Endpoint management is essential for maintaining the security and performance of devices within an organization. This guide explores the principles of endpoint management, including device monitoring, patching, and security policies.
 Learn about the tools and strategies that facilitate effective endpoint management and the importance of a proactive approach. Understanding endpoint management is crucial for organizations to protect their digital assets.
Learn about the tools and strategies that facilitate effective endpoint management and the importance of a proactive approach. Understanding endpoint management is crucial for organizations to protect their digital assets.
What is an Endpoint?
Endpoints are the physical devices connected to a network – laptops, smartphones, IoT devices, etc. An endpoint is the place where any internet-facilitated communication takes place, whether sent or received.
Most commonly connected to enterprise networks are desktop and laptop computers, devices which are also most likely to be the focus of endpoint security systems. In most organizations, at least one of the following endpoints is present:
- Internet of Things (IoT) Devices
- Desktops
- Servers
- Smartwatches
- Printers
- Tablets
- Medical devices
- Point-of-sale (POS) systems
- Workstations
Why Do Endpoints Need to be Managed?
Despite any differences between endpoints, they all have one important feature in common: they’re vulnerable to attackers. Every time an endpoint is used while connected to a network, it creates and exchanges data, which means it can also serve as an attack vector for cyber attackers. Endpoints are among the easiest entry points for cybercriminals and according to an IDC study, endpoints cause nearly 70% of successful breaches.
Once an attacker successfully gains entry to a network or system via an endpoint, they’re essentially free to execute malicious code, exploit unpatched vulnerabilities, or encrypt, exfiltrate, and leverage high-value assets. The more endpoint devices connected to a network, the more vulnerable that network is to cyberattacks. Each endpoint connected to a particular network contributes to what is often called an attack surface, or the sum of all the possible points an attacker might exploit to gain entry.
With the shift to remote work and an ever-increasing number of endpoints accessing networks at home, at work, and abroad, endpoints must be managed effectively for the most protection. Without endpoint protection in place, organizations risk giving cybercriminals easy access to their networks and systems and opportunities to conduct malicious activity.
Cyber attackers often target endpoints to:
- Access high-value assets via an organization’s network
- Access high-value assets stored on an endpoint
- Take control of the endpoint and use it in a botnet for a DoS attack
What cybercriminals do with high-value assets once they gain access varies, from selling sensitive information on the dark web to holding critical data hostage ransom, or even leaking internal documents to competitors. To prevent these and other cybercrimes from taking place, the best place for organizations to start is with endpoint security.
What is Endpoint Security?
Endpoint security refers to the cybersecurity tools and services that are used to implement endpoint management practices. Most endpoint security tools use advanced analytics to gather and monitor network activity across endpoints for indicators of compromise, remediate attacks, and remote threats.
Endpoint security services typically include antivirus software, email filtering, web filtering, and firewall services, any of which can come in the form of a client-server model or software-as-a-service (Saas).
No matter the service, the goal of an endpoint security solution is to detect and mitigate the risk of cyberattacks on endpoints.
