Trickbot, as a malware family, dates back to 2016. In recent months we, and many others in the industry have been observing something of an “awakening” or resurgence of widespread Trickbot campaigns. Trickbot started life as one of many specialized banking trojans. However, over the years, it has become far more robust. In many ways, Trickbot parallels the evolution of contemporary threats (such as Emotet) via its modular and expandable architecture.
In this write-up, we will focus on a recently intercepted sample of Trickbot, specifically highlighting the threat’s ongoing efforts to evade detection, and we will look at the current suite of modules installed with the analyzed sample(s).
Trickbot: Background and Sample Overview
Trickbot is distributed in multiple ways. It is common to see it dropped in tandem with (or, as a later stage, in) Emotet and Ryuk ransomware infections. It can also be distributed via common Exploit Kit, as well as more traditional methods such as email phishing or via drive-by download.
At the time of infection, Trickbot will typically
· Deposit configuration and supporting module data into %appdata%roaming
· Establish persistence (e.g. via a scheduled task)
· Establish secure communications (TLS) with the C2
· Attempt to update/reconfigure relevant modules
· Attempt lateral movement via the “mworm” and “share” modules
Sample Details:
| Size | 852.0KB |
| Type | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5 | 43e5a4836f8b53e6155ac85ca6311d2e |
| SHA1 | 989ea2e24be32348b5d3bb536c41171afdd32d64 |
| SHA256 | ddb093214e73a1014ee03924e308267281b9f383ab85ea03c3d98dfeeec38a |
| Original Filename | MSWDAT10.DLL |
| Compile Time | 2019-09-16 23:23:41 |
This particular sample was downloaded by a malicious Office document (.docm) received via a phishing email.
Following a short built-in delay (approximate 3000ms or so), the sample begins execution with the trojan dropping copies of itself into %ProgramData% and %AppData%.
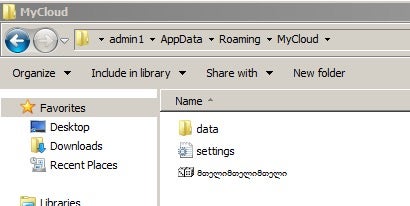
As with other examples of Trickbot, the %AppData% directory will end up homing all the configuration files and encoded modules for the trojan.
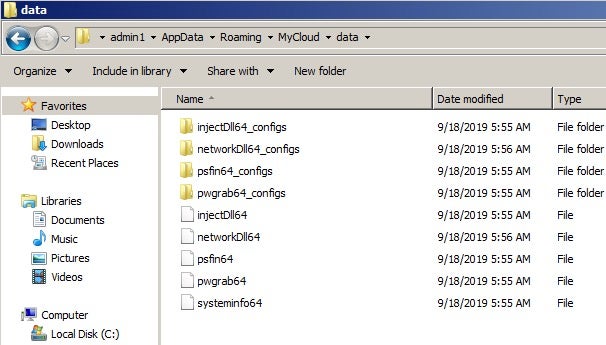
In this sample, we also observe an RSA Crypto routine for decrypting resources in RoamingCryptoRSA for self protection / internal use.
Disabling Windows Defender
The sample manipulates the local policy to alter the behavior of PowerShell and Windows Defender. This specific behavior is not necessarily new to Trickbot. However, it is important to highlight this behavior to remind us of some of the “tricks” that this threat (and others) will use to increase exposure on affected hosts.
cmdline cmd.exe /c powershell Set-MpPreference -DisableIOAVProtection $true
cmdline cmd.exe /c powershell Set-MpPreference -DisableBlockAtFirstSeen $true
cmdline cmd.exe /c powershell Set-MpPreference -DisableIntrusionPreventionSystem $true
cmdline cmd.exe /c powershell Set-MpPreference -DisablePrivacyMode $true
cmdline cmd.exe /c powershell Set-MpPreference -LowThreatDefaultAction
cmdline cmd.exe /c powershell Set-MpPreference -ModerateThreatDefaultAction
cmdline cmd.exe /c powershell Set-MpPreference -DisableBehaviorMonitoring $true
cmdline cmd.exe /c sc delete WinDefend
cmdline cmd.exe /c sc stop WinDefend
cmdline cmd.exe /c powershell Set-MpPreference -DisableScriptScanning $true
cmdline cmd.exe /c powershell Set-MpPreference -DisableRealtimeMonitoring $true
cmdline cmd.exe /c powershell Set-MpPreference -SevereThreatDefaultAction With PowerShell’s advanced logging features (ScriptBlock logging) we can see these events transpire.
