Malware analysis plays an essential role in avoiding and understanding cyber attacks. When incident response teams are brought into an an incident involving malware, the team will typically gather and analyze one or more samples in order to better understand the attacker’s capabilities and to help guide their investigation. As organizations deal with an increasing number of attacks and breaches, analysts are always looking for ways to triage and understand samples faster and more efficiently. In this post, we dive into the top 15 Essential Malware Analysis Tools used by researchers today. All 15 tools listed are free or have a community version that is free, and these offer a great way to see if a tool suits your needs. For professional use, the paid versions where available are highly recommended.
Disassemblers
1. IDA Pro/Ghidra
IDA Pro has been the go to SRE (Software Reverse Engineering) Suite for many years until Ghidra’s release in 2019. Since then Ghidra’s popularity has grown exponentially due to it being a free open-source tool that was developed and is still maintained by the NSA. If you do not have an IDA Pro license and do not have thousands of dollars to spend on IDA Pro, then Ghidra is for you. Since I use both of them I will also list my top 5 favorite plugins for each.
IDA Pro:
- VT-IDA Plugin: GitHub – VirusTotal/vt-ida-plugin: Official VirusTotal plugin for IDA Pro
This plugin integrates functionality from VirusTotal web services into the IDA Pro’s user interface. - BinDiff: zynamics.com – BinDiff
BinDiff is a comparison tool for binary files, it is great for malware researchers to quickly find differences and similarities in disassembled code. - efiXplorer: https://github.com/binarly-io/efiXplorer
IDA plugin for UEFI firmware analysis and reverse engineering automation - Bincat: https://github.com/airbus-seclab/bincat
Binary code static analyzer that performs value and taint analysis, type reconstruction. - Ret Sync: https://github.com/bootleg/ret-sync
re-sync is a set of plugins that helps to synchronize a debugging session
Ghidra:
- VTGrep: https://github.com/SentineLabs/VTgrepGHIDRA
This plugin integrates functionality from VirusTotal web services into the GHIDRA’s user interface. The current version is v0.1, This plugin is not production-ready yet, and unexpected behavior can still occur and released without any warranty. This release integrates VTGrep into GHIDRA, facilitating the searching for similar code, strings, or sequences of bytes. - Binwalk: https://github.com/ghidraninja/ghidra_scripts/blob/master/binwalk.py
Runs binwalk on the current program and bookmarks the findings. Requires binwalk to be in $PATH - Yara: https://github.com/0x6d696368/ghidra_scripts/blob/master/YaraSearch.py
This Ghidra script provides a YARA search. It will place a PRE_COMMENT at the location of each match. It will set bookmarks for each match. - Golang Renamer: https://github.com/ghidraninja/ghidra_scripts/blob/master/golang_renamer.py
Restores function names from a stripped Go binary. - Daenerys: https://github.com/daenerys-sre/source
Daenerys is an interop framework that allows you to run IDAPython scripts under Ghidra and Ghidra scripts under IDA Pro with little to no modifications.
Debuggers
2. Windbg
Windows Debugger is a multipurpose debugger for the Microsoft Windows OS. Malware reverse engineers have used this in the past, but now there are other alternatives on the entry-level malware analyst market. Windbg has a steep learning curve, so check out some of the numerous video tutorials and websites to help learn the essential commands when debugging.
Some of the benefits of using Windbg over other debuggers besides debugging user-mode applications are device drivers, and the operating system itself in kernel mode.
3. x32/x64 Debugger
x64dbg is an open-source binary debugger for Windows aimed at malware analysis and reverse engineering of executables. There are many features available, and it comes with a comprehensive plugin system. You can find many plugins for this debugger on the plugins wiki page.
x64dbg has become one of the most popular debugging software for malware due to its ease of use and its GUI interface, making it easy to understand things.
Hex Editors
4. HxD
HxD is a free hex editor, disk editor, and memory editor for Windows. Other primary options include tagging sections of memory, searching for unique types of data, modifying the direction of these searches, and exporting any information in various outputs. There is no limit in terms of the number of times an action can be undone.