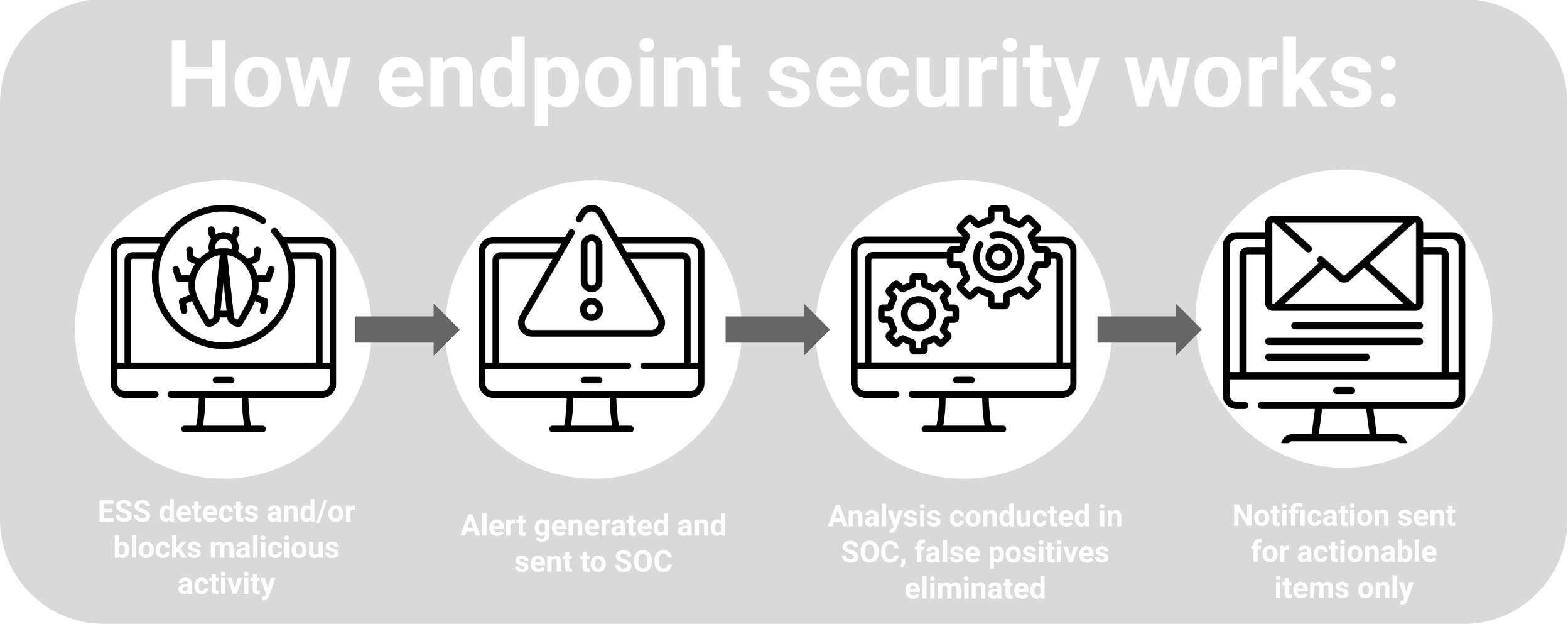
What Does Endpoint Security Do?
For most businesses today, endpoint security plays an important role in protecting critical systems, intellectual property, customer data, employees, and guests from cyber threats including ransomware, phishing, malware, and more.
Most organizations have relied heavily on antivirus as the main method for securing endpoints for decades, but many are finding traditional antivirus solutions are no match for modern sophisticated threats.
Modern endpoint protection platforms (EPPs) employ a variety of security capabilities to identify cyberattackers who bypass traditional security solutions, including antivirus software. Unlike other forms of endpoint security, EPPs provide organizations with more holistic defenses against a variety of threats, including zero-day exploits and fileless malware attacks.
Today, most EPPs are cloud-native, giving them the added advantage of agility with advanced monitoring and remote remediation. The majority of endpoint security solutions also tend to be behavior-centric and can incorporate a broad array of capabilities including antivirus, exploit protection, endpoint detection and response (EDR), analytics, and device control.
However, even the best endpoint security solutions are only as good as the methods organizations use to manage them.
What is Endpoint Management?
Like endpoint security, endpoint management is a core component of a comprehensive cybersecurity strategy. Together, endpoint security and endpoint management work in tandem to protect an organization and its endpoints from cyberattacks.
While endpoint security comprises the tools, technologies, processes, procedures and policies in place to protect endpoints, endpoint management refers to the overarching capability of ensuring that only authenticated and approved endpoints can connect to the network, and that they can do so only at the appropriate access level. Endpoint management also works to ensure an organization’s endpoint security policies and tools are enforced consistently across all devices.
Ultimately, endpoint management ensures network security by formally screening, authenticating, and monitoring endpoints with an endpoint management tool. Endpoint management tools are primarily used to manage devices and provide support, giving administrators the ability to oversee endpoint activities.