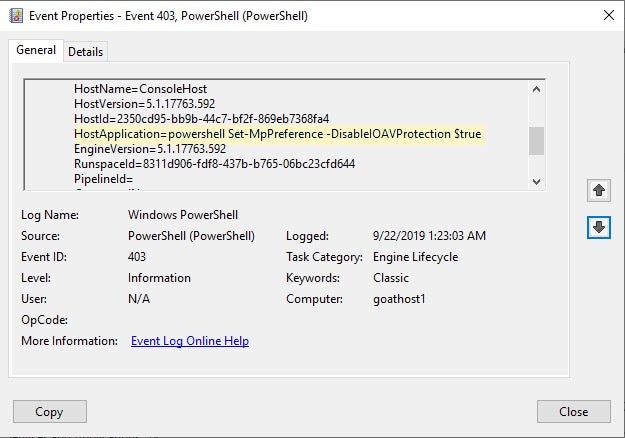
All these commands are executed by powershell.exe via cmd.exe. The purpose of each is to chip away at the protections provided by Windows Defender / native OS controls. Each of these settings are well documented. In essence, they each function as follows:
| Setting | Function |
|---|---|
| DisableOAVProtection | Toggles scanning of downloaded files and attachments |
| DisableBlockAtFirstSeen | Toggles blocking of new/unknown malware upon the first instance of such |
| DisableIntrusionPreventionSystem | Toggles network exploit prevention |
| DisablePrivacyMode | Toggles display/availability of threat history data to other users |
| LowThreatDefaultAction | Controls behavior on low-level threat detection |
| ModerateThreatDefaultAction | Controls behavior on moderate-level threat detection |
| DisableBehaviorMonitoring | Toggles Windows Defender behavioral monitoring and detection |
| DisableScriptScanning | Toggles scanning of scripts by Windows Defender |
| DisableRealTimeMonitoring | Toggles Windows Defender real-time detection |
| SevereThreatDefaultAction | Controls behavior on severe threat detection |
Persistence Mechanisms & Configuration
Trickbot employs multiple persistence mechanisms, including the creation of scheduled tasks. In this particular example, the trojan creates a task which is triggered upon startup and repeats every 11 minutes.
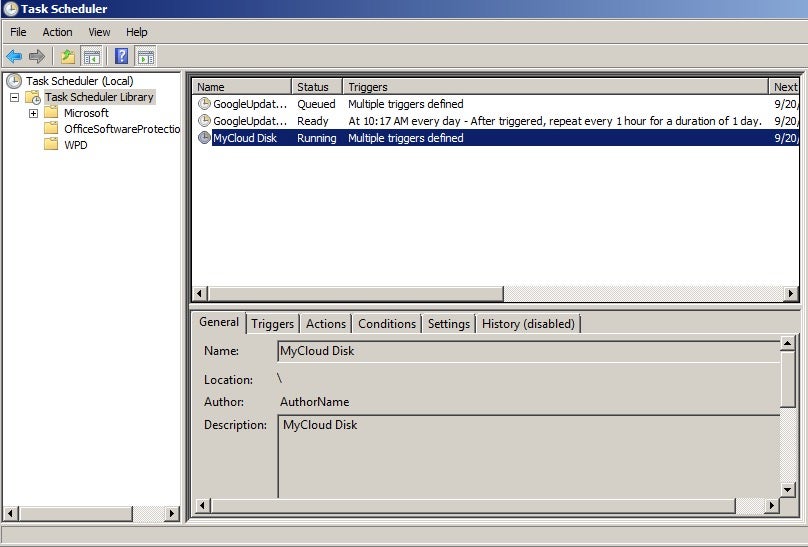
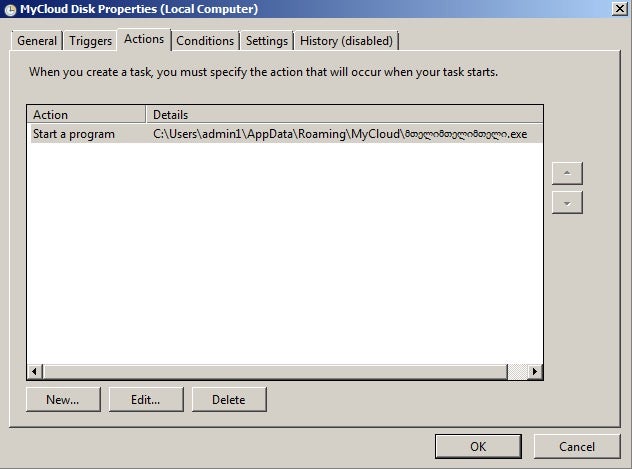
Per typical Trickbot infections, the trojan installs multiple modules and encoded configuration data in %appdata%roaming.
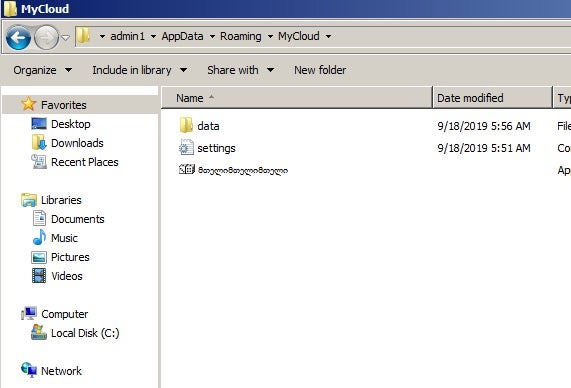
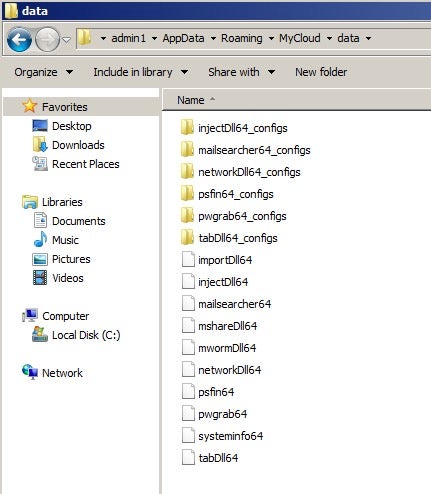
We see, in this example, that we have the following:
| Name | Function |
|---|---|
| importDll64 | Browser data stealer module |
| injectDll64 | Handles web-injects, including support for several hundred banking/financial sites |