5. Hiew
Hacker’s View (Hiew) is a program that allows you to visualize files. Hiew’s main function is to display hex files for people who want to change a few bytes in the code, but it is also capable of much more. Hiew additionally contains tools for detailed dumps of OMF/COFF object files and libraries and NE/LE/LX/PE/ELF executables. It is also useful for splitting and joining dual executables. This tool is a go-to tool for many malware analysts. HIEW cycles through string types ASCll, Odd and Unicode, and can find strings many other tools don’t. If you want to see how good it is, the creator of Hiew, Yuri Slobodyanyuk, has created an in-depth tutorial that is great.
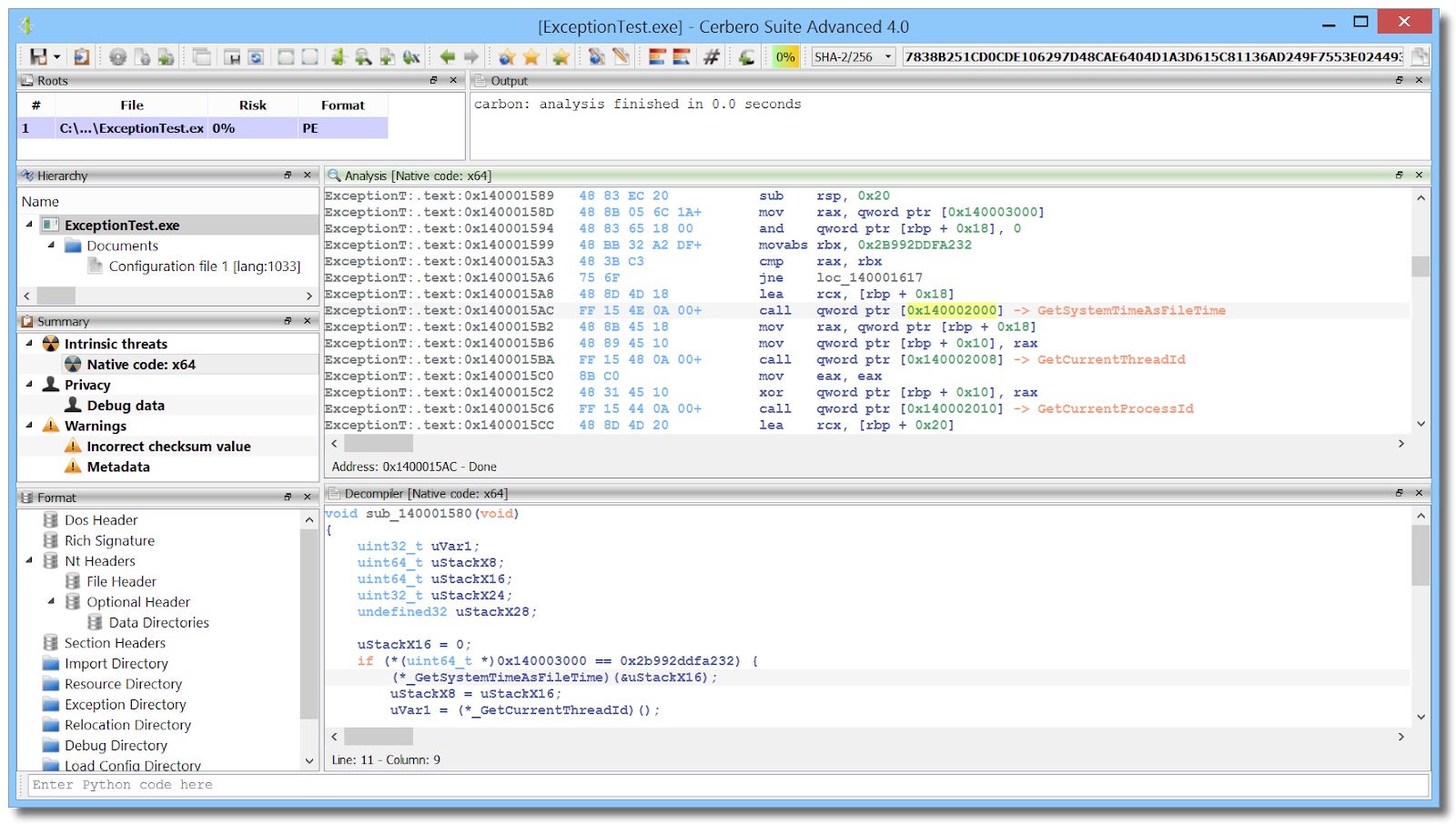
6. Cerbero Suite
The Cerbero Suite is branded as “The Hacker’s Multitool”. I initially came across this tool when I was looking for an advanced hex editor years ago. This tool suite has added so many features in the last two years that I use this just as much as any tool listed in this blog. The Cerbero Suite has a hex editor with advanced features and lets you define layout elements such as structures and code. It can analyze many different file formats.