Most often, device management support activities are executed via MDM (Mobile Device Management), EMM (Enterprise Mobility Management), or UEM (Unified Endpoint Management) solutions and include the following:
- Managing system, software, and application updates
- Patching vulnerabilities
- Sending configurations, commands, and queries to endpoints
- Defining VPN and WiFi Configurations
- Managing or changing passwords
- Controlling devices through remote access
All endpoints need to be managed effectively to prevent cyberattacks. An advanced endpoint security platform can help. However, there are a few key differences to note.
Mobile Device Management (MDM)
As mobile devices become increasingly ubiquitous among enterprises, securing them in addition to traditional enterprise devices is equally important. Smartphones, tablets, and laptops are unique endpoints because they typically move across networks and are used to complete a wide variety of tasks.
Some enterprises provide employees with mobile devices and some enterprises permit employees to use their own personal devices to complete work. Either way, managing mobile devices is complex, and the practice has warranted its own category of endpoint management: mobile device management (MDM).
Because mobile devices used for work typically access critical business data, they often pose a serious threat to enterprise security, especially if a mobile device is hacked, stolen, or lost. Today, security teams are usually responsible for securing mobile devices, and many opt to do so using an MDM platform designed to keep devices secure while maintaining the flexibility and productivity of employees.
Like endpoint management, MDM combines the use of security software with processes and security policies to protect mobile devices’ applications, data and content.
Enterprise Mobility Management (EMM)
Managing mobile devices themselves is no longer enough to protect an organization from potential cyberattacks. Like MDM, enterprise mobility management (EMM) focuses on managing a variety of mobile devices used by employees, both on and off the enterprise network. More specifically, EMM refers to the management of mobile devices and mobile infrastructure components such as wireless networks, routers, and IoT devices.
Most EMM solutions vary widely from organization to organization, depending on their unique needs. While some focus on securing specific applications or limiting the applications that can be installed on devices, others are more compliance-centric, ensuring users are utilizing secure infrastructure before granting access to protected information or intellectual property.
As a holistic approach, EMM encompasses MDM, as well as mobile content management (MCM), mobile identity management (MIM), mobile application management (MAM), and mobile expense management (MEM). While MDM manages specific device features, EMM manages the entire mobile device.
Unified Endpoint Management
Unified endpoint management (UEM) refers to the software and tools used to authenticate and control all endpoints, typically with a centralized console to oversee all associated activity. Unlike MDM or EMM solutions, UEM tools allow users to manage all their endpoints in a single location, reducing the number of platforms needed to manage a wide variety of endpoints.
Typically, UEM dashboards provide a single-pane-of-glass experience for administrators, as opposed to managing various types of endpoints in silos. By incorporating mobile and remote device management, UEM solutions can simplify security patch deployment and software updates across multiple endpoints.
Endpoint Management Policies
Beyond device management and support, endpoint management typically incorporates a number of policies dictating device authentication and network access protocols. The best endpoint management policies begin with setting permissions for device access and include identity authentication protocols. Management policies may also include device-specific encryption tokens to ensure authenticity.
Some of the most common endpoint management policies include the following:
Bring Your Own Device (BYOD)
BYOD policies usually allow employees to bring their personal devices to work, or use their own devices to work remotely. BYOD models generally include mobile devices, laptops, tablets, and other portable endpoints.
For the most protection, organizations must ensure that personal devices are secured so they don’t introduce risk. However, because these devices belong to employees, securing them with far-reaching security measures or restrictions is more difficult.
Endpoint management teams are responsible for creating and implementing a clear BYOD policy, outlining how the organization will access personal devices used for work, and which applications and data will be subject to monitoring and analysis. Endpoint management teams also determine how they’ll enforce BYOD policies.
Privileged Access Management (PAM)
Using the Principle of Least Privilege to define and control users, PAM policies aim to minimize identity-based malware attacks and prevent unauthorized access of the network or other high-level assets.
While PAM policies tend to be effective, they are often burdensome to enforce. Managing access at the individual level can be a tedious task, and it doesn’t always provide the best protection for organizations. For example, if an attacker gained access to an administrator’s account, they would then have the ability to define and control privileges for all the other administrator accounts.
