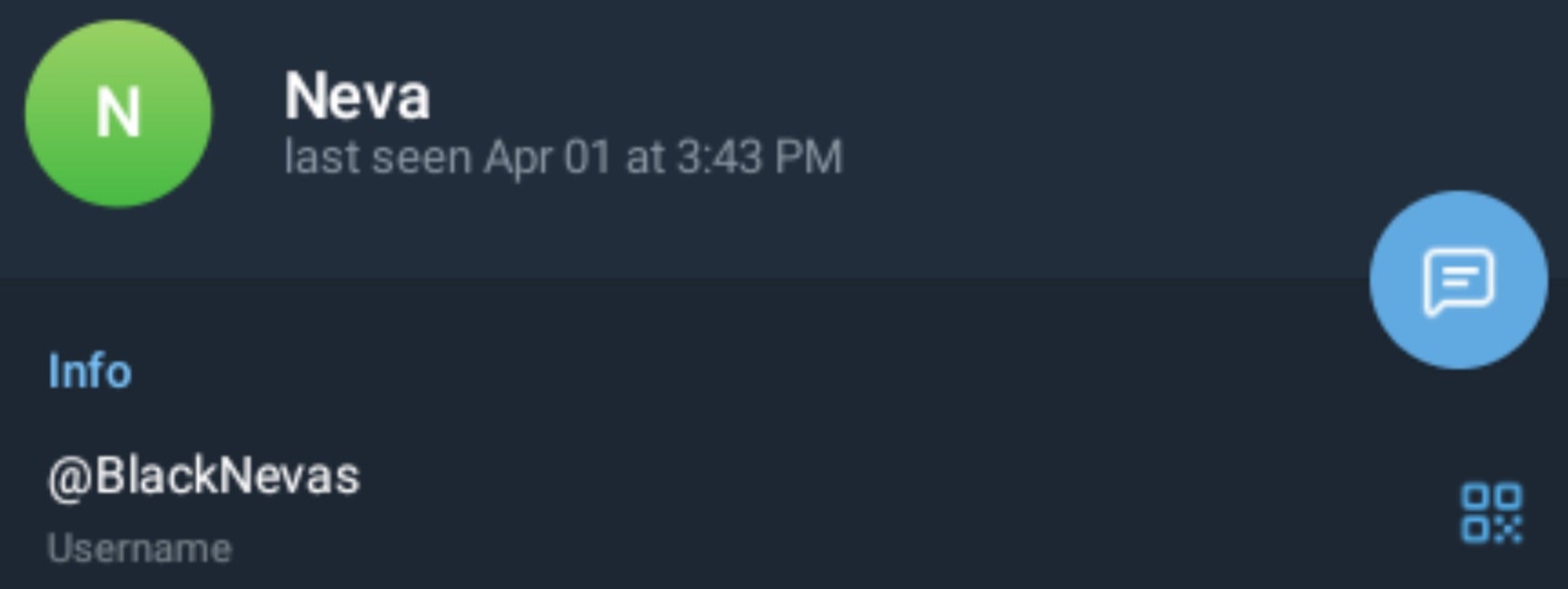
Unlike Trigona, BlackNevas directs victims to a Telegram channel for communications along with victim-specific email addresses. The “@BlackNevas” Telegram contact is included in BlackNevas ransom notes.
IOCs
SHA1
203f81cbe35c64071f52f34afbbbfc7d61b3e702
2a79c999e20c5d8102e0b728733cc8eba2b4d8ac
3226ebfc23dbe1a6cc44c3255d1a0e12f0dd153c
3ff7aedacf36f96fef42391aaadb2c63820bef7f
49551cb0bbc2da3f6d36523a005af5ee1f5ad1a8
499cd23b37a00b9a8ad212f879501705baad1781
4d5605008bd0619a5980c4633889d7c253093360
4db3b2876ef5c8e5ea977d8ffedef428b93408a4
61c56c25f5ca4bee336aa30e89123eb2daf5166a
646533556a16a9d17bd7ad2265873bc8f1ccb4f4
67750b2b0b90572ade6ef760bcded1ef5fc09982
781a8e52c2399c07ca4853def924d79be5182b32
7b3cbd60020c1d155b12271881d69c968fcde04f
7bf79cc58fb8f3d0ec774cb8b9e8ce311cbc27d2
7c4f10d85607e65386fb504446b45419901c5276
812d65b67ce28905f5e07ac1f82b827ebd36470a
88aee839de69ce1602ef2bb401a6cabb6b376e19
8cbbcbe187ff66c44908a205236d4230931f7d73
923be026c79e7b5b5d29461420887fe2e8875b01
92b0ce569d838cd9b773cc13b6b6ea5609e85fd7
B00897AE5B116680CCDD2E43A3A9599D8C3E166E
b8c85fa5a81b3d70a21835fbea394e0611461bf8
c1c9008b4be855583df0f04204443262a3fbc8ab
cd2f25a8ab74bdc17d7c8170f2c4135537ece3c4
cdb07718787743ceb488b5bd184d9a4939c12dbf
d026954e6f646b84943f8514be606650be8c18bb
dc6d4f0a88ea0458926ff8f57dbd8239ed140824
ebf63e7a27c91f96d84b66d7ba435ddc3a153b71
2d8e9ea39b9853d5676957a51f09f14d3703d1bd
d6e1a47a0cf9bc94a816149f6e1f1a04c53f99d1
1b14a60d50622a7c846f9e81d9668b4962fc356b
70e9b61e0a8e708e8512c54f96b90b32bac38984
a35b2be3167b72c73b2f8f9ac058576cf080f752
1c0620a81f8cfb3c2a8b073b7e5a5c2329b511a5
f7d2d8fd75a62a9ce4533196b13f9ba55e985b62
3b8185e491bbfe4ba0583f3a5810674aeaff26ad
1ad51a365293269da14fd6914c3014fb3556f69f
a61aaf88253bfb4bd80e0ca7bbaf4a78e6bb2591
67a078a7d703308e3c0eb2af7ea0c288453cd705
80ad69638820c264552e5f73ed696f88614fa3bd
cbe2b0cfa599fe7477ebbe92feaadb54b5b25deb
ad63f0652ce21b0dac5284158cf301410f57d0f9
f7ac2604e6e186a647318544c36ba5758cdcb85a
97fa0c24f75164940717672f22643ba31161c638
f18b501eca2a7390705967a24f67b808b43d2212
8dfd14d230d93ff6eea3dd09934ebf9c9e860a0f
93ba61e1b7d12277e0bcee27ec7f37a74d8f1c97
119388459d68d2781b843e1db71be8f5e01e965a
0a33ed85842cf189f96ae9ea804a2e0789200430
3bcf26bb616c57330da226f5db4e89bb609147e8
827c01503a92b1e202939ae5a0e3e4d5ff02f4ae
2e2046d5e8fb4ccc18f7fdf1a4dd076bf2333417
18af0b641e456ed5df3908f2e2fc16ea01fef0f2
1881f7bd1867e7d625e2ef2f0dc856437a376112
1b87e342d2fdd5cf5db3a8280bac92f90f099516
6b22150c7eeafd74dca41b749bf33f391401d094
a7da9e83c69a9deb6aa4de1fb0ec7d0badb4a426
67c0338c0a58493befc6c77c9f7fb16d753eb155
0b02e7c36714e9af519fd24bca893172afd2562d
aa10da9d601482262b87cb1e0748acca7a91c2a5
Email Addresses
amsomar[@]consultant[.]com
avalonsupp[@]consultant[.]com
biosannetsuabvg[@]mail[.]com
black4over[@]newlookst[.]com
compsupp[@]techie[.]com
corubete[@]dr[.]com
milford[@]usa[.]com
murrock[@]consultant[.]com
ovtaitonine[@]usa[.]com
suppcarter[@]uymail[.]com
toxicavalon[@]toke[.]com
varentsujikyuke[@]mail[.]com
widemoucerpco[@]mail[.]com
How to Detect BlackNevas Ransomware
The SentinelOne Singularity XDR Platform can identify and stop any malicious activities and items related to BlackNevas ransomware.