Over the last year, the Cerbero Suite has added a Carbon disassembler engine that integrates with the Sleigh decompiler that Ghidra uses. You can also perform Windows memory analysis on physical memory images, hibernation files, and crash dumps.
Monitors
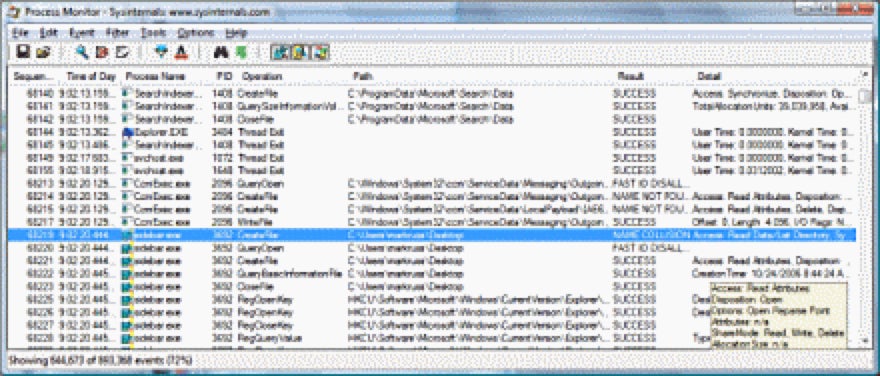
7. Process Monitor
Process Monitor is an advanced monitoring tool for Windows that shows real-time file system, Registry, and process/thread activity. Process Monitor includes robust monitoring and filtering capabilities, boot time logging of all operations, data captured for operation input and out params, and provides reliable capture of process details. The process tree tool shows the relationships of all processes referenced in a trace, and much more.
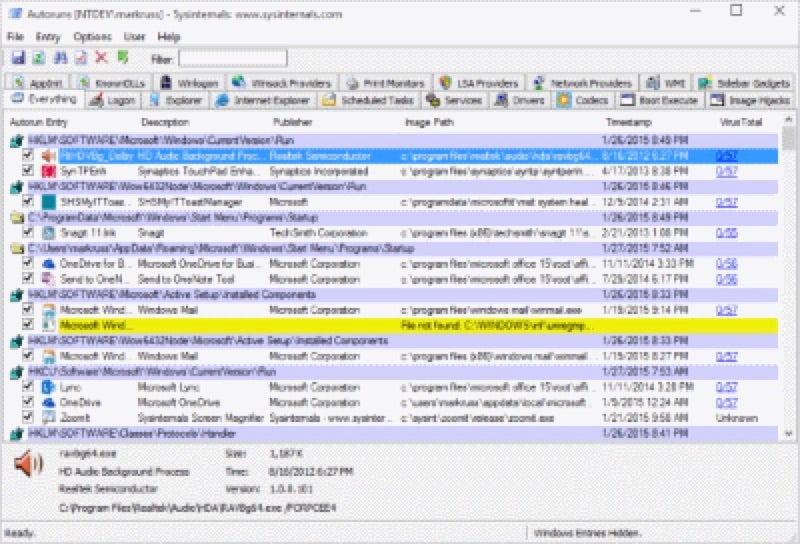
8. Autoruns
This utility, which has the most comprehensive knowledge of auto-starting locations of any startup monitor, shows you what programs are configured to run during system bootup or login, and when you start various built-in Windows applications like Internet Explorer, Explorer, and media players. Autoruns shows you the currently configured auto-start applications as well as the full list of Registry and file system locations available for auto-start configuration.
Autostart locations displayed by Autoruns include logon entries, Explorer add-ons, Internet Explorer add-ons, including Browser Helper Objects (BHOs), Appinit DLLs, image hijacks, boot execute images, Winlogon notification DLLs, Windows Services and Winsock Layered Service Providers, media codecs, and more. Switch tabs to view autostarts from different categories.
