In a recent post [1], we disclosed details of a new Trickbot executor module “mexec” and analyzed the downloader variant of this module. In this follow up post, we provide the first analysis the dropper version of the mexec module.
See the report for the full list of IOCs and further details on the TrickBot executor module “mexec”.
Background
TrickBot is the successor of Dyre [2,3], and at first was primarily focused on banking fraud and utilized injection systems in the same manner. Over the years, TrickBot has shifted focus to enterprise environments to incorporate everything from network profiling and mass data collection to lateral traversal exploits. This focus shift is also prevalent in their incorporation of malware and techniques in their tertiary deliveries that are targeting enterprise environments. Such behavior is similar to a company where the focus will shift depending on what generates the best revenue.
Research Insights
The dropper version of mexec is very similar to the downloader except that the payload is carried onboard, which makes the module substantially larger than its downloader counterpart. The dropper variant is also very similar to TrickBot’s loader but was written to be able to accommodate more generic deliveries.
The dropper version of mexec functionally overlaps with how TrickLoader works:
- Custom Base64 alphabet string encoding
- Usage of MiniLZO
- Function obfuscation using a table of offsets
This version of mexec could easily be misidentified as TrickLoader, but mexec is not used to deliver TrickBot and is simply setup as a dropper piece that will write and execute an onboard hidden executable. It’s also a DLL and designed to be executed in memory to perform its task or to deliver another piece of malware.
While the strings are encoded in the same manner you would expect in a Trickbot sample, there are noticeably fewer of them.
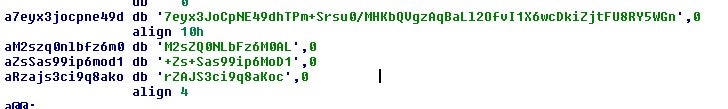
Decoding them is the same process as you would find in a TrickBot sample.
The first thing the sample does is spin up multiple threads, but the interesting one is the second one.
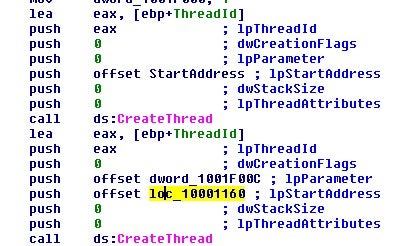
In the main thread that is spun up as the second one, it performs the normal deobfuscation routine that you find in a Trickbot loader sample. If you are unfamiliar with this process of deobfuscation, you can find more details in our report on TrickLoader Deobfuscation.
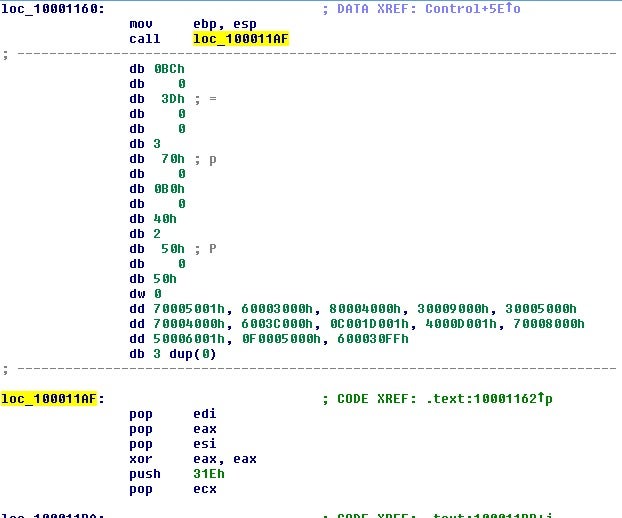
The above code is the start of the process of building out the function address table; it jumps over a table of offsets to kick off the process.
