By Jim Walter and Niranjan Jayanand
First noticed on VirusTotal on November 26th by researcher Zack Allen, Rook Ransomware initially attracted attention for the operators’ rather unorthodox self-introduction, which stated that “We desperately need a lot of money” and “We will stare at the internet”.
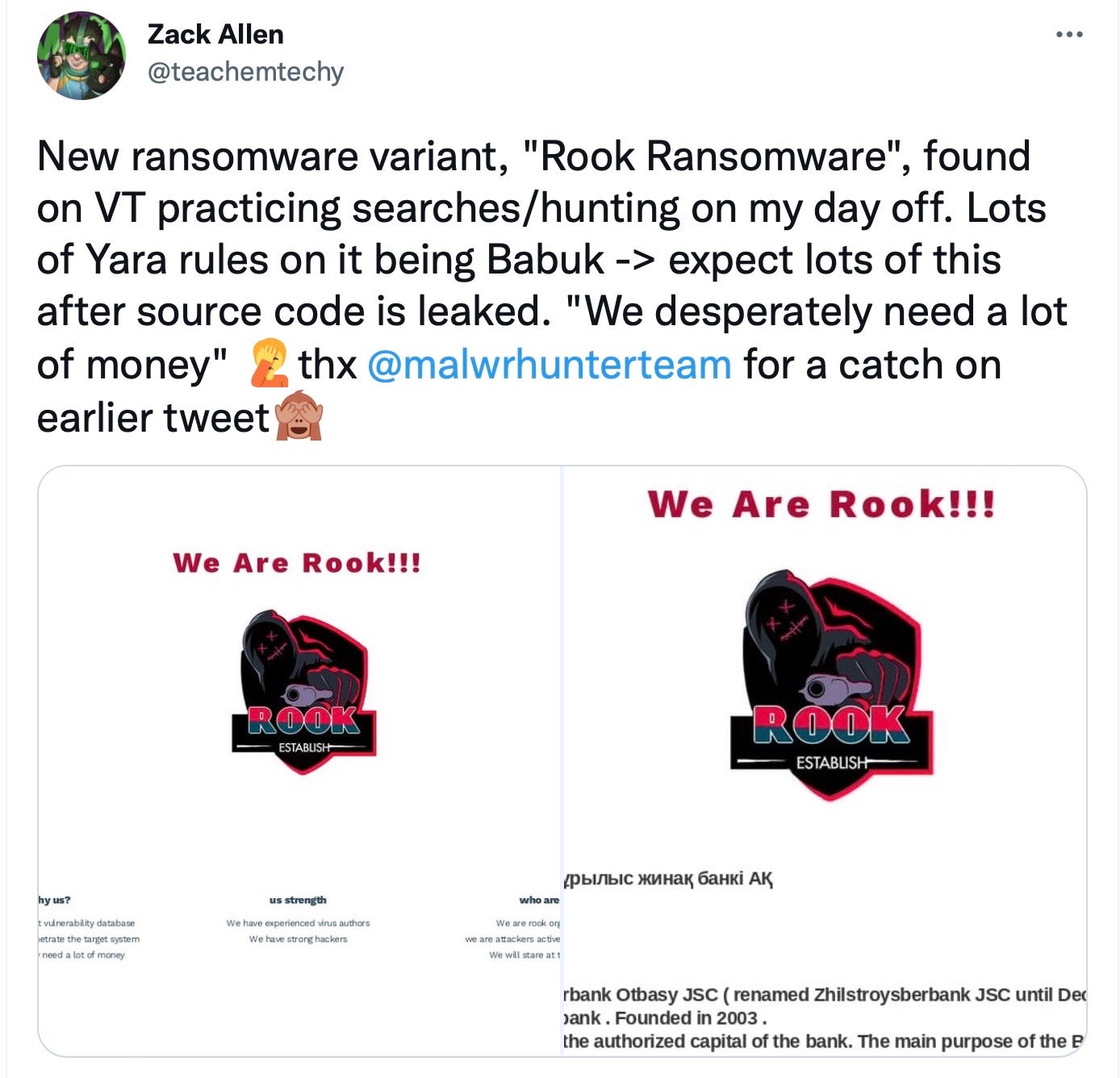
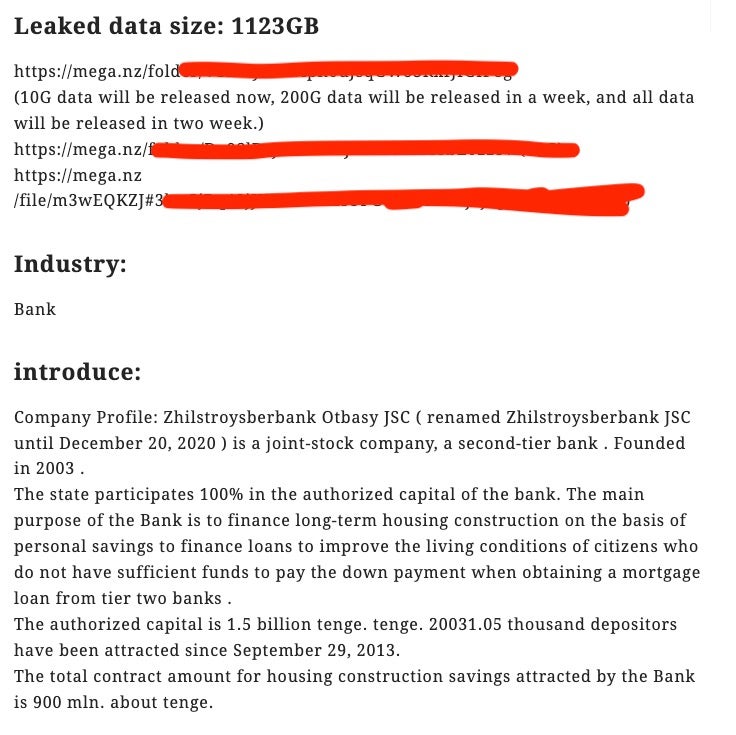
These odd pronouncements prompted some mirth on social media, but they were followed a few days later by more serious news. On November 30th, Rook claimed its first victim: a Kazkh financial institution from which the Rook operators had stolen 1123 GB of data, according to the gang’s victim website. Further victims have been claimed since then.
In this post, we offer the first technical write up of the Rook ransomware family, covering both its main high-level features and its ties to the Babuk codebase.
Technical Details