Zero Trust
Zero Trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated. It authorizes and continuously validates for security configuration and posture before granting access to applications and data.
Although Zero Trust policies can be frustrating for users at times, they ultimately provide the most security for organizations and their networks.
Endpoint Management Software
Endpoint security and endpoint management aren’t possible without endpoint management software. But investing in any security solution is a critical decision that requires careful consideration. The wrong product could create a false sense of security, which can lead to additional problems down the road.
Ideally, an endpoint management system should offer both local and autonomous access and functionality across multiple operating systems. It should also incorporate real-time threat monitoring, analysis, and response capabilities to form a multi-layered defense.
A cloud-managed endpoint management solution should enable continuous remote monitoring and remediation actions. Advanced EPPs use AI and ML to prevent sophisticated attacks by monitoring user behavior to sense unusual patterns of behavior and identify sources of potential attackers.
The best endpoint management solutions should be easy to manage – simplicity is key.
Gartner MQ: Endpoint
See why SentinelOne has been named a Leader four years in a row in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms.
Read Report
The Best Endpoint Management Solution
SentinelOne provides the only security platform with all the tools necessary to safeguard endpoints, data, and network assets with the most cutting-edge threat mitigation techniques in the cybersecurity world.
With multiple tiers of endpoint protection suited for diverse enterprise security needs, SentinelOne’s Singularity platform extends protection from the endpoint to beyond, all in a unified platform. By ingesting data from multiple sources, organizations get greater visibility of potential threats and unprotected endpoints across their entire system.
See why SentinelOne was named a leader by Gartner in the 2021 Magic Quadrant for Endpoint Protection Platforms and request a demo today.
Endpoint Management FAQs
Endpoint management is the process of overseeing and controlling all devices that connect to a network—laptops, smartphones, tablets, servers, and IoT gear. It uses centralized software to keep an up-to-date inventory, deploy patches and updates, enforce security policies, and remotely troubleshoot issues.
By giving IT teams real-time visibility and control over every endpoint, it helps maintain device performance and reduce security gaps.
With remote work and bring-your-own-device practices on the rise, every endpoint is a potential entry point for attackers. Proper endpoint management ensures devices are authenticated before joining a network, have the latest patches, and follow access rules.
This prevents breaches, keeps systems healthy, and supports compliance with regulations. Without it, organizations face higher risk of data loss, downtime, and costly security incidents.
Endpoint management lays the groundwork for endpoint security. Management tools verify device identity, enforce configuration standards, and push security policies across all endpoints. Endpoint security solutions then monitor for malware, block threats, and respond to attacks on those managed devices.
Together, they ensure only approved devices connect, receive security updates, and have protections in place, reducing the chance of successful attacks.
Maintain a complete inventory of endpoints and enroll every device in your management console. Automate patch deployment and software updates to close vulnerabilities quickly. Enforce strong access controls and configuration standards across all device types. Monitor device health continuously and set alerts for anomalies.
Use remote troubleshooting tools to fix issues without physical access. Regularly review policies to adapt to new devices or threats.
Unified Endpoint Management (UEM) combines management of PCs, mobiles, tablets, and IoT devices into a single console. This boosts efficiency by automating routine tasks—patching, software deployment, and compliance reporting—so teams spend less time juggling multiple tools.
It also improves security through consistent policy enforcement, faster threat detection, and streamlined audits. As a result, security teams can focus on critical threats instead of manual upkeep.
SentinelOne supports endpoint security management with its EDR and XDR solutions. It can protect managed and unmanaged devices, users, identities, and cloud ecosystems. SentinelOne’s AI can block machine-speed attacks and it can detect ransomware with behavioral and static AI models. It can analyze anomalous behavior and identity malicious patterns in real-time without human intervention. Users get critical endpoint and identity alerts with real-time visibility from system-level to identity-based attacks.
SentinelOne’s endpoint security management can correlate and prioritize alerts across workstations, identities, and exposures. It also shows you the full view of attacks and responds quickly with Storyline® technology. SentinelOne can also remediate endpoint security threats with automated or 1-click response/rollback actions.