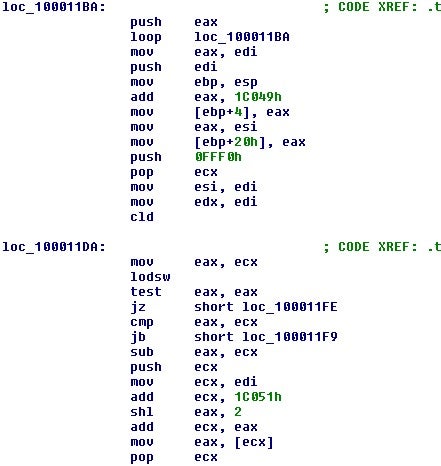
After rebuilding the address table, the function responsible for decoding functions is called.
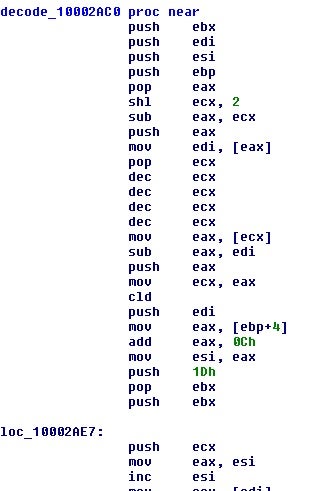
In the exact same way that we go over deobfuscating the TrickLoader binary, we can do the same with this sample. This will then leave us with all of the decoded functions.
One of the decoded addresses from the table does not appear to be a function; in fact, much like TrickLoader, this is a LZO compressed PE file.
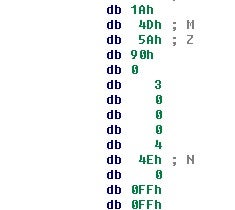
After decompressing and analyzing the PE file, we discover this version of mexec is dropping the DNS variant of Anchor TrickBot[4].
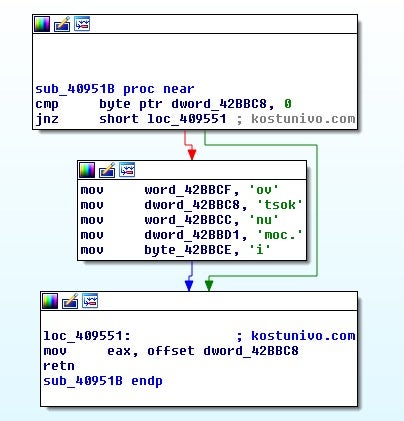
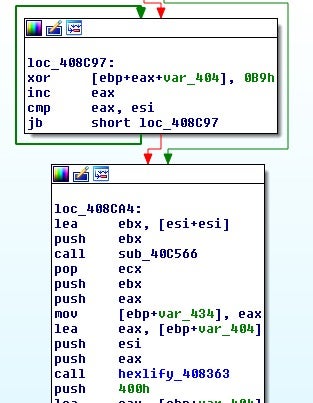
Another variant recovered was also dropping the normal variant of Anchor TrickBot.
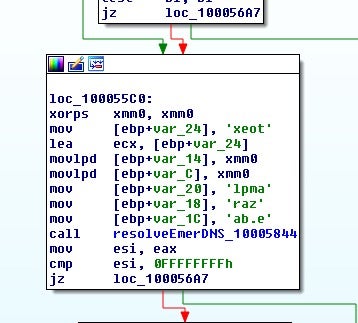
Pivoting on the decoding string of “futuresx.exe” from above also leads to a sandbox report[4] on an Anchor DNS sample. In VirusTotal, we can see this same hash was also delivered through the downloader variant:
Read the Full Report
See the report for the full list of IOCs and further details on the TrickBot executor module “mexec”.
References
1: Deep Dive Into TrickBot Executor Module “mexec”: Hidden “Anchor” Bot Nexus Operations
2: https://blog.malwarebytes.com/threat-analysis/2016/10/trick-bot-dyrezas-successor/
3: https://www.fidelissecurity.com/threatgeek/archive/trickbot-we-missed-you-dyre/
4: https://www.sentinelone.com/labs/anchor-project-the-deadly-planeswalker-how-the-trickbot-group-united-high-tech-crimeware-apt/