Rook ransomware is primarily delivered via a third-party framework, for example Cobalt Strike; however, delivery via phishing email has also been reported in the wild.
Individual samples are typically UPX packed, although alternate packers/crypters have been observed such as VMProtect.
Upon execution, Rook samples pop a command window, with differing output displayed. For example, some versions show the output path for kph.sys (a component of Process Hacker), while others display inaccurate information around the use of ADS (Alternate Data Streams).
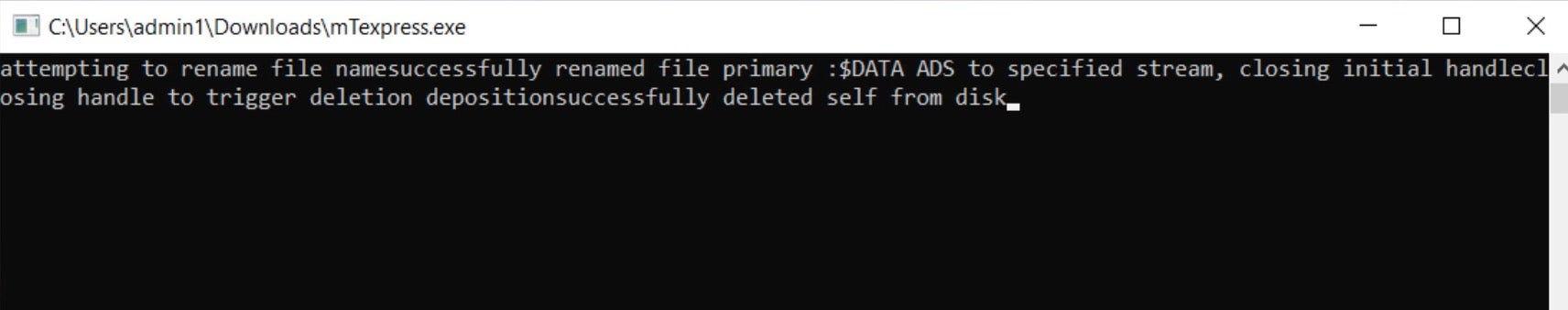
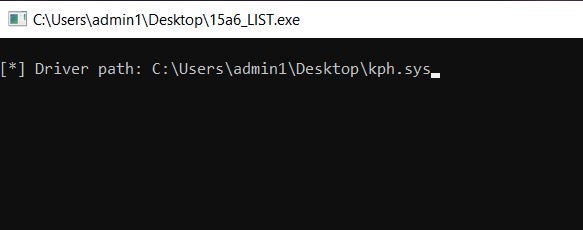
The ransomware attempts to terminate any process that may interfere with encryption. Interestingly, we see the kph.sys driver from Process Hacker come into play in process termination in some cases but not others. This likely reflects the attacker’s need to leverage the driver to disable certain local security solutions on specific engagements.