| mailsearcher64 | Recon module parses specific filetypes for “of interest” data |
| mshareDll64 | Lateral movement / enumeration module via LDAP and SMB exploitation. Mshare and mworm modules work in cooperation |
| mwormDll64 | Lateral movement / enumeration module via LDAP and SMB exploitation. Mshare and mworm modules work in cooperation |
| networkDll64 | Recon module queries network specific environmental data |
| psfin64 | Point-of-sale recon module |
| pwgrab64 | Credential theft module (stored browser data) |
| systeminfo64 | Recon module. Provides system-specific information and data to the C2 |
| tabDll64 | Credential theft module (mimikatz). Sometimes contains additional lateral movement code. |
The SHA checksums for the DLL modules dropped by this sample are listed below:
| Name | SHA1 |
|---|---|
| importDll64.dll | cbd80eb5112a9560fbe7d9ce6fc0258af6415827 |
| injectDll64.dll | 452d1bd2c7108429a732f2d6c504a595989a91d8 |
| mailsearcher64.dll | 452d1bd2c7108429a732f2d6c504a595989a91d8 |
| mshareDll64.dll | 9d545c60a015a42668b33797e0274b8f7e374de9 |
| mwormDll64.dll | 1b8088f5ae6118fd948c50bf9269ba4d9ba1a781 |
| networkDll64.dll | 374b411a00f513b002902870e216e56186b8c9b8 |
| psfin64.dll | de9caa99ca6c4f7892b3b9dfb9c9747bd503d753 |
| pwgrab64.dll | 8ad57a9acfd3940f2b044c2ab7777f8d051941f0 |
| systeminfo64.dll | b8608d835faa4f5b3fe38e79c0b3a9e6a7f1811f |
| tabDll64.dll | a6c0d73d47945bd6350bf698870aa7189e7085c7 |
Decoding Trickbot DLL Modules
By decoding the individual modules and their configuration/support files, we can gain further understanding on the data being targeted. The data from decoding the importdll64 module shown below is just a small fraction of the sites listed for interception by this particular module. This sample listed ~25,000 sites for targeting; however, the amount is higher than that due to the use of wildcard characters.
