SentinelOne recently discovered a new variant of the Zeus online banking malware that is targeting Canada’s largest banks including: Bank of Montreal (BMO), Royal Bank of Canada (RBC) and National bank of Canada. The most interesting findings we made were in the control panel used by the attackers. More on that a little later.
This attack continues a growing trend in banking malware that goes beyond simply targeting the victim’s login credentials (i.e. their username and password) and injects pages to steal a wealth of personal information including answers to security questions, debit and credit card numbers, social security number, driver license number and more. While some of this information can be used to commit online banking fraud, the other personal data can be used for different crimes including healthcare fraud, opening credit accounts in victim’s names, etc. It could even be used in spear phishing attacks to target individuals within enterprises and government agencies in order to breach secure networks.
It also demonstrates how attackers can now easily repurpose malicious code to target several brands simultaneously.
This variant of Zeus performs the typical web injects we’ve come to expect from banking malware, transparently replacing the real login screen page with a fake web page (see below). The user experience is so seamless that the victim has no reason to believe they are not on the Bank’s real website.
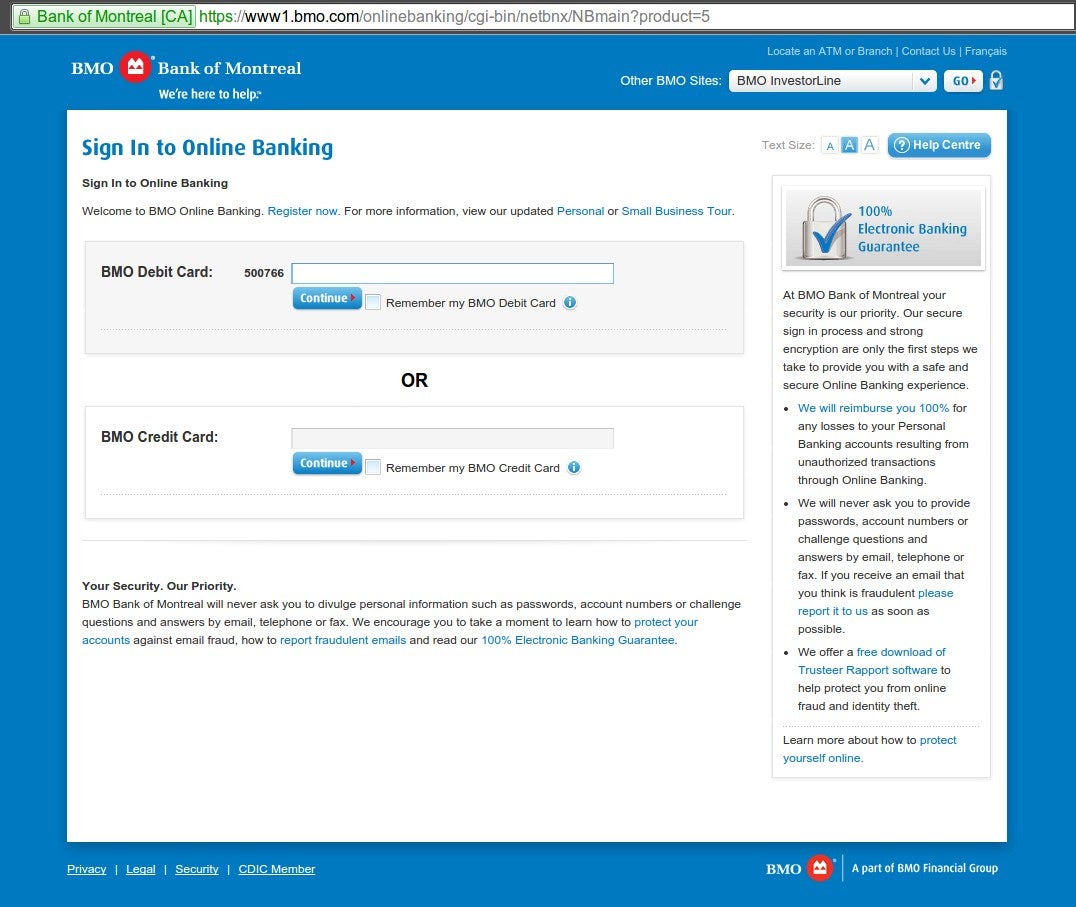
This variant, like most banking Trojans, is not detected by anti-virus products. It also bypasses SSL browser security. Since the malware is installed on the endpoint device it can inject fake webpages into the browser without breaking the SSL connection to the bank’s server and generating a security alert. Predictive execution technology that monitors activity on the endpoint device is the only way to detect and block these attacks, and protect personal information from getting into the hands of criminals.
The following screen shows the “Drop” form used to configure and customize each attack. For example, criminals can specify the destination bank account to transfer stolen funds, including Drop Name, City, Country, IBAN account number and memo about the transaction. The system can automatically calculate the profit percentage the person who is receiving the stolen money (called a Mule) will keep before transferring the balance to the attacker. The attackers can also specify minimum and maximum balances for accounts targeted and minimum and maximum transfer amounts.
This glimpse into the criminal underground demonstrates the sophistication of the tools being used by criminal gangs to conduct banking and other forms of online fraud. Building, executing and monetizing advanced attacks is easier and more affordable than ever before.
7 Little Changes That’ll Make A Big Difference To Your Endpoint Protection