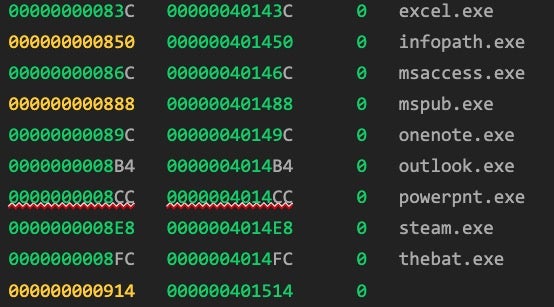
There are numerous process names, service names and folder names included in each sample’s configuration. For example, in sample 19CE538B2597DA454ABF835CFF676C28B8EB66F7, the following processes, services and folders are excluded from the encryption process:
Processes names skipped:
sql.exe oracle.exe ocssd.exe dbsnmp.exe visio.exe winword.exe wordpad.exe notepad.exe excel.exe onenote.exe outlook.exe synctime.exe agntsvc.exe isqlplussvc.exe xfssvccon.exe mydesktopservice.exe ocautoupds.exe encsvc.exe firefox.exe tbirdconfig.exe mydesktopqos.exe ocomm.exe dbeng50.exe sqbcoreservice.exe infopath.exe msaccess.exe mspub.exe powerpnt.exe steam.exe thebat.exe thunderbird.exe
Service names terminated:
memtas mepocs veeam backup GxVss GxBlr GxFWD GxCVD GxCIMgr DefWatch ccEvtMgr ccSetMgr SavRoam RTVscan QBFCService QBIDPService Intuit.QuickBooks.FCS QBCFMonitorService AcrSch2Svc AcronisAgent CASAD2DWebSvc CAARCUpdateSvc
Folders names skipped:
Program Files Program Files (x86) AppData Windows Windows.old Tor Browser Internet Explorer Google Opera Opera Software Mozilla
File names skipped:
autorun.inf boot.ini bootfont.bin bootsect.bak bootmgr bootmgr.efi bootmgfw.efi desktop.ini iconcache.db ntldr ntuser.dat ntuser.dat.log ntuser.ini thumbs.db
As with most modern ransomware families, Rook will also attempt to delete volume shadow copies to prevent victims from restoring from backup. This is achieved via vssadmin.exe.
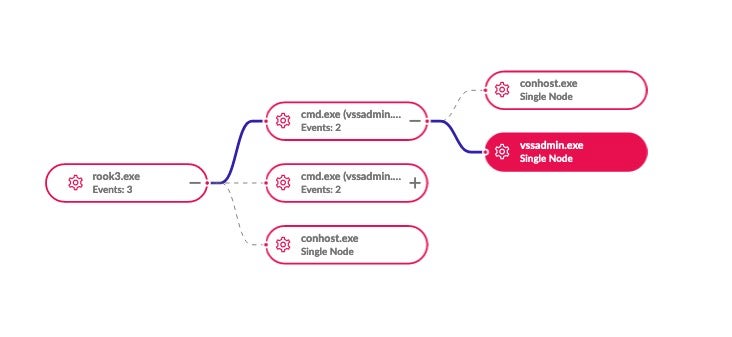
The following syntax is used:
vssadmin.exe delete shadows /all /quiet
Early variants of Rook were reported to have used a .TOWER extension. All current variants seen by SentinelLabs use the .ROOK extension.