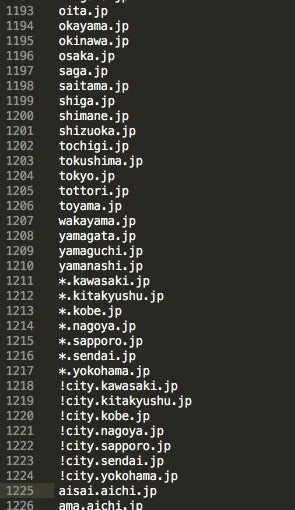
We can also dive into the specific web-injection attacks and targets by exploring the decoded configuration files for injectDLL64. This part of the decoded injectdll64dinj reveals a portion of the trojan’s web injects.
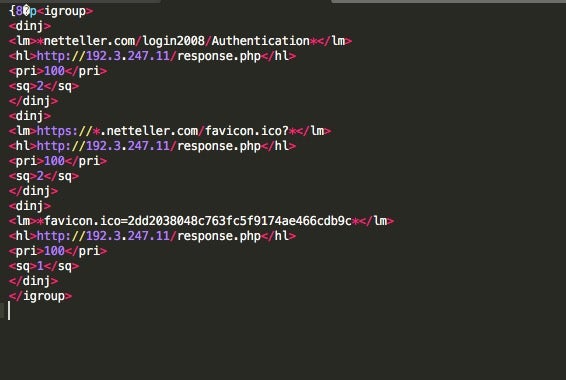
Here were see part of the decoded injectdll64dpost revealing the data exfiltration targets:
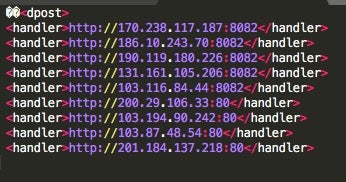
Part of the decoded mwormDll64 module:
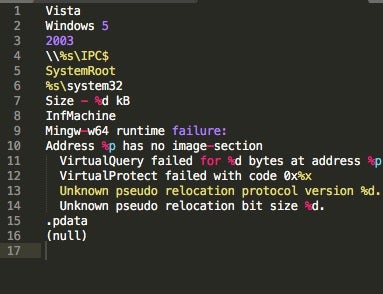