In case you do not have SentinelOne deployed, detecting BlackNevas ransomware requires a combination of technical and operational measures designed to identify and flag suspicious activity on the network. This allows the organization to take appropriate action, and to prevent or mitigate the impact of the ransomware attack.
To detect BlackNevas ransomware without SentinelOne deployed, it is important to take a multi-layered approach, which includes the following steps:
- Use anti-malware software or other security tools capable of detecting and blocking known ransomware variants. These tools may use signatures, heuristics, or machine learning algorithms, to identify and block suspicious files or activities.
- Monitor network traffic and look for indicators of compromise, such as unusual network traffic patterns or communication with known command-and-control servers.
- Conduct regular security audits and assessments to identify network and system vulnerabilities and ensure that all security controls are in place and functioning properly.
- Educate and train employees on cybersecurity best practices, including identifying and reporting suspicious emails or other threats.
- Implement a robust backup and recovery plan to ensure that the organization has a copy of its data and can restore it in case of an attack.
How to Mitigate BlackNevas Ransomware
The SentinelOne Singularity XDR Platform can return systems to their original state using either the Repair or Rollback feature.
In case you do not have SentinelOne deployed, there are several steps that organizations can take to mitigate the risk of BlackNevas ransomware attacks:
Educate employees: Employees should be educated on the risks of ransomware, and on how to identify and avoid phishing emails, malicious attachments, and other threats. They should be encouraged to report suspicious emails or attachments, and to avoid opening them, or clicking on links or buttons in them.
Implement strong passwords: Organizations should implement strong, unique passwords for all user accounts, and should regularly update and rotate these passwords. Passwords should be at least 8 characters long, and should include a combination of uppercase and lowercase letters, numbers, and special characters.
Enable multi-factor authentication: Organizations should enable multi-factor authentication (MFA) for all user accounts, to provide an additional layer of security. This can be done through the use of mobile apps, such as Google Authenticator or Microsoft Authenticator, or through the use of physical tokens or smart cards.
Update and patch systems: Organizations should regularly update and patch their systems, to fix any known vulnerabilities, and to prevent attackers from exploiting them. This includes updating the operating system, applications, and firmware on all devices, as well as disabling any unnecessary or unused services or protocols.
Implement backup and disaster recovery: Organizations should implement regular backup and disaster recovery (BDR) processes, to ensure that they can recover from ransomware attacks, or other disasters. This includes creating regular backups of all data and systems, and storing these backups in a secure, offsite location. The backups should be tested regularly, to ensure that they are working, and that they can be restored quickly and easily.