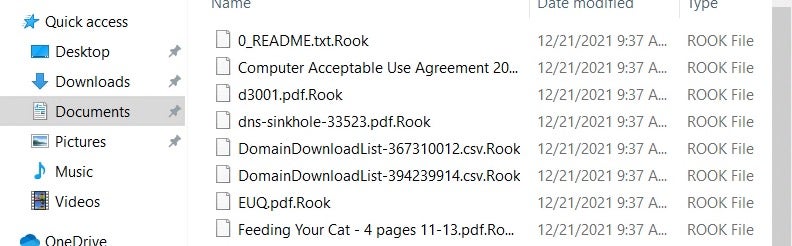
.ROOK extension on affected filesIn the samples we analyzed, no persistence mechanisms were observed, and after the malware runs through its execution, it cleans up by deleting itself.
Babuk Overlaps
There are a number of code similarities between Rook and Babuk. Based on the samples available so far, this appears to be an opportunistic result of the various Babuk source-code leaks we have seen over 2021, including leaks of both the compiled builders as well as the actual source. On this basis, we surmise that Rook is just the latest example of an apparent novel ransomware capitalizing on the ready availability of Babuk source-code.
Babuk and Rook use EnumDependentServicesA API to retrieve the name and status of each service that depends on the specified service before terminating. They enumerate all services in the system and stop all of those which exist in a hardcoded list in the malware. Using OpenSCManagerA API, the code gets the Service Control Manager, gets the handle and then enumerates all services in the system.
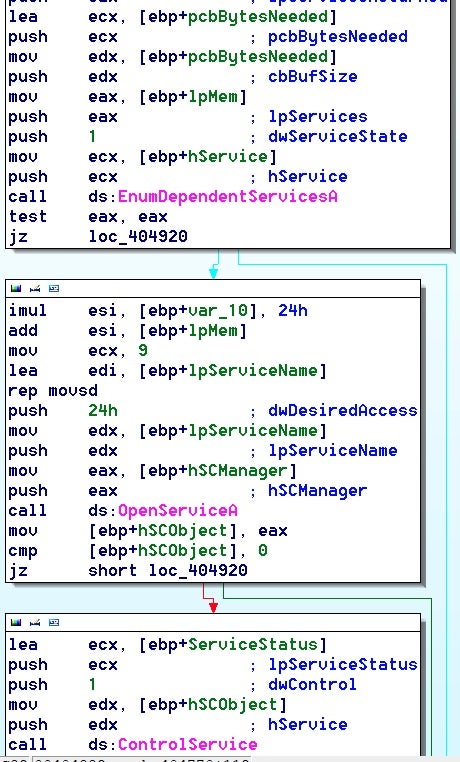
Veeam Backup GxVss GxBlr GxFWD GxCVD GXCIMgr DefWatch ccEvtMgr ccSetMgr SavRoam RTVscan QBFCService QBIDPService Intuit.QuickBooks.FCS QBFCMonitorService YooBAckup YooIT Zhudongfangyu Sophos Stc_raw_agent VSNAPVSS VeeamTransportSvc VeeamDeploymentService VeeamNFSSvc Veeam PDVFSService BackupExecVSSProvider BackupExecAgentAccelerator BackupExecAgentBrowser BackupExecDiveciMediaService BackupExecJobEngine BackupExecManagementService BackupExecRPCServiceAcrSch25vc AcronisAgent CASAD2DWebSvc CAARCUpdateSvc
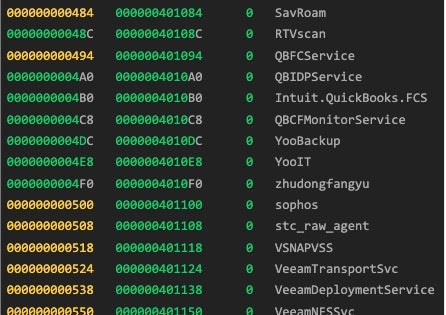
In addition, both Rook and Babuk use the functions CreateToolhelp32Snapshot, Process32FirstW, Process32NextW, OpenProcess, and TerminateProcess to enumerate running processes and kill any found to match those in a hardcoded list.