Decoding the pwgrabDLL64 shows the sample’s password grabbing functionality:
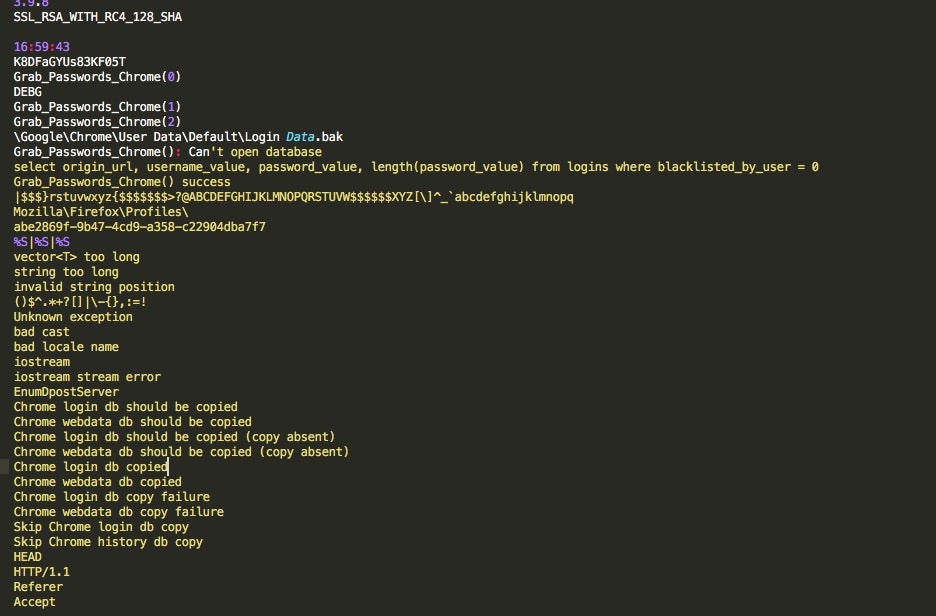
SentinelOne Detection & Mitigation
SentinelOne’s advanced endpoint technology is able to prevent infection and further compromise at all stages of a Trickbot-based attack.
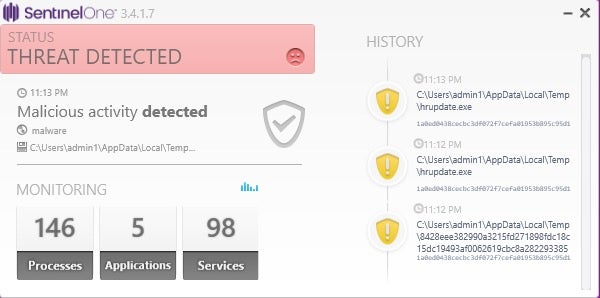
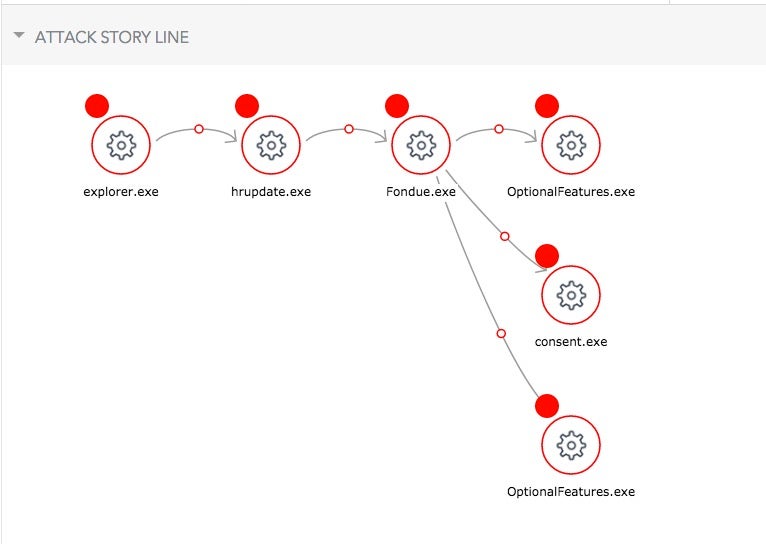
Through the SentinelOne Management console, we can drill deeper to see the specific flow and gather additional details. For example, below we see the Attack Story Line for a directly executed Trickbot payload.
