Thank you for Registering
We look forward to seeing you there.






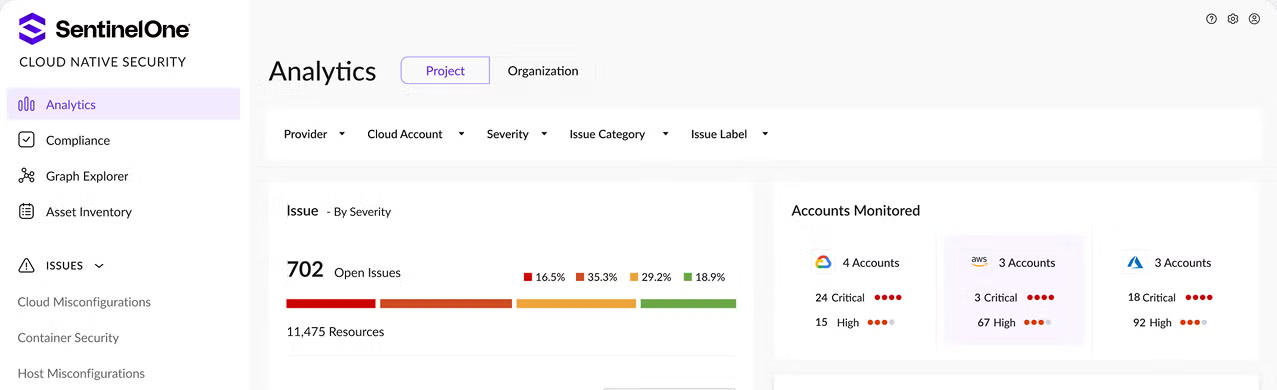
Prepare for what’s next in cloud security with insights and strategies straight from the experts.
Rich Mogull, CSA
Security invariants are controls that must always hold true— ideal for cloud. Learn to build them at scale in AWS, with a brief look at Azure and GCP.
Corey Quinn, Duckbill
Why bad security UX creates risk, how cloud incentives shape outcomes, and a framework for evaluating security tooling.
Dr. Krti Tallam, Kamiwaza
Operationalizing data, model, and execution context to sharpen cloud detections, speed investigations, and make trust auditable.
Jason Kao, Fog Security
See how IAM, encryption, and configuration controls combine to protect cloud data, informed by real cloud provider trends.
Alex Delamotte, SentinelLABS
Learn how cloud-native attacks work in the wild and how to identify and hunt them using logs and attacker behavior.
Nathan Kirk, NR Labs
Learn how sensitive information filters fail in practice and what that means for securing GenAI systems.
Keynotes are the same across time zones, so please select only one track.
Workshops are unique across time zones and both sessions may be attended. For example, you may register for:
Day 2: 9:30 a.m. EST/3:30 p.m. CET and 3:30 p.m. EST/12:30 p.m. PST
We look forward to seeing you there.
See how the world’s most intelligent, autonomous cybersecurity platform can protect your organization today and into the future.