PE Analysis
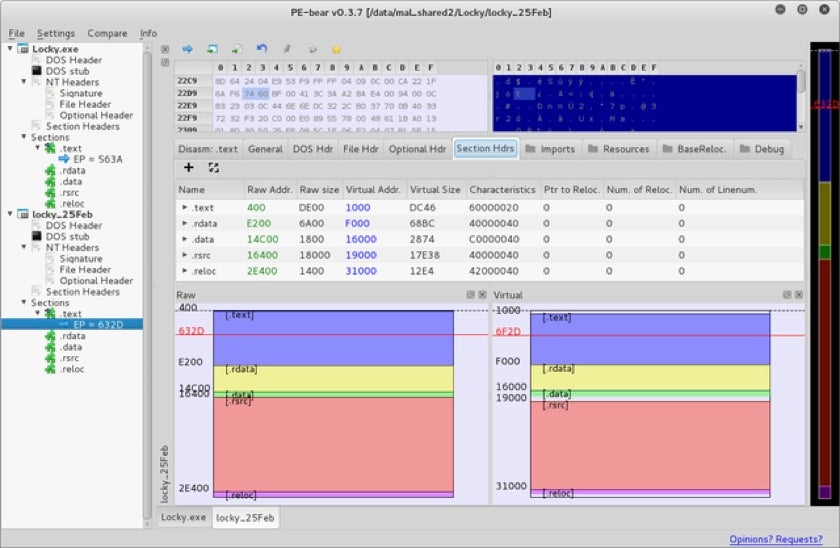
9. PE-bear
PE-bear is a freeware reversing tool for PE files. It is a viewer/editor for PE32 and PE64 files.You can view multiple files in parallel and it recognizes known packers by signature. PE Bear is very useful for visualizing a PE section layout, and it allows you to add new elements among many other features.
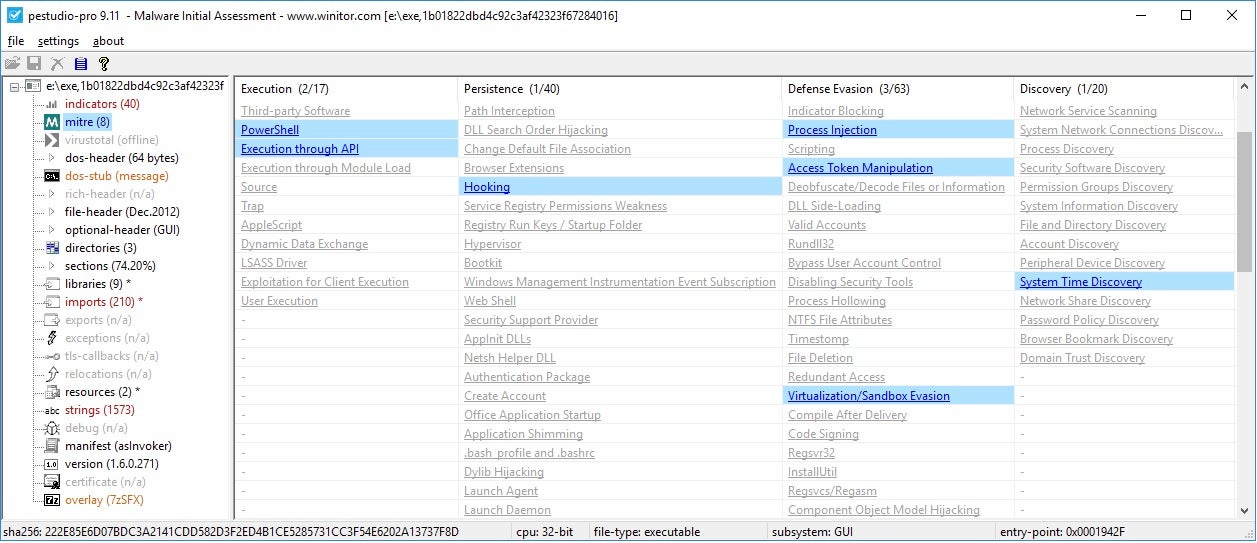
10. PE Studio
The goal of PE Studio is to spot artifacts of executable files in order to ease and accelerate Malware Initial Assessment. Some of PE Studio’s features are detecting file signatures, hard-coded URLs and IP addresses, metadata, imports, exports, strings, resources, manifest, rich-header, Mitre ATT&CK matrix and retrieval of VirusTotal scores.