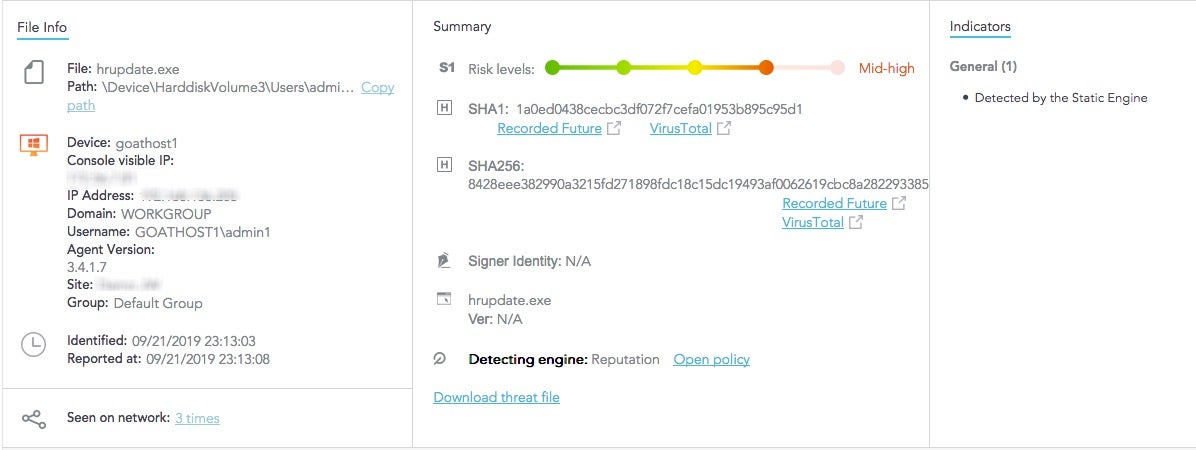
Conclusion
Over the years, Trickbot has continued to evolve and weave itself in and out of the threat landscape. The most recent campaigns have been some of the more prolific and damaging across the history of this threat family. That being said, it can be stopped. Regardless of the delivery method (web drive-by download, phishing email, direct execution), the SentinelOne advanced endpoint solution can prevent infection and block any related malicious actions. If you’re not already protected by SentinelOne, contact us for a free demo and see how we can help autonomously protect your organization from today’s malware threats.
IOCs
PE Hash(s) D48649f60b0b3e96fb3b077d7af00d1b1a3fefe8 989ea2e24be32348b5d3bb536c41171afdd32d64 9dbd2d9465c2013dc920100feb2112c04103fd5a Modules cbd80eb5112a9560fbe7d9ce6fc0258af6415827 importDll64.dll 452d1bd2c7108429a732f2d6c504a595989a91d8 injectDll64.dll 5e71926c1b704b13c42fd38f53aefed933d9c4ce mailsearcher64.dll 9d545c60a015a42668b33797e0274b8f7e374de9 mshareDll64.dll 1b8088f5ae6118fd948c50bf9269ba4d9ba1a781 mwormDll64.dll 374b411a00f513b002902870e216e56186b8c9b8 networkDll64.dll de9caa99ca6c4f7892b3b9dfb9c9747bd503d753 psfin64.dll 8ad57a9acfd3940f2b044c2ab7777f8d051941f0 pwgrab64.dllTrick b8608d835faa4f5b3fe38e79c0b3a9e6a7f1811f systeminfo64.dll a6c0d73d47945bd6350bf698870aa7189e7085c7 tabDll64.dll Network 212.80.216.142:443 170.238.117.187:8082 186.10.243.70:8082 190.119.180.226:8082 131.161.105.206:8082 103.116.84.44:8082 200.29.106.33:80 103.194.90.242:80 103.87.48.54:80 201.184.137.218:80 103.84.238.3:80 107.172.143.155:443 193.29.56.122:443 192.227.142.155:443 23.94.204.80:443 185.222.202.49:443 104.244.73.115:443 MITRE ATT&CK Trickbot Application has registered itself to become persistent via scheduled task. MITRE: Persistence {T1084} Shellcode execution was detected. MITRE: Execution {T1106, T1064} PowerShell {T1086} Process Hollowing {T1093} Exfiltration Over Command and Control Channel {T1041} Disabling Security Tools {T1089}