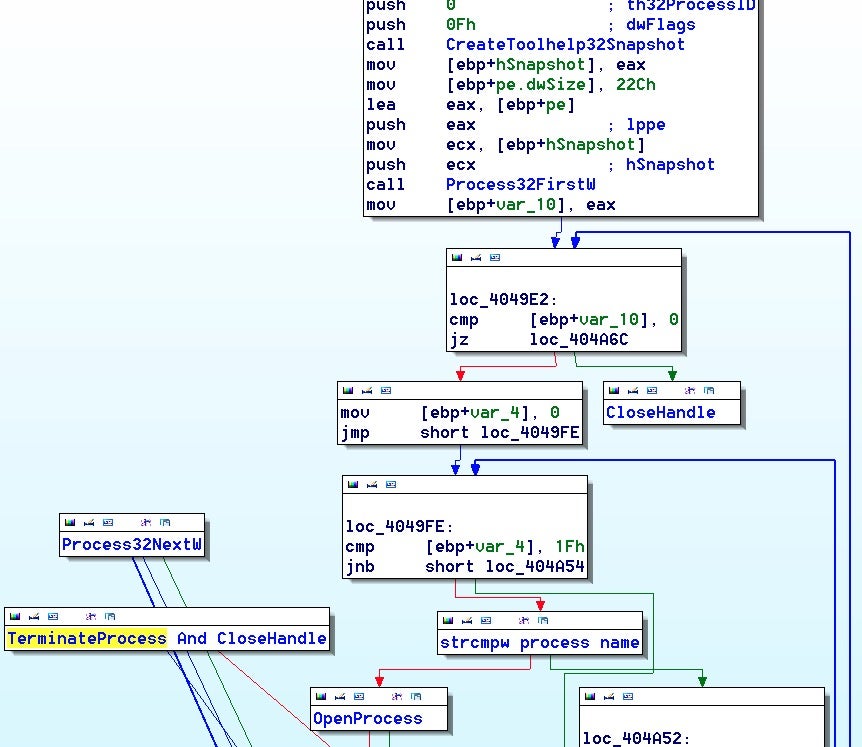
Also similar is the use of the Windows Restart Manager API to aid with process termination, which includes processes related to MS Office products and the popular gaming platform Steam.
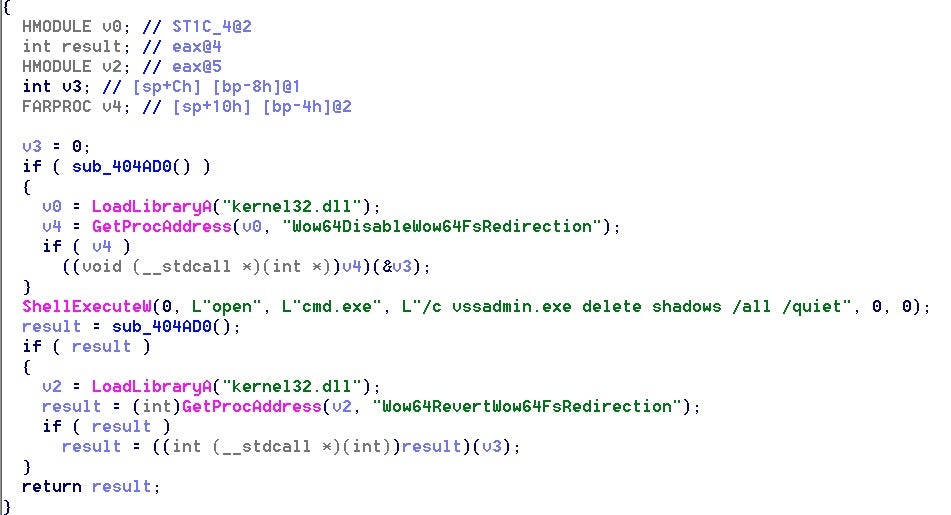
We also noted overlap with regards to some of the environmental checks and subsequent behaviors, including the removal of Volume Shadow Copies.
Both Babuk and Rook check if the sample is executed in a 64-bit OS, then delete the shadow volumes of the user machine. The code flows to Wow64DisableWow64FsRedirection to disable file system redirection before calling ShellExecuteW to delete shadow copies.