11. pefile
The pefile tool is a multi-platform Python module to parse and work with Portable Executable (PE) files. Most of the information contained in the PE file headers is accessible, as well as all the sections’ details and data. The structures defined in the Windows header files will be accessible as attributes in the PE instance. When scripting in python and you wanted to analyze a large data set of binary, Pefile is the a great tool to use.
Other Useful Tools
12. Yara
YARA is primarily used in malware research and detection. It provides a rule-based approach to create descriptions of malware families based on textual or binary patterns. A description is essentially a YARA rule name, plus a sets of strings to search for and a boolean expression that controls the logic of the search. Yara rules plays an important role in Threat Intelligence and are very fast when scanning large datasets.
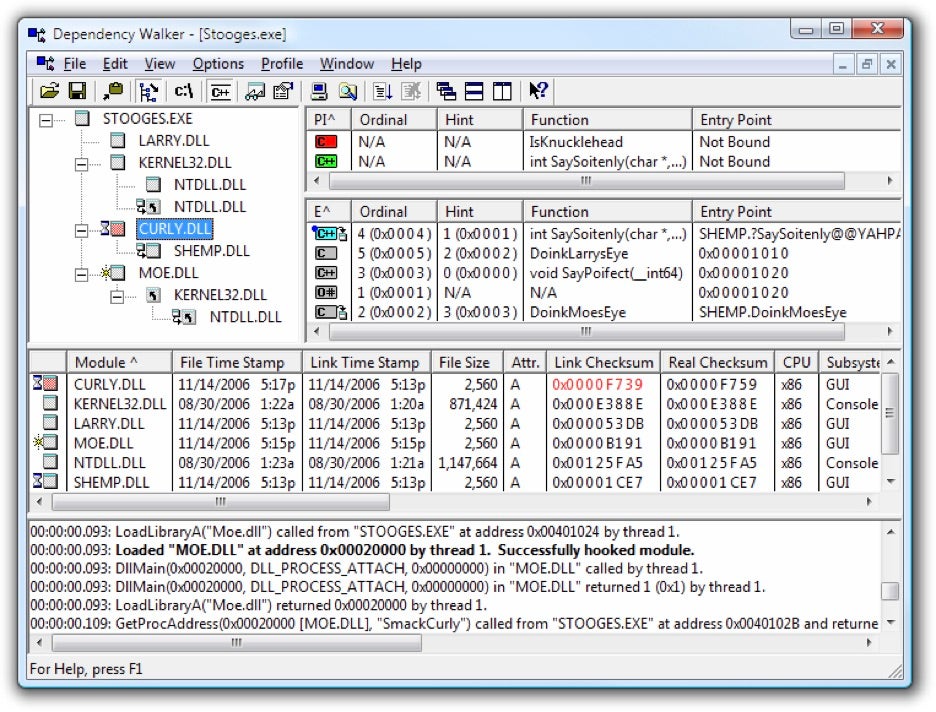
13. Dependency Walker
Dependency Walker is a free program for Microsoft Windows used to list the imported and exported functions of a portable executable file. It also displays a recursive tree of all the dependencies of the executable file. Dependency Walker was included in Microsoft Visual Studio until Visual Studio 2005 and Windows XP SP2 support tools.
14. dnSpy
dnSpy is a debugger and .NET assembly editor. You can use it to edit and debug assemblies even if you don’t have any source code available. The main features of dnSpy are its debug and edit features. This is a must have tool when reversing malware written in C#
- Debug .NET and Unity assemblies
- Edit .NET and Unity assemblies
15. Burp Suite
Burp Suite Professional is one of the most popular penetration testing tools available today, and is also helpful when you want to use burp for SSL interception. This will help when malware encrypts the traffic over SSL. Burp Suite is great to help you capture all of this traffic and more.
Conclusion
These 15 tools are all an essential part of my malware analysts toolkit, and I encourage you to become familiar with each one, as they will greatly enhance your ability to quickly and effectively triage and analyze new samples.