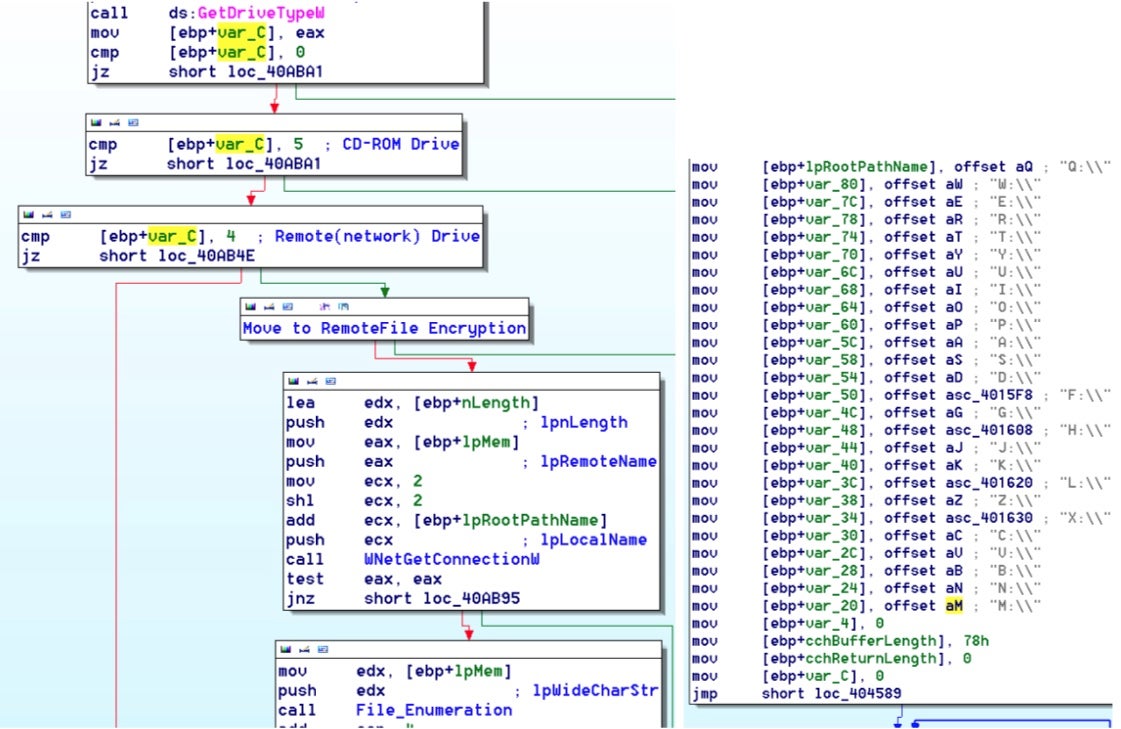
Babuk and Rook implement similar code for enumerating local drives. Rook checks for the local drives alphabetically as shown below.
The Rook Victim Website
Like other recent ransomware varieties, Rook embraces a dual-pronged extortion approach: an initial demand for payment to unlock encrypted files, followed by public threats via the operators’ website to leak exfiltrated data should the victim fail to comply with the ransom demand.

This TOR-based site is used to name victims and host any data should the victim decide not to cooperate. Rook also uses the site to openly boast of having the “latest vulnerability database” and “we can always penetrate the target system” as well as their desire for success: “We desperately need a lot of money”.
These statements appear under the heading of “why us?” and could be intended to attract affiliates as well as convince victims that they mean business.

At the time of writing, three companies have been listed on the Rook blog, spanning different industries.
Conclusion
Given the economics of ransomware – high reward for low risk – and the ready availability of source code from leaks like Babuk, it’s inevitable that the proliferation of new ransomware groups we’re seeing now is only going to continue. Rook may be here today and gone tomorrow, or it could stick around until the actors behind it decide they’ve had enough (or made enough), but what is certain is that Rook won’t be the last malware we see feeding off the leaked Babuk code.
Add that to the incentive provided by recent vulnerabilities such as log4j2 that can allow initial access without great technical skill, and enterprise security teams have a recipe for a busy year ahead. Prevention is critical, along with well-documented and tested DRP and BCP procedures. All SentinelOne customers are protected from Rook ransomware.
Indicators of Compromise
SHA1
104d9e31e34ba8517f701552594f1fc167550964
19ce538b2597da454abf835cff676c28b8eb66f7
36de7997949ac3b9b456023fb072b9a8cd84ade8
SHA256
f87be226e26e873275bde549539f70210ffe5e3a129448ae807a319cbdcf7789
c2d46d256b8f9490c9599eea11ecef19fde7d4fdd2dea93604cee3cea8e172ac
96f7df1c984c1753289600f7f373f3a98a4f09f82acc1be8ecfd5790763a355b
MITRE ATT&CK
T1027.002 – Obfuscated Files or Information: Software Packing
T1007 – System Service Discovery
T1059 – Command and Scripting Interpreter
TA0010 – Exfiltration
T1082 – System Information Discovery
T1490 – Inhibit System Recovery




